Bitcoin Private Key Scanner Decimal

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
Blockchain Fundamentals Coin Guides Developer Guides
A Bitcoin private key is an unimaginably large number that is kept secret and used to access BTC when making transactions. This article will explain what Bitcoin private keys are, and how they’re used to grant access to funds. It also details the differences between various private key formats, such as hexadecimal, wallet import format (WIF), and compressed wallet import format (compressed WIF).
As noted in the introduction, a Bitcoin private key, a.ka. BTC private key, is just an enormous number. In particular, it’s a 256-bit number. A bit is just a “binary digit,” meaning a single bit is either a 0 or a 1. There are no other possibilities for the value of a single bit. It’s also important to note that a bit is the smallest unit of data that computers can process.
So, if a Bitcoin private key is just a 256-bit number, then can a private key be expressed in a 256-character string of ones and zeros? Indeed, it can. Here’s an example:
This is an example of a Bitcoin private key in binary format.
If you’re sufficiently strong-willed and patient, you could theoretically generate a random private key by flipping a coin 256 times and recording the result each time. Just choose which side corresponds to which value (either heads is equal to 0 and tails is equal to 1 or vice versa), and flip away.
In practice, this method of choosing a random key shouldn't be used. Generally speaking, humans are not very good at generating entropy (randomness). For instance, perhaps the way the coin is tossed isn't exactly the same every time, leading to a result of tails at a greater rate than heads. Or, maybe the coin may have a slight physical imperfection that results in heads appearing much more often than tails.
It's best to generate a Bitcoin private key using a tool or program that ensures a high level of entropy for maximum security. Remember that Bitcoin private keys should always be kept secret. There are a few places online where you can find a Bitcoin private key list, which means the corresponding public address is compromised. Thus, it's very difficult to find Bitcoin private keys with balance still belonging to them.
Of course, binary is not the only format in which Bitcoin private keys can be expressed. In fact, there are several other formats. One is called decimal, which simply means writing the number out in full form. For instance, the number “thirteen million” written out in decimal is 13,000,000. Using a simple converter tool, the Bitcoin private key in binary format above can be expressed in decimal format like this:
As you can see, it is an incredibly large number. Put in very simple terms, that is what drives the power of Bitcoin security— incomprehensibly large numbers. This makes it very, very, very difficult to generate private key from Bitcoin address.
Bitcoin wallets are a little like bank accounts locked with very, very large numbers as passcodes. If someone were to correctly guess your Bitcoin private key’s number, they would have access to your BTC and could easily steal your funds. However, because such gargantuan numbers are involved, the probability of that happening is basically zero.
Think of it this way: if every human on Earth had a computer program that allowed them to take a guess at your Bitcoin private key 1 Billion times per day per person, every day, for 100 years straight, the chances of anyone correctly guessing your private key number would still be in the ballpark of 1 in 3,512,469,265,893,923,428,170,004. Let that sink in for a moment.
But what about public keys and addresses? Since those are shared publicly, can’t someone discover your private key? Well, as it turns out, this isn’t any more likely than someone guessing your Bitcoin private key outright.
There are two layers of security to prevent an attacker from discovering your Bitcoin private key, even if they know your BTC address: Elliptic Curve Cryptography (ECC) and cryptographic hash functions.
The Bitcoin software uses an advanced form of public key cryptography called Elliptic Curve Cryptography. In particular, Bitcoin uses the secp256k1 implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA). This sounds very complex and, indeed, the mathematics behind the ECDSA are extremely advanced. Fortunately, you don’t actually need to understand the details to understand how the ECDSA keeps Bitcoin private keys secure.
As noted at the beginning of the article, a Bitcoin private key is just a very large number. When this very large number is multiplied with the predetermined “generator point” on the secp256k1 elliptic curve, it produces a new point on the same curve. This new point is the public key that corresponds to the private key in question. One private key produces exactly one public key.
So, from a very high level, a public key is just a point on this curve (y^2==x^3+7). The point has an x-coordinate and a y-coordinate. The public key is simply these two values pushed up against one another (with a small prefix to indicate the format).
This provides two very important benefits. First, the public key can be shared with the network and it is still virtually impossible to reverse engineer the private key. Second, the private key can provide digital signatures such that the network can mathematically prove with 100 percent certainty that a particular Bitcoin private key provided the signature, without actually needing to know the private key itself. This is how most transactions are carried out.
Some researchers have noted that, at some point in the future, a theoretical attack from quantum computers could make cracking ECDSA cryptography possible. For an increased level of security—plus an easier and more friendly UX— we normally use addresses when making transactions, rather than public keys. This adds an extra layer of encryption to the public key. Let’s learn more about what makes an address different from a public key.
Cryptographic hash functions are mathematical equations used to create a digital fingerprint of data. They have a few important properties that make them extremely useful.
First of all, cryptographic hash functions are one-way only, meaning that input goes in and an output comes out, but there is absolutely no way to determine an input from the output alone.
Second, no matter what kind of data or what length of data you put in, you will get a random-looking string of data in return that is of fixed length and offers no clues about the input that produced it. If you enter a short input of, say, ten words, you will get an output 64 characters. If you enter an input of ten thousand words, you will still get an output of 64 characters.
Third, the same input will always produce the same output. If you use the same input and the same hash function ten million times in a row, you will receive the same output ten million times over.
Fourth, the probability of finding two inputs that produce the same output is so incredibly small that it can safely be assumed impossible. Once someone discovers two inputs that produce the exact same output, the hash function is considered broken and insecure.
Lastly, computers must be able to execute the hash function very, very quickly. This also means that, once you have a secret input, it’s trivial to confirm that the output (called the hash) matches a previously-announced public hash.
So, to provide users with an extra layer of security, we often use Bitcoin addresses, rather than public keys. When a public key is hashed with the Secure Hash Algorithm 256 (SHA-256), and then the resulting hash is hashed again with the RACE Integrity Primitives Evaluation Message Digest 160 (RIPEMD-160), the result is known simply as a “pubkey hash.” Remember that hash functions cannot be reversed, so, if you know someone’s pubkey hash, you can send them funds but you cannot determine what their public key is (let alone their private key).
Once the pubkey hash is derived, a few more steps are required to create an address. To get the address, you add the version byte (normally 0x00 for the Bitcoin protocol) to the beginning of the pubkey hash. That new string is then hashed again with SHA-256. The first four bytes (32 bits) of that hash (considered the checksum) are added to the end of the previous RIPEMD-160 hash, then the whole string is converted from a byte string into a base58 encoded string. This is the address.
Bitcoin addresses always start with a “1”, “3”, or “bc1”, making them easily distinguishable from public keys and private keys.
We can think of using an address as effectively securing the public key, which can technically be shared publicly. The only thing that absolutely must be kept secret is the Bitcoin private key. But, if an added layer of security is available, it makes sense to use it as a fail-safe. In addition, addresses are much shorter and easier to manage than public keys so they provide a better user experience.
Let’s look at a basic example of how a private key is used in a transaction.
Suppose Alice wants to buy a latte at Bob's Coffee Shop. The price of a latte is currently 0.0005 BTC. Before the transaction occurs, Alice's funds are secure in her wallet. Alice only needs to provide two things to the Bitcoin network to complete the purchase: her public key and a digital signature from her Bitcoin private key.
Recall that digital signatures are a secure way of verifying private key ownership publicly without ever having to reveal one’s private key. A digital signature can be thought of as a one-time password generated for each unique transaction.
In our example, as long as Alice is the only person who knows her Bitcoin private key, she is also the only person who can create the digital signature required to spend funds from her wallet. Let’s say Alice has 1 BTC in her wallet before buying a latte. Alice creates a unique digital signature for the 0.0005 BTC needed to purchase a latte. The transaction is broadcast to the Bitcoin network and confirmed by Bitcoin nodes. This 0.0005 BTC is now available in the wallet belonging to Bob’s Coffee Shop. No one else, including Bob’s Coffee Shop, can spend the remaining 0.9995 BTC in Alice’s wallet.
If Alice or someone else tries to use the same digital signature for a second transaction, Bitcoin nodes will always reject it. A second transaction would require a new, unique digital signature.
As discussed, there are multiple formats in which the same private key can be expressed. The two formats we covered in the beginning of the article— binary and decimal— are almost never used. They are useful for generating a Bitcoin private key but most wallet applications use other formats. In particular, wallets typically use hexadecimal, wallet import format (WIF), and/or compressed wallet import format (compressed WIF).
Let’s take a look at these three most common private key formats.
Hexadecimal is a notation that uses only the numerical digital 0—9 and the letters A—F. This makes data expressed in hexadecimal easier to read. Bitcoin private keys written in binary or decimal format can easily be converted to hexadecimal.
Here is the same BTC private key we expressed in binary and decimal at the beginning of the article converted to hexadecimal.
The wallet import format (WIF) and compressed wallet import format compressed (compressed WIF) are the most commonly used formats for Bitcoin private keys. They provide two main advantages over the above-mentioned formats. First, they are much shorter. This helps reduce copy/paste errors. Second, they use base58Check code to check for potential errors. That makes WIF formats very beneficial from an end-users’ perspective. Base58Check encoded private keys for WIF always start with a “5”, and compressed WIF private keys always start with a “K” or “L”.
It’s crucial to understand that compressed WIF doesn’t refer to private key compression. Bitcoin private keys are neither compressed or uncompressed. In fact, you might notice that the compressed WIF format, as seen in the example below, is one byte longer than WIF. It’s called “compressed WIF” because it indicates to the software to derive the compressed pubkey from it. Similarly, the "uncompressed wif" indicates to the wallet software to derive an uncompressed public key.
Of course, both the WIF private key and the compressed WIF private key can easily be converted to the other format. In that sense, both the compressed pubkey and the uncompressed pubkey can be derived from either the WIF or the compressed WIF. It may just require an extra step of conversion at the beginning.
Using a tool like this one, you can easily convert a BTC private key among various formats. Using the same address above in hexadecimal formats, we get the following results:
While WIF and compressed WIF are the most common formats for Bitcoin private keys, there are several other formats that are beginning to gain popularity. Let’s learn more about them.
Similar to WIF, mini private keys are also Base58Check encoded to prevent typos and copy/paste errors. It’s important to note that mini private keys can only be created from scratch, meaning you can’t convert a full-size private key to a mini private key. However, you can convert a mini private key to a full-size private key.
Mini private keys can be as few as 30 characters. They start with an “S” and look something like this.
Bitcoin Improvement Protocol 38 (BIP38) provides a way to encrypt a Bitcoin private key with a long passphrase composed of human-readable words. With this extra step of encryption, it’s possible to securely share the encrypted private key with a third-party. Without both the Bitcoin private key and the correct passphrase, it is impossible to access the funds held in that wallet.
For example, the address and encrypted private key can be printed on a physical bitcoin, while the passphrase is stored in a separate location or memorized. Even though others may know the private key, the funds are still secure.
In any case, BIP38 encryption requires the wallet owner to provide the encrypted Bitcoin private key along with an additional passphrase to access a BTC wallet and spend funds. BIP38 can be thought of as a form of two-factor authentication in which the wallet owner sets a personalized, reusable password. As with traditional passwords, you should choose a phrase that is difficult for others to guess.
BIP38 private keys always start with a “6P” and look something like this.
If you'd like to learn more about blockchain technology, check out Komodo's Blockchain Fundamentals series. These posts explain a wide variety of crucial blockchain topics, from things like cryptocurrency mining and margin trading to Proof of Work and Proof of Stake.
Begin your blockchain journey with Komodo today.
Blockchain and Crypto Education Platform - Blockchain Fundamentals, Coin Guides, and Developer Guides
Blockchain applications have many use cases in sectors that deal with the tokenization of assets. The interaction with a blockchain creates transactions, and blockchain offers a validation process. This interaction does not limit blockchain applications to financial use.
In this blog post, we cover the difference between centralized and decentralized exchanges - looking at the benefits and drawbacks of both.
Read to learn more about how blockchain architecture keeps data secure and what makes blockchain unique from ordinary databases.
Blockchain and Crypto Education Platform - Blockchain Fundamentals, Coin Guides, and Developer Guides
Great! Next, complete checkout for full access to Komodo Academy | En
Welcome back! You've successfully signed in
You've successfully subscribed to Komodo Academy | En
Success! Your account is fully activated, you now have access to all content
Success! Your billing info has been updated
Not a member of Pastebin yet? Sign Up, it unlocks many cool features!
# THE BTC CLEAN SWEEPER ! DONATE BTC TO 370f6522-bc63-448d-a153-bdd76c769808 AND EMAIL REQUEST TO SCRITS4HCK@HMAMAIL.COM , DOWNLOAD LINK WILL THEN BE EMAILED.
This script generates private keys from a word-list or pass-phrase list, it then checks the number of transactions on the account to show if it is active or not. The script then checks the current balance and if positive it sweeps the bitcoins by importing the private keys into your blockchain wallet. Active keys from the output should also be loaded into your wallet or monitored for a transaction, once a transaction is in process this a positive balance, you can transfer the BTC to another address that you control.
A script that takes a list of private keys, for example held in a text file and monitors the accounts every X seconds. As soon as an account becomes active, the BTC are transfered out to an address specified by you, in a matter of seconds.
Requests: To request any hacking scripts please send a BTC donation to 370f6522-bc63-448d-a153-bdd76c769808 and email details of your request to scripts4hck@hmamail.com : only requests from people who have donated BTC will be actioned.
Order: To order Key Monitor, please send a BTC donation to 370f6522-bc63-448d-a153-bdd76c769808 and email the details of the transaction to scripts4hck@hmamail.com.
Other Scripts available: Facebook brute forcer, BTC Key Encryption Tester + ecdsa-cracker (Find weak BTC transaction input and output scripts allowing us to gain access to the ecdsa private keys using ecdsa-cracker)
A limited number of copies will be distributed so only people who donate will be allocated a copy! Copies will be distributed in order of donation value, high to low.
Usage: cd to directory i.e cd Desktop/Btc-clean-sweeper.... ./perl sweeper.pl -w[wordlist] -t[threads] -o[output.txt]
perl sweeper.pl -w pass.txt -t 10 -o output.txt
It can be used to generate bitcoin private keys from passphrases
and the associated transactions and current balance. It can be used to sweep remaining balance to your BTC wallet.
[i] Sweeping 2.0004826 to wallet ...
18X6yC1p1hXvXjuwZfjT52Z1am9LNuAAC6, Passphrase: appointivelivefree
18X6yC1p1hXvXjuwZfjT52Z1am9LNuAAC6, Received Transactions: 4.00005460
18X6yC1p1hXvXjuwZfjT52Z1am9LNuAAC6, PrivateKey: 5JhijED9PdJHxBhAqFW3kWaJRkvckFsLY7jou4BmqnEmzf5WMHf
18X6yC1p1hXvXjuwZfjT52Z1am9LNuAAC6, Current Balance: 2.0004826
~/Btc-clean-sweeper# apt-get install libwww-mechanize-perl
~/Btc-clean-sweeper# apt-get install build-essential
~/Btc-clean-sweeper# apt-get install python-ecdsa
~/Btc-clean-sweeper# apt-get install cpanminus
~/Btc-clean-sweeper# cpanm Finance::Bitcoin::API
~/Btc-clean-sweeper# cpanm Parallel::ForkManager
~/Btc-clean-sweeper# perl sweeper.pl
Usage: perl sweeper.pl -w Thelist.txt -t 10 -o outputkeys.txt
We use cookies for various purposes including analytics. By continuing to use Pastebin, you agree to our use of cookies as described in the Cookies Policy. OK, I Understand
Krasivie Kiski Sex
Shemale And Guy Fuck Each Other
Pack Russian Mom Natalia Torrent
Izmena Xxx 2021
Girl Gives Blowjob
Bitcoin Private Key Scanner Decimal | Heavy- metal TRU ...
Bitcoin Private Key: An Easy-To-Understand Overview
BTC Scanner and Private Key - Pastebin.com
Bitcoin Private Key Auto Scanner - fluxorin.io
Key scanner - GitHub Pages
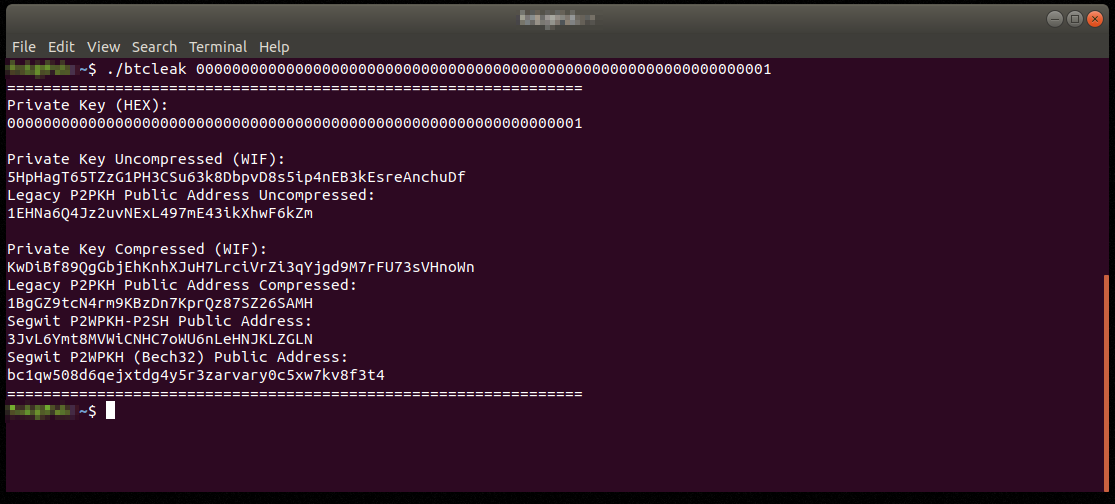
A super-fast Bitcoin private key generator - BTC Leak
000000000000000000000000000…
Ethscan.App - Scanner All Private Keys Ethereum
Braliman - bitcoin private key database with balance #1
Bitcoin Private Key Scanner Decimal