Coding For Penetration Testers

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Coding For Penetration Testers
Deliver to
Russian Federation
Don't Change
Change Address
Books
›
Computers & Technology
›
Programming
Coding for Penetration Testers: Building Better Tools
1st Edition
Qty:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
Qty: 1
Coding for Penetration Testers: Building Better Tools
$49.95
(11)
Available to ship in 1-2 days.
Customers who viewed this item also viewed
Page 1 of 1 Start over Page 1 of 1
Coding for Penetration Testers: Building Better Tools
Page 1 of 1 Start over Page 1 of 1
Hacking: The Art of Exploitation, 2nd Edition
The Hacker Playbook 3: Practical Guide To Penetration Testing
Hands on Hacking: Become an Expert at Next Gen Penetration Testing and Purple Teaming
Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws
System Design Interview – An insider's guide, Second Edition
Customers who bought this item also bought
Page 1 of 1 Start over Page 1 of 1
Hacking: The Art of Exploitation, 2nd Edition
Publisher
:
Syngress; 1st edition (October 7, 2011)
Language
:
English
Paperback
:
320 pages
ISBN-10
:
1597497290
ISBN-13
:
978-1597497299
Item Weight
:
1.43 pounds
Dimensions
:
7.5 x 0.73 x 9.25 inches
Help others learn more about this product by uploading a video!
Top reviews
Most recent
Top reviews
Good but think of the first part of the book as just an introduction to python
Absolute junk, the code and links do not work and the book is poorly written.
You can't write a book like this and have it be interesting, but it had good examples and easy to follow steps.
I expected a bit more depth. High level overviews of a few scripting languages with examples that are pen-test/information gathering focused. Touches on exploit code. If you are looking to begin pen-testing and have a solid understanding of tcp/ip this is a great book.
I have to say this has been the biggest disappointment of all security-related books that I ever purchased (there were dozens). It should be named "A quick glance at a few scripting languages". To give an example, Python is mentioned on 33 pages (that includes a few pages for scapy) where you'll be shown how to (hold your breath) send an ICMP packet. (I will not talk about PEP8 here). To drill a bit further, the chapter about Python lists is about (wait for it) - bitwise operations. Lists are only mentioned as a way of storing data for the given example which shows how you can use Python to calculate net & broadcast address from a CIDR notation (why would you want to use lists for that?). There is no meaningful mention of list indexing or slicing. The chapter about Python exceptions is just appaling. There is no explanation of "why" anywhere, just "what" and a little bit of "how". Also, no hint on where to look for further information. Real beginners might find this book interesting for getting a basic idea of how are scripting languages used (bash, Python, Perl, Ruby and PowerShell all get a really quick intro). But then they would get really confused towards the end of the book when they suddenly find authors throwing shellcode at vulnerable FTP server and using some terms that are mentioned very briefly: "EIP is called the Instruction pointer", "ESP points to stack area where you can see the stack", "as you can see, the EIP is now overwritten with 41414141 so the server is vulnerable". Is any beginner expected to understand this? I'm really struggling to see who is the intended audience. It does not give any explanation to beginners and is way too shallow for any penetration tester.
This has been a really helpful book to me in learning to make some use of new scripting tools in more useful directions. I have a bit of python right now, but having examples of how these languages can be used across several different languages is really useful. Some of the book is still a bit over my head, but I sure feel like I'm starting to get there. Great read and some good excercises to make the examples even better. I'm hoping they'll do a second book and keep going with other languages.
Face it, there are technologies you are master of and others which find you lacking. Yet in pentesting, you are expected to be master of all things you encounter. Coding for Penetration Testers is one of those rare books that no matter your current status, can help you get better. The author takes you on a walk through multiple languages including shell scripting for both Windows and *nix platforms, Ruby, python, and more. This book can help refresh concepts you may have forgotten on rarely used platforms, teach new techniques for solving challenging problems, and enable you to be the professional tester you want to be. Further, the languages covered are the same languages which power some of the most common open source tools and enable you to customize those tools to generate more accurate and productive results. I highly recommend this become required reading for every tester on your team.
Pages with related products.
See and discover other items: web testing , python data science , python data , python for data science , security coding
"This book is definitely not for rookie coders, but rather a good starting point for people with a medium level of programming experience. It is also not suited well as a reference to quickly look things up in. But if what you’re looking for is a very practical guide with tons of pointers to further (and recommended) reading material and exercises Coding for Penetration Testers delivers what it promises." --Computers and Security
"Penetration testing is a profession that requires the mastery of dozens of tools; every job poses challenges that require these tools to be mixed, matched, and automated. The master penetration tester not only excels at using his or her toolbox, but also expands it with custom scripts and unique programs to solve the challenge of the day. This book provides a solid introduction to custom scripting and tool development, using multiple languages, with a penetration tester's goals in mind. This background can transform penetration testing from a manual, often repetitive task, to an efficient process that is not just faster, but also more accurate and consistent across large engagements."-- HD Moore, Metasploit Founder and CSO of Rapid7
"Penetration testing requires that the tester understand the target as much as possible, and know how to perform various attacks while being as efficient as possible. Having the skill set to create and use a variety of scripts increases the penetration tester's efficiency and elevates him or her from the script kiddie to the professional realm. Ryan Linn and Jason Andress have created a guide that explores and introduces the techniques that are necessary to build the scripts used during a test. No matter the platform, this book provides the information required to learn scripting and become a world-class penetration tester. This is definitely a book that will remain close at hand for every test I perform!"-- Kevin Johnson, Senior Consultant, Secure Ideas
"At 175 pages, the book does not kill many trees, but does give the reader an overview of all of the key principles around information security…For those looking to get their feet wet in the deep waters of information security, The Basics of Information Security: Understanding the Fundamentals of InfoSec in Theory and Practice is a great place to start."-- RSAConference.com
"Overall this is an excellent book, which offers some clear and effective tutorials on the different languages and on efficient and effective penetration testing. It’s highly recommended for any testers who want to broaden their skills and move to the next level." --BCS.org
Learn how to create custom penetration testing tools using a wide variety of development languages!
Coding for Penetration Testers : Building Better Tools: Andress, Jason...
Coding for Penetration Testers | Request PDF
Coding for Penetration Testers - 2nd Edition
40 Best Penetration Testing (Pen Test ) Vapt Tools in 2021
GitHub - wtsxDev/ Penetration - Testing : List of awesome penetration ...
To read the full-text of this research, you can request a copy directly from the authors.
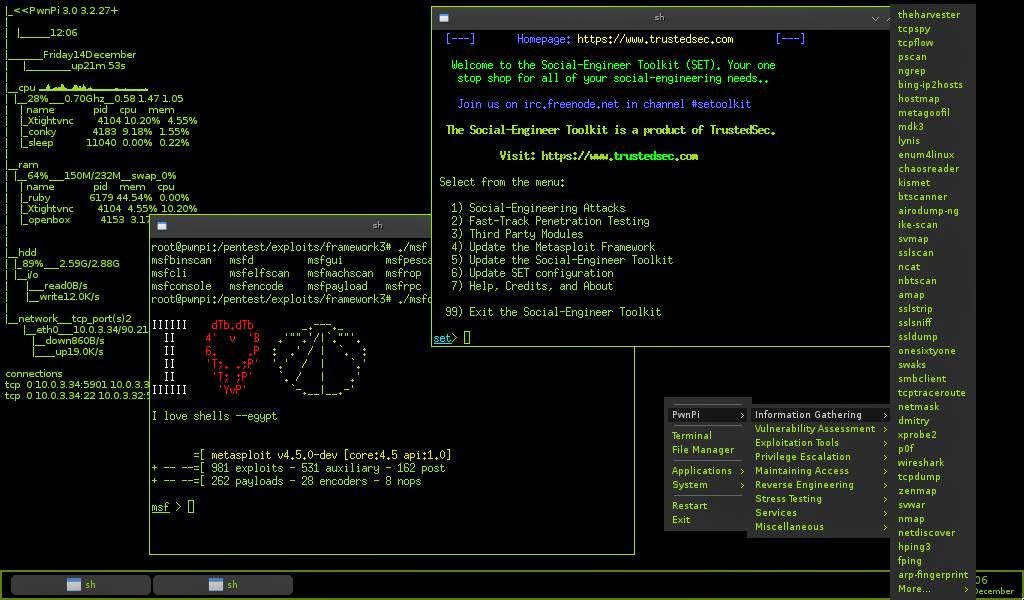
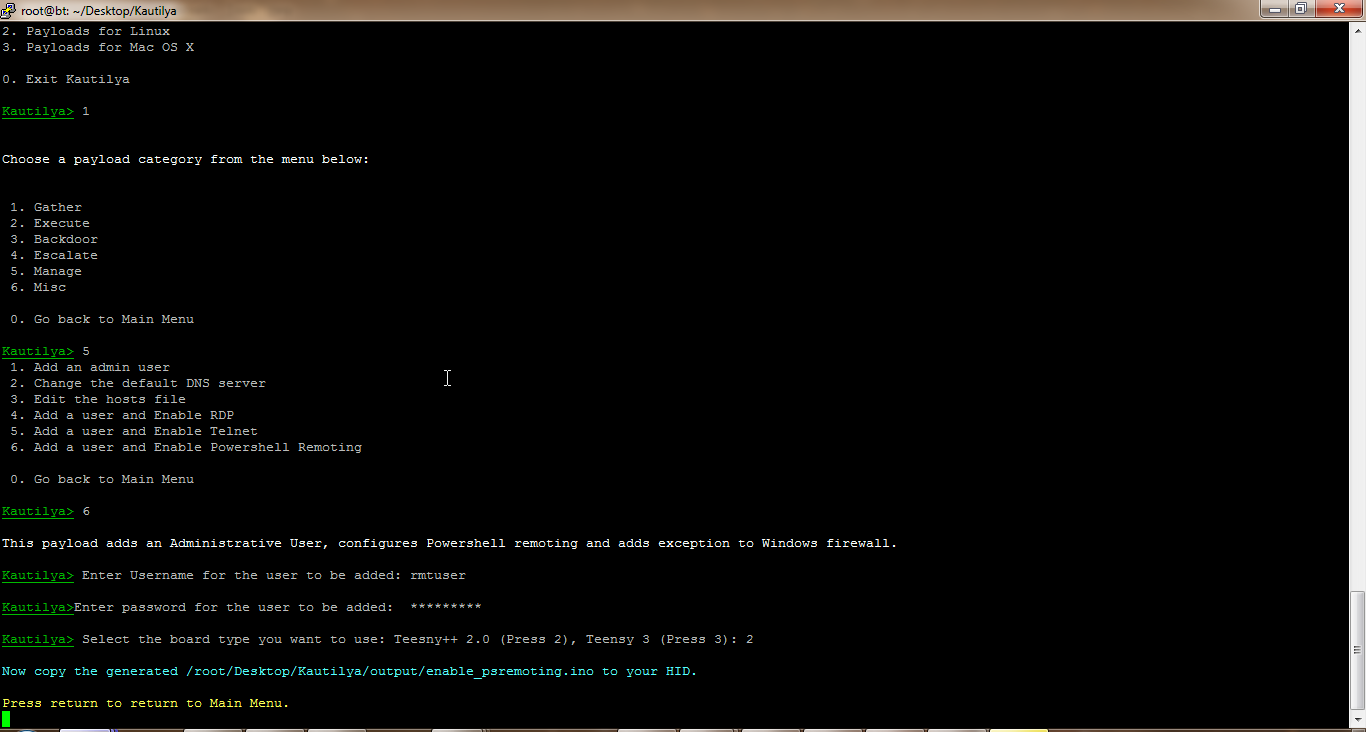
Tools used for penetration testing are often purchased off-the-shelf. Each tool is based on a programming language like Perl, JavaScript, Python, etc. If a penetration tester wants the tool to perform a test differently than the off-the-shelf configuration, he or she must know the basics of coding for the related programming language. Coding for Penetration Testers provides the reader an understanding of the scripting languages that are in common use when developing tools for penetration testing. The book also guides the reader through specific examples of custom tool development and the situations in which such tools might be used. Most books currently available that discuss penetration testing tool creation cover the topic as an aside to a general programming discussion or talk about it from a very specific focus, such as one particular language. Discusses the use of various scripting languages in penetration testing Walks the reader through building custom penetration testing tools Demonstrates how custom tools can be put to use in penetration testing.
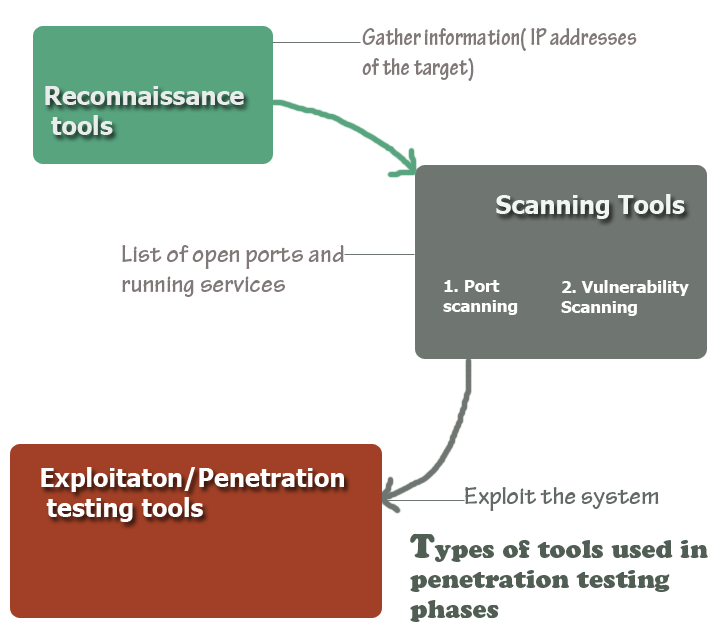
... The penetration testing process in divided in several phases: target scoping, information gathering, target discovery, enumeration target, vulnerability mapping, social engineering, target exploitation, privilege escalation, maintaining access, documentation and reporting [3] . These phases are used entirely in a black-box type, while in white-box the phases such as target scoping, information gathering and target discovery may be omitted, because of the fact that the white-hat auditor has prior knowledge about the system that shall be tested. ...
... what dictionary do you want to use? [1] default dictionary file 'pentest/database/sqlmap/txt/ wordlist.txt' (press Enter) [2] custom dictionary file [3] file with list of dictionary files > To this question we answer with choosing the first option. And the last question that is asked from SQLMap is: do you want to use common password suffixes? ...
Penetration testing on a website is discussed in this paper, in order to discover security vulnerabilities that may exist. The test is performed against a library CMS website, hosted in the same LAN with the attacker machine. The website is implemented using PHP and MySQL database, whereas sophisticated tools from the BackTrack 5 R3 Operating System are used for testing purposes. In addition to discovered vulnerabilities, some suggestions on improving website security are considered, as well.
Online learning platforms are becoming increasingly popular in engineering education. Through combining the educational form of online learning with laboratory information management systems (LIMS), we can integrate the education and management functions into one system. The purpose of this study is to develop a collaborative education and management system for the water hydraulic laboratory based on the Hypertext Preprocessor (PHP) scripting language. The system provides a convenient and multifunctional education and management platform for students and teachers throughout the whole experiment courses. Additionally, the B/S (Brower/Server) structure based on the Model-View-Controller (MVC) model was used in our system. The key steps of developing the WathyLab system were described, and the practical application subjects regarding water hydraulic materials were illustrated. The paper ends with an evaluation of this system according to the questionnaire survey. The students’ attitudes were surveyed and analyzed. Results showed that the proposed system can lead to better education effectiveness and learning efficiency.
In this paper, we describe penetration testing, as a methodology for information security. Pentesting is used for proactive defence and information systems protection. Special operational systems on UNIX core, developed scripts, utilities and applications are suggested. Most pros and cons of manual and automated pentest are given.
With increasing world-wide connectivity of Information systems, and growth in accessibility of data resources, the threat to the Integrity and Confidentiality of Data and Services has also increased. Every now and then cases of Hacking and Exploitation are being observed. So in order to remain immune and minimize such threats, the Organizations conduct regular Vulnerability Assessment and Penetration Testing (VAPT) on their Technical Assets [1]. We at IDRBT have developed a new automated VAPT Testing Tool named Net-Nirikshak 1.0 which will help the Organizations to assess their Application/Services and analyze their Security Posture. Net-Nirikshak 1.0 detects the vulnerabilities based on the applications and Services being used on the target system. Apart from these it detects the SQL Injection vulnerabilities and reports all the Identified vulnerable links on the Target. Further the tool can also exploit the identified SQLI vulnerable links and grab confidential information from Target.The automated VAPT report generated by the tool is sent to the specified Email and all the traces of Scan along with the Report are removed from the Hard disk so as to ensure the Confidentiality of the VAPT Report. All the Technical and Operational aspects of Net-Nirikshak 1.0 are described in this paper along with the Outputs of a sample VAPT Test conducted on www.webscantest.com using Net-Nirikshak 1.0
July 2008 · Journal of Physics Conference Series
We discuss the rapid development of a large scale data discovery service for the CMS experiment using modern AJAX techniques and the Python language. To implement a flexible interface capable of accommodating several different versions of the DBS database, we used a 'stack' approach. Asynchronous JavaScript and XML (AJAX) together with an SQL abstraction layer, template engine, code generation ... [Show full abstract] tool and dynamic queries provide powerful tools for constructing interactive interfaces to large amounts of data. We show how the use of these tools, with rapid development in a modern scripting language, improved the scalability and usability of the the search interface for different user communities.
With the increasing popularity of the World Wide Web, scripting languages and other dynamic languages are currently experiencing a renaissance. A whole new genera-tion of programmers are growing up with languages such as JavaScript, Perl, PHP, Python and Ruby. The attention that dynamic languages are receiving is remarkable, and is something that has not occurred since the early days of personal ... [Show full abstract] computers and the BASIC programming language in the late 1970s and early 1980s. At the same time, the web is becoming the de facto target platform for advanced soft-ware applications, including social networking systems, games, productivity applica-tions, and so on. Software systems that were conventionally written using static programming languages such as C, C++ or Java™, are now built with dynamic lan-guages that were originally designed for scripting rather than full-scale application development.
Perhaps the most time-consuming process when developing in any programming language is that of testing and debugging your code. With professional-grade code it becomes of the utmost importance to make sure that what you create is fully tested, verifiable, and bug-free. One aspect that makes JavaScript so different from other programming languages is that it isn’t owned or backed by any one ... [Show full abstract] company or organization (unlike C#, PHP, Perl, Python, or Java). This difference can make it challenging to have a consistent base with which you can test and debug your code.
Several image manipulation tools support the use of at least one general scripting language (e.g., Python, JavaScript), for task automation. But, users of such tools usually do not have much experience or skill with these (or often any) programming languages, which represents a barrier for the use of such languages when automating a task. With this in mind, we present IML, a work-in-progress, ... [Show full abstract] domain-specific language designed for easy and clear image manipulation. Besides describing the basic constructs and operations of this language, we compared a simple IML program with equivalent implementations in the languages currently supported by the popular image manipulation tool GIMP. This illustrates how IML might make the image editing automation process simpler, easier to learn, and more straightforward.
SWIG (Simplified Wrapper and Interface Generator) is a freely available tool that integrates Perl, Python, Tcl, and other scripting languages with programs written in C, C++, and Objective-C. This paper provides an introduction to SWIG and shows how it can be used to construct Perl extension modules. In addition, a number of applications in which SWIG has been utilized are described. While SWIG ... [Show full abstract] is similar to other Perl extension building tools such as xsubpp and h2xs, SWIG has a number of unique features that help simplify the task of creating Perl extension modules. Many of these features are described as well as limitations and future directions. This paper is primarily intended for developers who are interested in combining Perl with applications written in C or C++ as well as current SWIG users who are interested in learning more about some of SWIG's advanced features.
January 2010 · International Journal of Computer Applications
Digital Content Creation (DCC) Applications (e.g. Blender, Autodesk 3ds Max) have long been used for the creation and editing of digital content. Due to current advancement in the field, the need for controlled automated work forced these applications to add support for small programming languages that gave power to artists without diving into many details. With time these languages developed ... [Show full abstract] into more mature languages and were used for more complex tasks (driving physics simulations, controlling particle systems, or even game engines). For long, these languages have been interpreted, embedded within the applications, lagging the UIs or incomparable with real programming languages (regarding Completeness, Expressiveness, Extensibility and Abstractions). Two approaches were used to implement those languages. Either build them from scratch (like MaxScript), or use an existing popular language and write a set of extensions to it and embed it (like Blender and Python). In practice, both those solutions suffer, the first method produces languages lacking being real, competitive languages and generally very inefficient, the second method has problems arising from not being dedicated in first place for that kind of applications so, they lack expressiveness facilities (like dedicated constructs) that support that particular domain, also it's very hard to optimize these languages for specific DCC situations.
August 1998 · Computers & Geosciences
The hypertext mark-up language (HTML) is used to create hypertext documents in use on the World-Wide Web (WWW), built up as a client/server model. In this paper we discuss the enhancement of HTML documents with JavaScript, a script language understood by most common browsers. JavaScript is considered an easy means for bringing interactivity and answer checking to educational Web pages. It is ... [Show full abstract] faster to learn compared to using a programming language like PERL and has the advantage of high portability between different operating systems. Because all actions are performed on the client side, it reduces net traffic and pages can be used off-line. Educational usage, including tests and operations in future distance learning are outlined. Examples of JavaScript supported documents are given using clay mineralogy and knowledge-based tests as examples. A critical review of this relatively new technology reveals some compatibility problems but these seem to be offset by the possibility to make Web pages more attractive.
There are a number of popular programming languages these days. Different companies, even different departments within the same company, prefer to use different languages. Driver developers get used to writing code in C. Many programmers who work on Linux develop applications in C++, while other programmers working on Windows prefer C#. Many cross-platform systems are developed in Java. Objective ... [Show full abstract] C becomes more and more popular due to sales of iPads and iPhones. Additionally, scripting languages, such as Perl and Python, are very suitable to toolkit development.
Our newly developed course introduces students to the design and use of scripting languages for web development and rapid prototyping. The course also seeks to improve student understanding of language design and construction by exposing them to the different language paradigms found in the three languages Perl, JavaScript, and Python. The course includes lectures and assignments on topics common ... [Show full abstract] to these scripting languages such as regular expressions and web protocols. Since the introduction of the course, increasing numbers of students are now using a scripting language for their senior project, rather than a compiled language such a Java or C++. Students are able to make faster progress in their senior projects because the use of these languages enables them to spend more effort on problem solving and less effort on getting their programs to work. Their successful experiences in prototyping applications mirror many current industrial practices.
Object-oriented scripting languages such as JavaScript or Python gain in
popularity due to their flexibility. Still, the growing code bases written in
the languages call for methods that make possible to automatically control the
properties of the programs that ensure their stability in the running time. We
propose a type system, called Lucretia, that makes possible to control the
object ... [Show full abstract] structure of languages with reflection. Subject reduction and soundness
of the type system with respect to the semantics of the language is proved.
December 2013 · California Cooperative Oceanic Fisheries Investigations Report
Converting between geographic coordinates in latitude and longitude and the line and station sampling pattern of the California Cooperative Fisheries Investigations (CalCOFI) program is a commonly required task for conducting research on the California Current ecosystem. This note presents several corrections and clarifications to the previously published algorithms for performing these ... [Show full abstract] conversions. We include computer code to implement the algorithms in Java(TM1), Perl, Python, and R. We note that freely available code to conduct the conversions in Fortran, Matlab((R) 2), JavaScript(TM), and Visual Basic((R) 3) has previously been published, and an online conversion tool is also available. A future version of the PROJ.4 cartographic projections library will also include support for CalCOFI conversions, thereby allowing for convenient conversions using the GRASS GIS, PostGIS, Python, Perl, R, and many other programs and programming languages.
Coding for Penetration Testers: Building Better Tools, Second Edition provides readers with an understanding of the scripting languages that are commonly used when developing tools for penetration testing, also guiding users through specific examples of custom tool development and the situations where such tools might be used. While developing a better understanding of each language, the book ... [Show full abstract] presents real-world scenarios and tool development that can be incorporated into a tester's toolkit. This completely updated edition focuses on an expanded discussion on the use of Powershell, and includes practical updates to all tools and coverage. Discusses the use of various scripting languages in penetration testing Presents step-by-step instructions on how to build customized penetration testing tools using Perl, Ruby, Python, and other languages Provides a primer on scripting, including, but not limited to, web scripting, scanner scripting, and exploitation scripting Includes all-new coverage of Powershell.
© 2008-2021 ResearchGate GmbH. All rights reserved.
To read the full-text of this research, you can request a copy directly from the authors.
Lingerie Feet
Porno Hotwife Bbc
Bd Naked
Nasty Prospects 10
Outdoor Covers



 630_.jpg" width="550" alt="Coding For Penetration Testers" title="Coding For Penetration Testers">
630_.jpg" width="550" alt="Coding For Penetration Testers" title="Coding For Penetration Testers">