Cyberspace: A Real Digital Place
arkinoxAbstract: The nostr protocol combined with proof-of-work meta-protocols create a solid foundation for a functioning metaverse that is decentralized, permissionless, enables fair competition over scarce resources, and functions as an extension of reality by grounding all actions in thermodynamics. I call this metaverse cyberspace.
Notes and... Other Stuff
Nostr was expressly created as a decentralized protocol-level alternative to Twitter. But this protocol has incredible untapped potential to be much more than a micro-blogging replacement. Under the hood, nostr is a method of sending cryptographically signed and consistently structured JSON between clients (a user's device) and relays (basic servers) via instant websocket channels. If I publish a note, it takes the form of an event, and it goes to the relays I choose. If you subscribe to any one of those relays and you follow me, you see my note. It's that simple. And this simplicity has been a catalyst for hundreds of protocol enhancements (NIPs - nostr improvement possibilities) that have been contributed by an enthusiastic and diverse community to expand the capabilities of nostr. A good idea and a pull request on the github repo is all it takes to upgrade the nostr protocol and it happens almost every day.
At its core, nostr is a communication protocol. Anything that can be transmitted by text can be transmitted by nostr. Things that can't be transmitted by text such as audio and images can still be integrated with nostr by URL references. A text note containing a link to an image triggers most clients to load the image automatically; it is up to the client how they handle things like this.
The ability for anyone to create a client or relay and instantly connect to a rapidly expanding userbase demonstrates a powerful network effect. Users own their content and identity via a cryptographic keypair that allows them to sign into any nostr app and bring with them their entire nostr history of posts, friends, and settings. It really is a game changer.
In keeping with the original stated purpose of nostr, tens of clients already exist that create superb Twitter-like microblogging experiences. As incredible as it is that a protocol that started as a markdown document on a Github 2 years ago could spawn a dozen clients that arguably do a better job at being Twitter than Twitter itself, this is only the beginning of what we will see humanity do with nostr. We should not think of it as a Twitter replacement, but rather as a new base layer for decentralized, cryptographically-secure communication on the web.
As I learned more and more about the nostr protocol, there was something about it that felt familiar. I finally realized that it shared many fundamental properties with something I had read frequently about in science fiction: the metaverse.
What is a Metaverse?

Of course, if you turn to fiction for schematics and particulars you will find very little. If the author who imagined the tale knew how to build the things they wrote about, they might not need to sell any books. The metaverses I read about in "Snow Crash", "Ready Player One", and "Neuromancer" (to name my favorites) were all different and yet shared some compelling attributes:
- There are no competing metaverses.
- Everything is connected to it.
- Somewhere between most people and all people use it.
- People use the metaverse for entertainment, learning, communication, commerce, and crime.
- There are real-world consequences for actions taken in the metaverse.
- Nobody has full control over the metaverse.
These are interesting attributes because they raise some great questions that are conveniently never addressed in the narrative (perhaps only a developer such as I would care to ask). Regarding a metaverse with such striking attributes:
- Who hosts it?
- Who decides how it looks?
- Who owns the content?
- Who makes the rules?
- Who assigns the space?
- Who controls it?
To date no company in the real world has attempted to create a metaverse possessing all of these attributes. As far as the 6 questions above, any company that attempts to make a metaverse simply fills in their name as the answer to all.

What is the difference between a video game and a metaverse? Some may argue that the ability to interact in natural human ways in digital space might a metaverse make, but regardless of how innovative your motion tracking or holo-gramming is: if a single entity own and controls every aspect of the metaverse, aren't you just using an app?
I believe the most fundamental aspect of the metaverses depicted in fiction is that they are permissionless by nature. Unfortunately for any company trying to make the one metaverse to rule them all, it simply isn't possible to build a permissionless product if the company intends to retain any power, especially "moderation" power, over users. You can bet your private keys that no publicly traded company will loosen their grip on their users in such a radically liberating way, especially when monetizing the users' attention, activity, relationships, emotions, data, and time are the core business model under which so many companies operate.
On the other hand, an open protocol like nostr (with a little help from bitcoin) can answer the 6 questions above very satisfactorily. Regarding the metaverse:
- Who hosts it? nostr relays
- Who decides how it looks? nostr clients
- Who owns the content? users cryptographically own their content
- Who makes the rules? open source consensus
- Who assigns the space? an impartial algorithm + proof of work
- Who controls it? NOBODY
Ah, do you feel that? 🎯 That is when the lightbulb went on for me too. We have a metaverse in our midst, and it's called nostr.
Enter Cyberspace
When I realized this, I set to work on figuring out how I could visualize this dormant metaverse hidden within the nostr protocol. This is how I came up with ONOSENDAI. Named for the device of Japanese manufacture that allows one to connect their mind to cyberspace in the foundational sci-fi work "Neuromancer", ONOSENDAI is my proof of concept demonstrating that nostr indeed functions as a metaverse.
I refer to this particular nostr-metaverse as cyberspace for several reasons:
- "metaverse" is a bad word in many circles and has been tainted by spectacular failures and poor public opinion
- cyberspace is the original sci-fi term for what a metaverse is, and it's a cool retro word that people don't use much anymore so there is little baggage associated with it
- I distinguish between nostr as being the metaverse protocol and cyberspace as being an implementation of a meta-protocol on top of nostr which defines a particular metaverse based on proof-of-work. Theoretically, other metaverses could be built on top of nostr, but ONOSENDAI visualizes cyberspace.
The dream of the metaverse began as cyberspace, and so I find it fitting that as it crosses from dream to reality from the depths of the nascent nostr protocol, it be named in accordance with its predictors' wishes from some odd half-century ago.
"What is out there in cyberspace?" one may wonder. I wondered too as I stared at a black, empty screen. Initially my goal was to determine a way to visualize notes in 3D space. Notes are what most people would think of as tweets in Twitter. Notes are by far the most common kind of event on the nostr protocol since so many nostr clients act as Twitter-like microblogging apps. With unlimited notes at my disposal, I could easily fill the void of cyberspace by finding a way to put them into 3D space that made sense.
Initially I thought I could derive an X/Y/Z coordinate from the note's event ID which is a 256-bit hash. I could take the first 85 bits as the X coordinate, the 2nd 85 bits as the Y coordinate, and the 3rd 85 bits as the Z coordinate, which leaves 1 leftover bit (the least significant bit) that we simply ignore. However, this would mean that every event would essentially be located in a completely random location which isn't particularly useful nor interesting.
I then stumbled upon the idea of simhashing. A simhash is like a hash but instead of producing an extremely unpredictable 256-bit number for any given input, it will produce a very similar 256-bit number for similar inputs. This algorithm is used by Google to compare document similarities in their search engine.
I decided to simhash the content of each note and derive a coordinate from this in the same way by dividing it into 85-bit axis. I refer to this as the Semantic Coordinate System. The end result was quite compelling.

Clusters of notes have similar content, whereas unique notes are alone in the neon void of cyberspace. It doesn't particularly matter where a given note ends up; the notes near it are what make simhash clustering a special and interesting kind of visualization. I casually refer to this cloud of notes as "the vector of human discourse".

Organizing content in 3D space by this simple and impartial algorithm fits with the answer to question #5: Who assigns the space? an impartial algorithm + proof of work. No proof of work is involved with addressing notes, but simhash is a very impartial algorithm. It is so impartial that I found I was slightly dissatisfied with the similarity of some clusters of notes. However, the temptation to optimize the categorization based on content is a sheer cliff that will lead you straight into creating a biased algorithm for which there will be some method of optimizing, like Search Engine Optimization for websites which is so opaque and mysterious I can't help but think of anyone who specializes in it as snake oil salesmen. I want to avoid this kind of bias at all costs or else we will have failed to create a metaverse that is truly permissionless.
Let's review the attributes of sci-fi metaverses that I identified earlier:
- There are no competing metaverses.
- Everything is connected to it.
- Somewhere between most people and all people use it.
- People use the metaverse for entertainment, learning, communication, commerce, and crime.
- There are real-world consequences for actions taken in the metaverse.
- Nobody has full control over the metaverse.
We can safely ✅ check off several of these and mark some others as ⌛ pending:
- There are no competing metaverses. Time will tell on this.
- ✅ Everything is connected to it. Nostr is fully internet-native and can interoperate with pretty much anything. People have already used nostr to publish IOT events about when their smart dishwasher finished its cycle (and then someone started talking to the dishwasher in the replies. I saw it happen.)
- ⌛ Somewhere between most people and all people use it. If nostr ends up eating all other social platforms, it is safe to say that most people will likely use nostr; whether they will use cyberspace is uncertain, but large scale adoption of nostr bodes well.
- ⌛ People use the metaverse for entertainment, learning, communication, commerce, and crime. Once more capabilities are added into ONOSENDAI, all of these things will be possible.
- ⌛ There are real-world consequences for actions taken in the metaverse. This is called proof-of-work. More on this shortly.
- ✅ Nobody has full control over the metaverse. Nostr has this in spades.
This is pretty significant progress and we've only just begun. What else can we add to cyberspace besides notes, and what compelling reasons can we find to do so?
Taking The Path Untraveled

Ted Nelson is a man who ought not require any introduction, but for the youngins in the crowd, he is an early pioneer and contributor to the creation of the internet in the 1960s and has spent his life trying to liberate computing from the confines of facsimile. When humans invented computers, we invented a machine that can simulate reality, create whole new worlds, and visualize the impossible. And then what did we do? We filled our computers with digital facsimiles of literal paper and have been content with it ever since.
Why oh why! When we can do anything inside of our screens, why do we insist on stuffing everything into digital copies of physical things? Can you see how unimaginative this is? Can you see how, despite the relatively unlimited power of our devices, nobody has bothered to figure out something better than viewing linear digital sheets of paper on our devices?
An early demo of Meta's metaverse included a 3D office environment complete with cubicles that one was meant to experience in VR. It seems that the baseline human instinct is to copy reality into our computers without imagining anything new. Given how little creativity it takes to do this and how underwhelming the results are, I would claim that any amount of creativity applied to this problem is a step in the right direction, and a step in any direction at all is better than the status quo.
Ted Nelson is trying to get humanity to realize that copying reality verbatim into our machines is a waste of their potential, and while it will take effort and creativity to realize their full potential, it will be worth it in terms of the enrichment and productivity we will gain from it. Ted's hypothesis may or may not be true, but if we don't attempt to stray from the beaten path we will never know what possibilities await.
Ted has spent his entire life trying to get people to open their minds to a new way of consuming content. His project Xanadu, while it has struggled for decades and has yet to reach broad adoption, is a highly impressive expedition into the unexplored realm of possibilities for how humans might use computers to display media in a digital-native format. That is to say: if words on paper is the primitive format for physical communication, we as a species have yet to discover and utilize the fundamental primitive format for communication inside of our screens. This should be exciting to you!
I wax poetic and adjure you:
I think that the mission of Project Xanadu, while criminally underappreciated, is an incredibly worthwhile mission, and I sincerely hope that ONOSENDAI can help press forward into this unknown territory and spark new interest in this area of research.
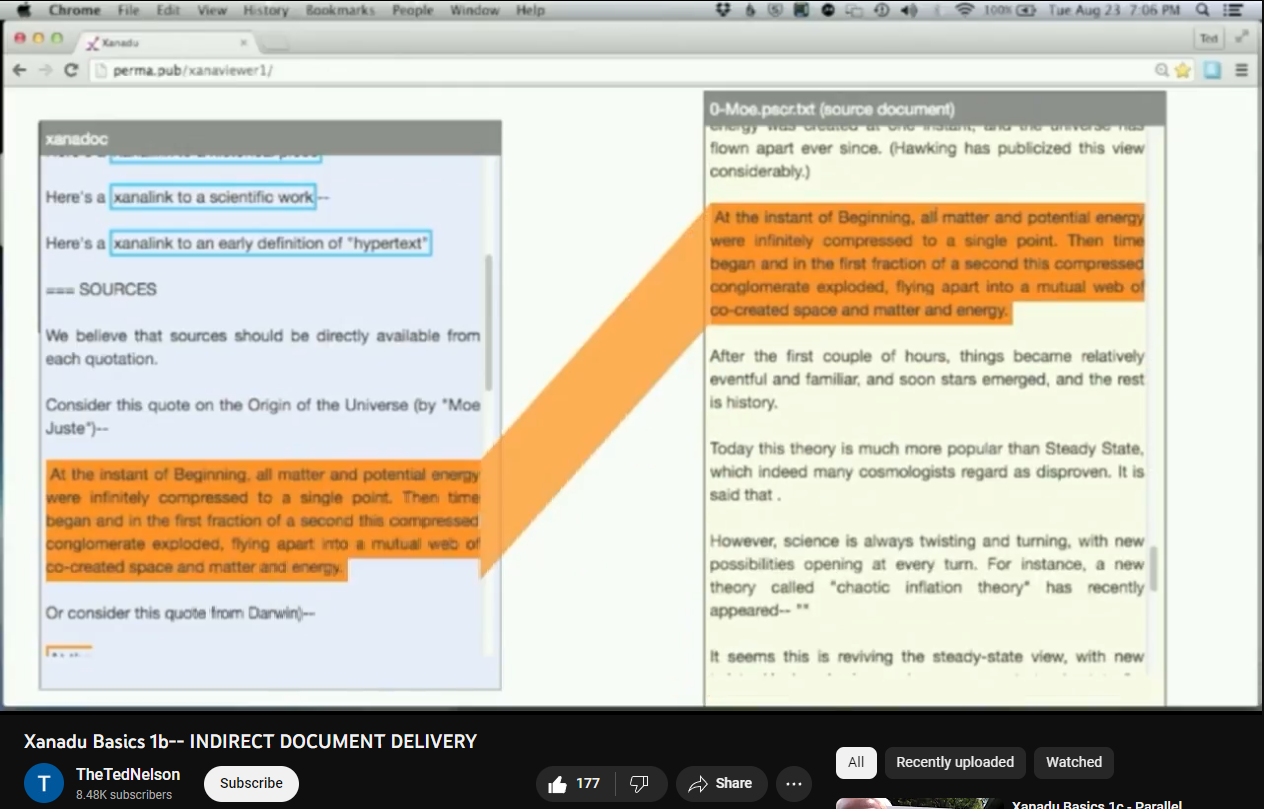
I would like to clarify that Ted Nelson does not eschew reality or physicality when it comes to visualizing digital media. In fact, one of his Xanadu prototypes uses a spatial document layout system that involves a sort of 3D space to organize documents. 3D space is what we live in. We are very instinctively familiar with it. But when we work with documents in reality, gravity and physics prevents us from fully utilizing 3D space. This is a clear advantage that digital reality has over physical reality, yet nobody seems to be utilizing it. Another profound idea from the Xanadu project is utilizing 2-way inline connections between fragments of content in separate documents and media. Imagine some text that visibly connects to a footnote or reference in a nearby document. Imagine a fragment of a video being pulled in and connected to a highlight in the paragraph you are reading. Ted's vision for the web is that we don't have to keep everything separate. It can be interconnected, multi-dimensional, and full of deep, rich context in a way that would seem foreign and perhaps even overwhelming to our linear-document conditioned minds.

What I would like to emphasize from all of this is that while copying reality verbatim seems to yield uninspired results that fail to reach the full potential of the digital medium, reality does contain great mechanics that the digital realm could benefit from such as 3D visualization, which is highly familiar and baked-in to human cognition. We understand 3D spaces. We live in them. Let's use them in the digital world too.
Another fundamental mechanic of our reality often taken for granted is that every action requires energy to overcome entropy. Entropy is the universal tendency for matter to break down, disperse, and reach equilibrium. Life defies this equilibrium by maintaining itself as a concentrated unit of warmth, nutrients, pressure, and energy, constantly struggling to exist separately from the universe. This struggle, which demands a continuous expenditure of thermodynamic energy, is what we call work.
Life Requires Proof-of-Work
In the physical world, energy expenditure is inherent to every action, so proof-of-work is self-evident. For example, movement requires energy to perform, so the movement itself is the proof of the work. However, digital systems operate in a realm of abstraction where logical operations are uncorrelated to real-world energy costs. Because of this, logical operations cannot serve as a basis for establishing consensus because they are fundamentally abstract, and the abstract cannot constrain the abstract. This is why hackers can grant themselves abstract power over your data with the right logical steps. Logic can always trump logic.
Proof-of-work, however, is technique to put thermodynamic constraints on abstract logical operations. Proof-of-work has been used to successfully secure the bitcoin network from abstract logical attacks since bitcoin's genesis in 2009. Before bitcoin, there was no significant known use for proof-of-work although it had already been invented and referred to by other names decades prior. At its core, proof-of-work relies on the concept of hashing, which is a logical operation that transforms an input into a fixed-size output. In proof-of-work systems, the objective is to find a hash output that falls within a certain predefined range. Since the output is unpredictable and cannot be determined without performing the hash, finding an output within the specified range serves as proof that an amount of work has been done. The smaller the range is, the more work must be done to find an output that is within it. The range is like a target that can change size. A more thorough primer on hashing is provided in the next section as some of its technicals are prerequisite to understand the meta-protocols proposed below.
The process of hashing requires an average expenditure of computational power proportional to the amount of work required, which in turn demands thermodynamic energy. As participants expend energy to perform the hashing process, the abstract logical operation they perform becomes connected to real-world energy costs. This connection transforms the digital process into a hybrid action that exists in both the physical and digital realms.
By incorporating proof-of-work, a digital system can be made consequential in the context of reality. Proof-of-work provides a fair, equitable, permissionless, and trustless mechanism for settling disagreements and competing for resources in the digital realm. Through energy expenditure, proof-of-work anchors cyberspace to the entropy of our universe, creating a digital extension of reality that is far more than just another 3D world.
Proof-of-work serves as a bridge between the abstract digital realm and the tangible physical world. By requiring participants to expend real-world energy to perform logical operations in cyberspace, proof-of-work creates a consequential digital environment that carries real-world value and consequences and enables trustless resolution of the custody of scarce resources. This unique fusion of the digital and the physical transforms cyberspace into a new kind of reality, one that is deeply interconnected with the fundamental laws of our universe.
Here are the ways in which I envision proof-of-work should be used to legitimize cyberspace as an extension of reality.
Constructing Cyberspace

An empty metaverse isn't a metaverse at all. In terms of first-principles, the real reason we need objects in cyberspace is because cyberspace is an analog to the real world and our lives are filled with objects and places. Without them, there is no sense of place, and therefore no analog.
Now that we have a valid reason beyond "it would be cool to have 3D stuff in cyberspace", how should one go about putting objects into the shared consensual hallucination and prevent them all from being universe-wide dicks?
You can probably guess by now: proof-of-work.
Proof-of-work is the process of repeatedly hashing some text with slight alterations to obtain an output hash that meets a certain criteria.
If you are unfamiliar with this process, here is a quick primer. Scroll down to PRIMER END /// if you are already familiar with how hashing works on a slightly more technical level.
PRIMER BEGIN ///
hash function: a mathematical function where you put in data and receive as the output a unique random-looking fixed-length number that deterministically relates to the input. Putting in the same data will always result in the same output number. Changing the input the slightest amount will change the output drastically such that it will be unrecognizable. Two different inputs should never produce the same output. The input cannot be determined by the output; it is a one-way process. The output cannot be known without performing the function on the input; this is the "work" in proof-of-work. SHA256 is the algorithm used for proof-of-work in bitcoin and cyberspace.
commitment: some data that specifies the output hash criteria and is fed into the hash function. If the resulting hash matches the criteria, then this serves as the "proof" in proof-of-work.
hashing: repeatedly altering the input data and putting it into a hash function to obtain different output hashes in hopes that one output hash will match the commitment criteria.
Commitment criteria often takes the form of a number of leading zeroes. For example, if a hash function outputs a random number 6 digits long: 583906, a commitment criteria could specify 2 leading zeroes for a valid proof, meaning that the hash must be 00xxxx, where x can be any number but the 0s must be on the far left. If the output hash matches this criteria, the proof-of-work is valid. The more specific the commitment criteria is, the more work (on average) it will take to find a hash that matches the criteria. Searching for a hash that matches 3 leading zeroes takes an exponentially higher amount of work that 2 leading zeroes. Of course, sometimes you get lucky and a hash matches much sooner than expected. Or, you get unlucky and it takes a lot longer than expected to find a matching hash. The point is that the hash function is balanced and has no exploits or shortcuts. Everyone who hashes must perform the same work for an equally likely, probabilistically fair result. The only advantage you can gain over me in publishing a 3D object at the same location is how much hashpower you have at your disposal.
PRIMER END ///
We can use proof-of-work to determine the coordinates and the bounding box size of our 3D object, which can be represented by a nostr event of kind 33333 whose content contains the 3D data of the object (in a particular format that I am working on). By default, publishing a 3D object with no proof-of-work will put it at a coordinate determined by the event ID which is an essentially random location, and having 0 proof-of-work will create a bounding box that limits the 3D object to a scale of 0 units, which is invisible. Womp womp. It would be advisable to apply at least some proof-of-work to your 33333 event or nobody will see it. And even then, in the future it is very likely that ONOSENDAI and other cyberspace clients will filter out all 3D objects under a certain proof-of-work threshold; this could even be set by the operator.
It is important to note that the enforcement of these rules relies on ONOSENDAI to consistently interpret the proof-of-work contained within the nostr event. Other theoretical cyberspace clients could interpret proof-of-work differently, resulting in a very different landscape in cyberspace. However, it is my hope that much like bitcoin, a network-wide consensus on how to interpret the proof-of-work for cyberspace will lead to a consistent experience across all cyberspace clients. This impartial algorithm + open source consensus is a nostr meta-protocol specifically designed for cyberspace.
A new type of commitment criteria I have specified for cyberspace is the coordinate commitment. A 255-bit string representing an X/Y/Z coordinate is specified in the commitment and the resulting hash, representing the event ID, is compared to the commitment (omitting the least significant bit from the event ID). The inverse Hamming distance between the commitment and result is the amount of valid proof of work, which determines the bounding box size for the 3D object. The X/Y/Z coordinates derived from the event ID are the coordinates of the 3D object. If the resulting coordinates are not desirable, the hash may be discarded and the hashing may continue. Note that this commitment scheme allows for a "good enough" result at the discretion of the creator; the proof is not invalidated if the amount of work is low.
Hamming distance: the number of differing positions between two strings of equal length, representing the number of changes required to transform one string into the other. An inverse Hamming distance is the string length minus the Hamming distance, which yields the similarity between the two strings.
Using proof-of-work to mine your event location and bounding box size means that you can have any real estate you want in cyberspace as long as you have the computing power to hash until you get those coordinates and desired level of proof-of-work.
I refer to these 3D objects as constructs because they represent something that takes work to build. By using proof of work to build constructs, we have a permissionless, chainless, tokenless way of fairly claiming real-estate in cyberspace grounded in real-world expense.
What if someone else publishes a construct on top of yours? Whoever has the highest proof of work is displayed and the other is hidden. This means that after you publish your construct, if you wish to defend your property, you should continue to hash larger amounts of work and be ready to publish it if and when your property is ever vandalized by someone. In this way, nobody can lay claim to a space forever, all space is scarce, and all space is tied to real-world costs.
I'd like to highlight for the reader that the connection to real world costs is the heart of this article and the core concept behind cyberspace. Unlike all other 3D worlds, cyberspace will be the first digital world that not only has a cost to participate in but requires you to pay that cost to the universe as entropy in a completely fair, completely neutral protocol. It incentivizes a hash-powered arms race to secure and maintain property. This cyber real estate, while vast, is ultimately finite and temporary as people use thermodynamic force to contest and acquire a space for themselves.
Now that we have a conceptual basis for proof-of-work derived constructs in cyberspace, we ought to consider how people might interact with them. This will provide some insight as to why it would be beneficial for one to maintain a construct by expending energy in perpetual defense of it. It will also elucidate what role proof-of-work plays in interpersonal interactions in cyberspace.
Billions of Legitimate Operators

We've talked about the structures. Now let's talk about the people.
I refer to cyberspace users as operators (thanks for the cool nomenclature, William Gibson), and operators can be humans or AIs (like ChatGPT) that control a Presence in cyberspace.
A Presence is your avatar, which can be customized and moved around cyberspace. More on movement below.
In nostr, you can publish a kind 0 event that contains metadata about you: a profile picture, a banner image, a Lightning Network payment address, and a NIP-05 identifier. This is where we would save a reference to an avatar URI or something along those lines; I haven't tackled this yet.
The NIP-05 identifier looks like this: arkinox@arkinox.tech
If you don't know how to manage your own web server, there are many nostr identity services that you can pay via Lightning to receive NIP-05 identity. Having a NIP-05 identity is a form of soft verification that makes you appear more legitimate on Twitter-like nostr clients.
In ONOSENDAI, NIP-05 identities will be simhashed to create home coordinates in the Semantic Coordinate System for every operator. This means that when the operator first brings their identity into ONOSENDAI (or when they get killed... more on that later) they will start at their home coordinates in cyberspace.
This means that large identity servers like nostrplebs.com will have thousands of operators with their home coordinate (or spawn location) clustered together in cyberspace, because every NIP-05 ends with the same suffix: someone@nostrplebs.com.
These clusters are places that will become hot real estate. Constructs positioned near NIP-05 clusters will have instant high-visibility. But attaining that real-estate will require some serious proof-of-work!
To maintain the valuable properties of cyberspace, proof-of-work is required for operators to interact with cyberspace.
Movement
When an operator wants to move, they must publish a Drift event of kind 333 with a minimum of 1 unit of NIP-13 proof-of-work. The event must contain their current coordinate. The publishing of this event will award the operator with acceleration equal to their valid proof-of-work from their coordinate.
To ensure that operators cannot easily lie about their location (and wield omnipresence) the Drift event must also contain an e tag referencing their most recent 333 event by ID. The previous 333 event's coordinate plus acceleration (proof-of-work) can be checked to verify that it would yield the current 333 event's coordinate. If they do not match, or if the current 333 event does not reference the most recent 333 event, the operator's movement chain is broken and their location can be considered invalid.
The ONOSENDAI client (and other cyberspace clients) should be incapable of publishing invalid movement chains, so an invalid movement chain would indicate foul play.
There are consequences for breaking your movement chain. The tip of a movement chain is susceptible to Derezz attacks from other operators. Normally the tip of your movement chain is where you are currently located, but if you break your movement chain, your last valid coordinate in the chain will remain vulnerable to a Derezz attack regardless of your current location. A new Derezz attack will have to contain sufficient proof-of-work to reach far enough into the past to affect your last valid move; if the move is far in the past, it is very unlikely that anyone will attempt to reach it. But if it is recent, you remain quite vulnerable. Derezz is discussed below.
Aggression
Derezz is an event kind 86 that represents an attempt to kill another operator. A successful Derezz will teleport the victim back to their home coordinate and nullify all of their proof-of-work events to date including Armor, Vortex, Bubble, Drift, and Stealth. Constructs are not affected by Derezz.
An attacker generates NIP-13 proof-of-work on a kind 86 event that contains the victim's pubkey (only 1 target allowed), an e tag to the victim's latest movement chain event, and an e tag referencing the tip of the attacker's movement chain.
These attributes not only allow for anyone to independently verify the validity of the attack, but also requires that the POW for the attack be generated at the time of the attack and not beforehand.
The proof-of-work of the event determines the range and power of the attack. For example, if the proof-of-work was 10 and the victim was 7 units distance away from the attacker, the victim would be attacked with a Derezz of strength 3 (3 Derezz). If the victim was 2 units distance away from the attacker, they would receive 8 Derezz.
1 unit of Derezz is enough to Derezz an operator. However, an operator can generate proof-of-work Armor to defend themselves from a Derezz attack in advance, and the Armor's proof-of-work value is subtracted from the Derezz attack's value to determine if the operator succumbs to the attack. More on Armor below.
Defenders have an asymmetric advantage against attackers because they can generate an unbounded amount of proof-of-work in advance of being attacked. Because of this, there is another tool that attackers can use to their advantage.
Vortex is an event kind 88 that represents the creation of a constant gravitational force that pulls a victim toward it. A vortex can be used to immobilize a victim while the attacker generates higher amounts of proof-of-work for a successful and easier Derezz kill. The Vortex event must contain the same tags and contents as a Derezz event, except it may also contain a coordinate where the vortex should appear. Unlike Derezz, Vortex does not require the attacker to be physically near the location of the Vortex they create. The range and force of attraction is relative to the proof-of-work for the event and the distance to the victim. If the Vortex's proof-of-work is 10 and the victim is 7 units away from it, 3 units of acceleration are applied to pull the victim toward the center. The victim has 3 options: escape velocity via higher movement proof-of-work, publish a deactivation event to counter the Vortex with equal or higher proof-of-work, or Derezz the attacker (which nullifies all their Votrices and other proof-of-work). The counter event (kind 89) must contain a tag to the event ID of the original vortex and meet or exceed the original proof-of-work. The Vortex will persist indefinitely until countered or the owner killed. Each Vortex may only target 1 pubkey.
Defense
Armor is an event kind 10087 that simply publishes proof-of-work as an offset to any incoming Derezz attacks. As long as the Armor proof-of-work is greater than or equal to any incoming Derezz attack, the defending operator will survive the attack. Operators ought to generate proof-of-work armor before they need it or they will be vulnerable to sudden attacks. If the operator succumbs to a Derezz attack, their previous Armor is invalidated.
Stealth
The state of the nostr network does not reflect whether an operator is actively controlling their Presence or not. Your latest Drift event determines where you are located. If you close ONOSENDAI, other operators will still see you in that location and you are still vulnerable to attack. Therefore, it is important to be able to conceal one's location so that when the human controller is not present the operator is less vulnerable.
Stealth is an event kind 10085 that simply publishes proof-of-work to define a stealth boundary. Each unit of proof-of-work results in a stealth radius = 4096 / (POW+1). A smaller stealth radius is better. 4096 is the length of 1 sector.
When an operator has published a valid Stealth event, they may publish their Drift events differently without breaking their movement chain. Instead of publishing their coordinates directly in the Drift event, they may publish a zk-snark that will only reveal their coordinates if the input to the zk-snark is a coordinate within the boundary radius. This is called a Stealth Drift event.
Someone hunting this stealth operator may see their Stealth Drift events and input their own coordinates into the zk-snark. If they are not within the stealth boundary radius, they will simply receive a rejection. If they are within the stealth boundary radius, they will receive the actual coordinates of the operator.
Having a sufficiently small stealth boundary (high Stealth proof-of-work) will make it computationally infeasible for even a malicious actor to abuse your zk-snark by trying to brute-force it with random coordinates outside of ONOSENDAI. Of course, they can use your prior movement chain to try and guess where you may have gone or how far you moved since your last clear broadcast of your coordinates, but this can be very difficult if your movement chain has a lot of Stealth Drift events.
Another tip is to not have enemies ✌
Either way, once you've cloaked yourself, it's much harder for you to get got while you're AFK.
PS - logging out at your home coordinate isn't a great idea unless you have nothing to lose!
Communication
Operators may publish a Shout event of kind 20333 (ephemeral) with proof-of-work to broadcast a public message to nearby operators. The more proof-of-work the event has, the larger the broadcast radius. The event must reference in its e tag the tip of the Shouting operator's movement chain; this is the coordinate from which the Shout emanates. Operators will ignore Shouts whose radius they do not fall within.
The Shout may have an optional parameter to be broadcast as voice or text. Text shouts show up in a chat box on the interface, while voice Shouts will be heard via text-to-speech engines built into the web browser. This, of course, can be muted globally on the receiving operator's interface, which will force the speech to the text chat box.
ONOSENDAI will have optional speech-to-text via the web browser too so that a human controller can speak naturally to broadcast a Shout without typing.
Securing Property
Securing one's property is a human right, and so it is necessary to provide tools for operators to constrain the movement of other operators in defense of their cyber property.
Bubble is an event kind 90 that represents the creation of a constant anti-gravitational force that pushes an aggressor away from it. It functions as the exact opposite to a Vortex. A Bubble can be used to force a victim away from a central origin point. The Bubble event must contain the same tags and contents as a Vortex event, including a coordinate where the Bubble should appear. Like Vortex, Bubble does not require its creator to be physically near the location of the Bubble they create. The range and force of repulsion is not relative to the proof-of-work for the event and the distance to the aggressor. If the Bubble's proof-of-work is 10 and the aggressor is 7 units away from it, 10 units of acceleration are applied to push the aggressor away from the center. The aggressor has 3 options: intrusion velocity via higher movement proof-of-work, publish a deactivation event to counter the Bubble with equal or higher proof-of-work, or Derezz the Bubble creator (which nullifies all their Bubbles and other proof-of-work). The counter event (kind 91) must contain a tag to the event ID of the original Bubble and meet or exceed the original proof-of-work. The Bubble will persist indefinitely until countered or the owner killed. Each Bubble may only target 1 pubkey.
Monetizing Property
If you haven't experienced the magic of zaps, it really is nostr's killer feature. Using the Lightning Network, you can send micro amounts of bitcoin instantly from your lightning wallet to any user or note you see on most major nostr clients. If you don't have a lightning wallet, you can easily get one and a zappable lightning address from a custodian like Alby at getalby.com.
Likewise in cyberspace, constructs themselves will be zappable but will also support zappable sub-meshes, meaning you can make little zappable objects inside of your constuct. So, imagine a store in cyberspace where the goods can be zapped to purchase them. Likewise, operators and notes will have the ability to be zapped too.
If you can set up a storefront and receive instantly settled payments without having to physically be present, that's pretty cool right? The buyer could receive an encrypted direct nostr message as soon as they zap what they want with the download link or access code.
You may think "Yeah but on online store can do that too."
- Unless you are running BTCPay Server, you probably are running a centralized store that can be censored.
- Unless you are running BTCPay Server, you probably can't accept bitcoin into self custody directly from your shop.
- A store in cyberspace is like a physical shop in that you can meet and interact other patrons and shopkeepers without geographical restrictions.
- Zaps are not only instantly settled payments, but a social indicator of quality and can be publicly totaled to show an item's popularity.
Max Webster made a very compelling point about zaps. Bitcoin is the only absolutely scarce resource in reality who's issuance is known. Content, on the other hand, will continue to scale infinitely and exponentially. In a sea, nay - universe of content produced by humanity, bitcoin will be an essential signaling feature to elevate what is worthwhile above what is not. In an abundant future with nearly infinite options of how to spend your time and money, being able to see how others have spent their time and money will be a literal life saver (in terms of amount of time of your life saved).
Zaps are an incredibly powerful nostr feature that combines instant decentralized communication with instant decentralized payments, and cyberspace turns it into a whole new medium of connection.
Other yet unimagined monetization strategies and use-cases will undoubtedly emerge for constructs and cyberspace in general. The Lightning Network, for example, is an evolution of the bitcoin protocol that couldn't have been imagined in 2009 but has brought critical, colossal, and continually emerging benefits to the original bitcoin network and humanity as a whole. As the cyberspace meta-protocol and its underlying nostr protocol grows, I hope that humanity is able to extrude reality into cyberspace to enable productivity and cooperation on a scale unseen in human history.
I strongly believe that the fundamental properties of nostr and proof-of-work are absolutely fundamental to building a metaverse that is more than a gimmick. Cyberspace has the potential to be a meaningful extension of reality and I hope it gives humanity room to grow.
Coming Soon
I haven't implemented all of the discussed features yet in ONOSENDAI but I'm working on it as fast as I can. I felt as though it was important to establish a strong conceptual basis for a proof-of-work-anchored digital world before I began implementing features.
I'd appreciate feedback on this article to refine and improve my cyberspace client implementation.
If you'd like to financially support development, please get in touch! I am looking for opportunities to pursue cyberspace development full-time.
Try it out at https://onosendai.tech
Github: https://github.com/arkin0x/ONOSENDAI
Telegram: https://t.me/ONOSENDAITECH
Geyser: https://geyser.fund/project/onosendai
npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
arkinox@arkinox.tech