Busting Myths: What Proxy Servers Are Able To and Cannot Do
In the modern digital world, proxy servers have become a topic of intrigue and confusion for many internet users. With our online lives becoming more interconnected with privacy and security concerns, understanding what proxy servers can really accomplish is important. Many myths exist, and misinformation can lead to misguided expectations about how these tools operate. This article aims to illuminate the truth of proxy servers, helping you comprehend their operations, benefits, and restrictions.
Proxy servers act as bridges between users and the internet, delivering various benefits for both personal and commercial purposes. Nevertheless, not all that is said about them is accurate. From increasing web privacy to enabling entry to geo-restricted content, proxy servers have a wide range of uses. Yet, their performance can vary greatly depending on the category of proxy and how it is configured. Join us as we bust popular myths surrounding proxy servers and clarify what they can and cannot do.
Understanding Proxy Servers
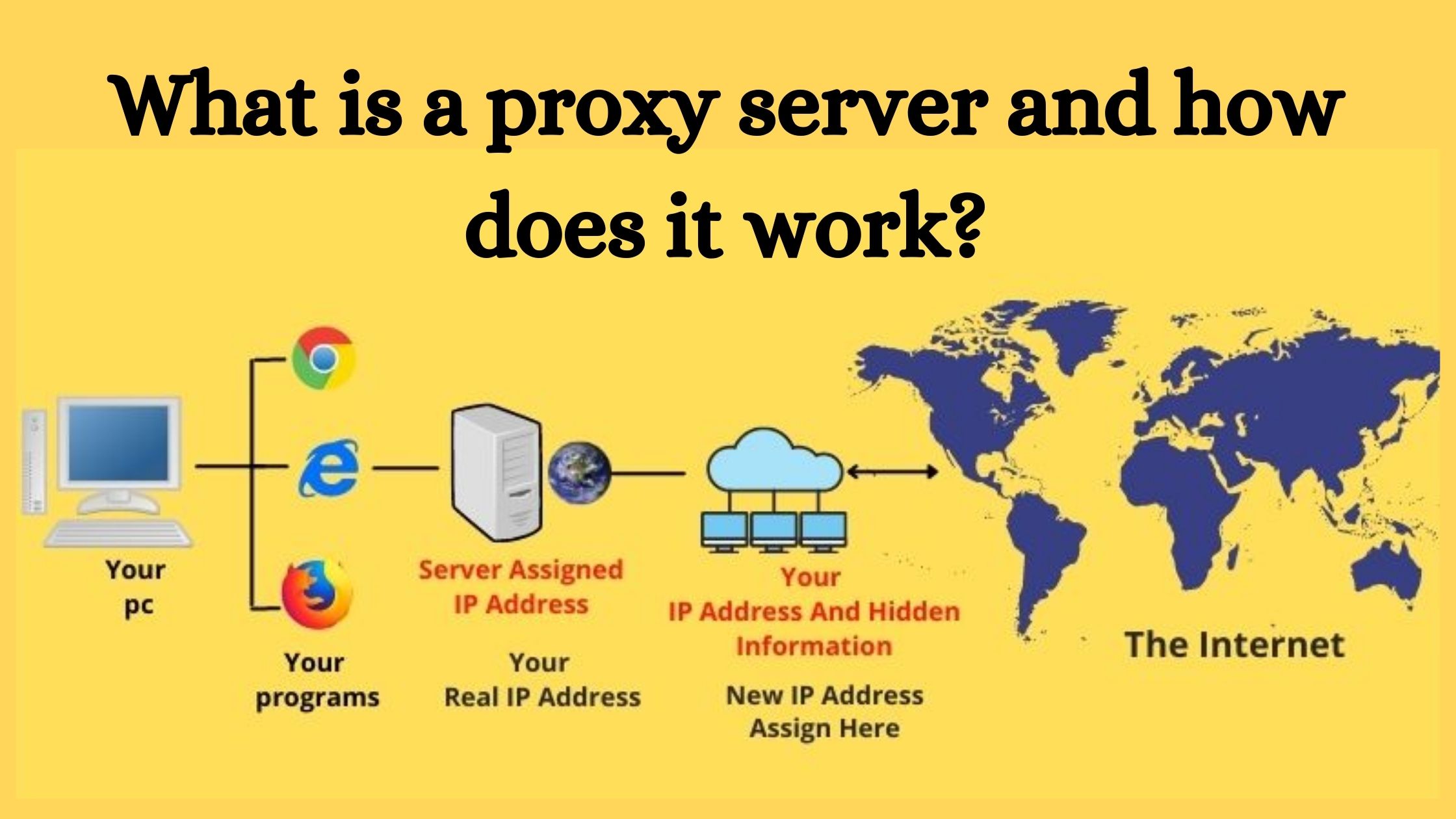
Such servers act as intermediaries between a user's device and the internet. When a user establishes a connection to the internet through a proxy server, their requests are sent via the proxy before reaching the target website. This process masks the user's IP address, providing a degree of privacy and security. Essentially, a proxy server retrieves data from the internet for the sake of the user, causing it to appear as though the request is originating from the proxy itself.
There are different types of proxy servers, every one serving distinct purposes. For example's sake, HTTP proxies are frequently used for web traffic, while SOCKS proxies can manage various types of traffic, including email and video streaming. Transparent proxies do not alter requests or responses, commonly used in organizational networks for data filtering. Comprehending these various types helps users select the right proxy server to satisfy their specific needs, whether for privacy, security, or content access.
The functions of proxy servers extend past anonymity. They can enhance online security by blocking harmful content, blocking access to malicious sites, and shielding sensitive data. In addition, proxy servers improve internet performance by caching frequently accessed content, diminishing load times, and decreasing bandwidth usage. This complex role shows how proxy servers are crucial tools for individuals and businesses looking to optimize their online activities and safeguard their information.
Advantages and Risks of Using Proxy Servers
Proxy services offer a range of benefits for individuals looking for enhanced online privacy and safety. By routing internet traffic through a proxy, individuals can mask their IP identifiers, making it more hard for sites and online services to monitor their actions. This increased anonymity can be especially beneficial for those who prioritize their privacy while browsing or participating in online transactions. Furthermore, proxy servers can assist individuals bypass geo-restrictions, allowing access to materials that may be restricted in their area, such as media services or specific websites.
However, there are also risks associated with using proxy servers, particularly when selecting complimentary or untrusted providers. Free proxies often have poor security measures and can leave individuals to information leaks or harmful attacks. Users may find their personal information at stake when using insecure proxies, making it important to choose a reputable service. Additionally, reliance on servers can lead to slower connection speeds, especially when streaming bandwidth-intensive content, which may reduce from the overall online experience.
Furthermore, it's vital to recognize that not all servers provide the identical degree of protection against cybercriminals and online dangers. Although a server can obscure IP addresses and provide disguise, it doesn’t inherently encrypt data, which is a critical feature for protected online communication. Therefore, individuals must weigh the advantages and disadvantages carefully and consider their specific needs and situations when deciding whether to use a proxy server.
Proxy servers in Different Applications
Proxies have a wide range of uses across different areas, providing essential services that enhance online experiences and security. In the realm of cyber security, businesses use proxy servers to create an additional layer of defense against online threats. By routing traffic through a proxy, organizations can monitor and manage information flow, efficiently handling threats and safeguarding sensitive information. Moreover, proxy servers can limit employee access to specific websites, ensuring a concentrated work environment and enhancing overall efficiency.
Another significant application of proxy servers is in accessing content, particularly for overcoming geo-restrictions. Users utilize these proxy servers to access region-locked media on platforms such as Netflix and Hulu, allowing for a more diverse viewing experience without being restricted by geography. Many opt for custom proxy servers designed for streaming to ensure high bandwidth and performance, ensuring smooth viewing without disruptions. This has made proxy servers a preferred choice for users looking to explore an extensive range of online content that would otherwise be inaccessible.
In data scraping and market analysis, proxy servers are invaluable tools for businesses and individuals alike. https://buyproxy.omeka.net/ allow individuals to collect data from various sites without causing red flags that would result in bans or limits. By using different proxy servers, scrapers can spread their requests, mimicking genuine user behavior and thus preventing detection. This capability gives companies a strategic advantage by enabling them to obtain information and data analysis from rivals rapidly and efficiently, solidifying the role of proxy servers as a critical resource in modern data-driven strategies.