Begin Rsa Private Key Mii

🛑 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE👈🏻👈🏻👈🏻
Sign up or log in to view your list.
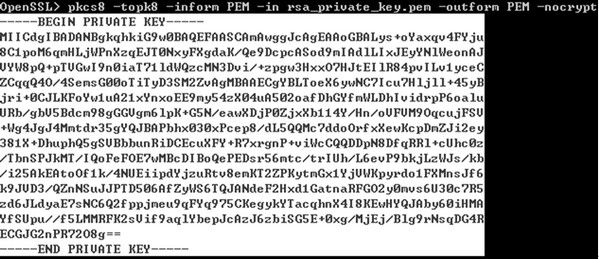
Until now I didn't find a specification (RFC or similar) for the file format that uses the BEGIN RSA PRIVATE KEY prefix and END RSA PRIVATE KEY suffix. Where is it defined? Is there an official name for it? It seems to be at least related to the series of PEM RFCs.
I am looking for reference information about the details of whitespace handling, base64 details, joining of different keys in one file etc..
This question is NOT about the ASN encoding of the payload.
Gustave
Gustave 250●11 gold badge●22 silver badges●77 bronze badges
\begingroup The OpenPGP specification describes similar ASCII-Armor formats.
\endgroup – CodesInChaos Apr 25 '17 at 11:27
\begingroup The most of PEM formats (also other than RSA Private Key) are documented in RFC 7468: Textual Encodings of PKIX, PKCS, and CMS Structures. There are e.g. some guidance on topic of whitespace handling. That RFC basically notes that details vary according to parser.
\endgroup – user4982 Apr 25 '17 at 13:09
\begingroup Thanks to user4982: This is the kind of source I am looking for. However, RFC 7468 contains information regarding the label "ENCRYPTED PRIVATE KEY", but it doesn't for "RSA PRIVATE KEY".
\endgroup – Gustave Apr 25 '17 at 15:06
\begingroup PEM is defined in RFC 1421 which describes the overall format of the header, etc. But I couldn't find about the "RSA PRIVATE KEY". This article from 1997 already mentions OpenSSL using it.
\endgroup – Conrado Apr 25 '17 at 16:46
I'm here, because, I'm asking myself the same question as the OP.
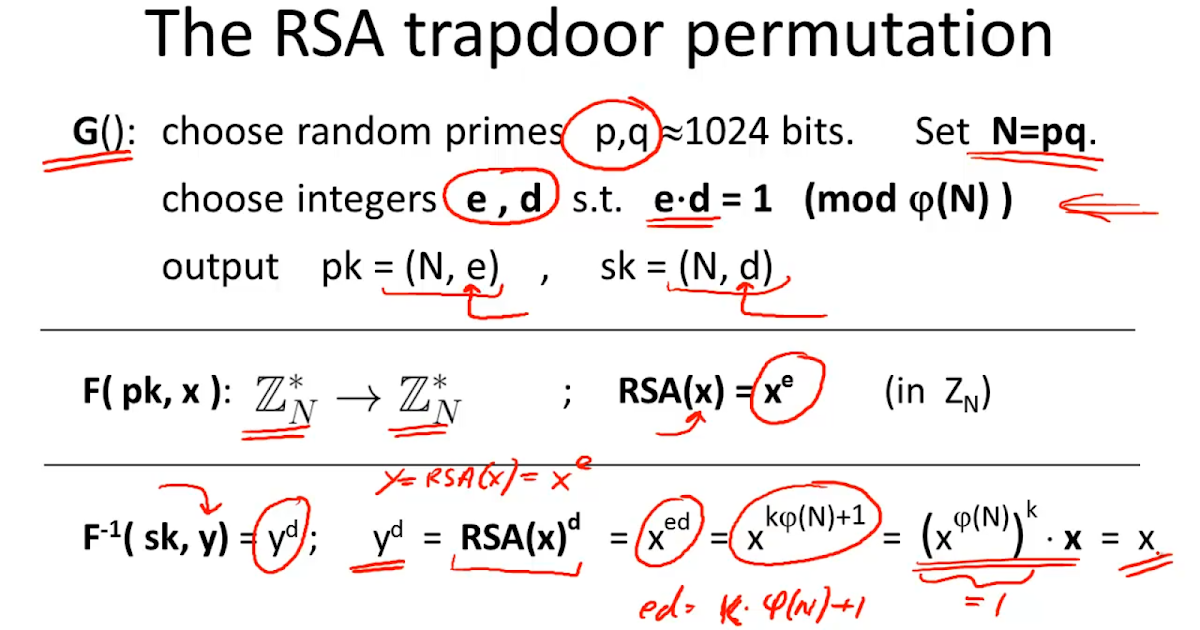
PKCS#1 (RFC 3447) defines the ASN.1 structure: RSAPrivateKey, permitting the expression of an RSA private key only.
PKCS#8 (RFC 5208) defines the ASN.1 structure: PrivateKeyInfo, permitting the expression of any private key. (For an RSA private key, PrivateKeyInfo is some packaging information, and a reuse of RSAPrivateKey from PKCS#1).
PEM (Privacy Enhanced Mail), is a defunct method for secure email. But, its container format was borrowed for packaging cryptographic items.
RFC 7468 (Introduction): "For reasons that basically boil down to non-coordination or inattention, many PKIX, PKCS, and CMS libraries implement a textbased encoding that is similar to -- but not identical with -- PEM encoding."
Which reads as: Um, folk have decided to use bits of PEM to package thier crypto files. Here we have a jolly good effort to try and formalise that...
Alas, RFC 7468 clarifies the PKCS#8/PrivateKeyInfo packaging as "BEGIN PRIVATE KEY". But not the packaging of PKCS#1/RSAPrivateKey as "BEGIN RSA PRIVATE KEY".
The "BEGIN RSA PRIVATE KEY" packaging is sometimes called: "SSLeay format" or "traditional format" for private key. Which, as least, gives us a name for this format, but, like yourself, I cannot find, and would welcome, something that approaches a formal description of this format. I suspect this does not exist.
William Ellis
William Ellis 126●22 bronze badges
\begingroup I'm here, because, I'm asking myself the same question as the OP. --- To clarify: is this your answer to the question asked above, or are you actually asking yourself the same question?
\endgroup – e-sushi May 15 '17 at 19:03
The format of the base64 contents inside:
You already know how to encode that using the DER flavor of ASN.1; and the question is about how to actually write that DER binary data to a file.
There is then the "Encapsulation Boundary" (EB), used to delimit encapsulated PEM messages.
It was the defuct Privacy Enhanced Mail that used:
Those PEM conventions were carried over for public key, private key, and certificates, but with suitable changed wording:
Ian Boyd
Ian Boyd 831●77 silver badges●1212 bronze badges
This document articulates the de facto rules by which existing implementations operate and defines them so that future implementations can interoperate.
10. One Asymmetric Key and the Textual Encoding of PKCS #8 Private Key Info
Unencrypted PKCS #8 Private Key Information Syntax structures (PrivateKeyInfo), renamed to Asymmetric Key Packages (OneAsymmetricKey), are encoded using the "PRIVATE KEY" label. The encoded data MUST be a BER (DER preferred; see Appendix B) encoded ASN.1 PrivateKeyInfo structure as described in PKCS #8 [RFC5208], or a OneAsymmetricKey structure as described in [RFC5958]. The two are semantically identical and can be distinguished by version number.
mikemaccana
mikemaccana 337●44 silver badges●1313 bronze badges
\begingroup I am asking about "RSA PRIVATE KEY", not about "CERTIFICATE REQUEST". By the way, I would expect PKCS #8 or PKCS #1, not PKCS #10. Chapter 10 would be closer. But it doesn't specify RSA in the label, so it makes sense to use PKCS #8 here. As the key algorithm would be specified redundantly, it could be OK (and I saw examples) to put PKCS #1 in a "RSA PRIVATE KEY" file.
\endgroup – Gustave Apr 28 '17 at 19:10
\begingroup @As I already said, I am looking for "RSA PRIVATE KEY", not for "PRIVATE KEY". So, even chapter 10 is not applicable, and RFC7468 is a wrong answer.
\endgroup – Gustave May 11 '17 at 5:33
\begingroup @Gustave I'm aware you wrote "RSA PRIVATE KEY", however specifying the format of the private key in the header is unnecessary and the spec is relevant.
\endgroup – mikemaccana May 12 '17 at 12:42
\begingroup The ABNF reads <> and <>. So, why do you think the header is unnecessary?
\endgroup – Gustave May 16 '17 at 6:33
\begingroup PKCS #1 (tools.ietf.org/html/rfc8017#appendix-A.1.2) doesn't specify any ASCII base64 encoding, and it also doesn't specify the -----BEGIN RSA PRIVATE KEY----- header. PKCS #8 doesn't specify any ASCII base64 encoding either. Chapter 10 indeed specifies -----BEGIN PRIVATE KEY-----. Do you have a link to a standard which specifies the the -----BEGIN RSA PRIVATE KEY----- header?
\endgroup – pts May 1 '20 at 21:54
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Home
About
AutoWrapper
Tags
Signing JWT with RSA in .NET Core 3.x Made Easy
Software Engineer, Microsoft MVP, C# Corner MVP, CodeProject MVP, MVA, MVE, Geek, Author, Mentor and a frustrated musician.
More posts by Vincent Maverick Durano.
There are cases that you will be working with external client integration and your API/service will act as a proxy that needs to perform some data processing which requires you to implement a feature based on external client needs. One typical example is to implement a custom JWT (a.k.a token) generation with custom claims that is signed using RSA algorithm.
In this scenario, the external client will give you the structure of JWT, normally with custom claims that they expect and provide you with an RSA private key to sign the token. The token will then be used to construct a Uri that will be sent to users and allowing them to invoke the external client endpoints.
In this post, we are going to take a look at how we can easily integrate this feature within our .NET Core 3.x application.
If you are new and haven't worked with RSA signing before, here's a quick definition taken from Wikipedia:
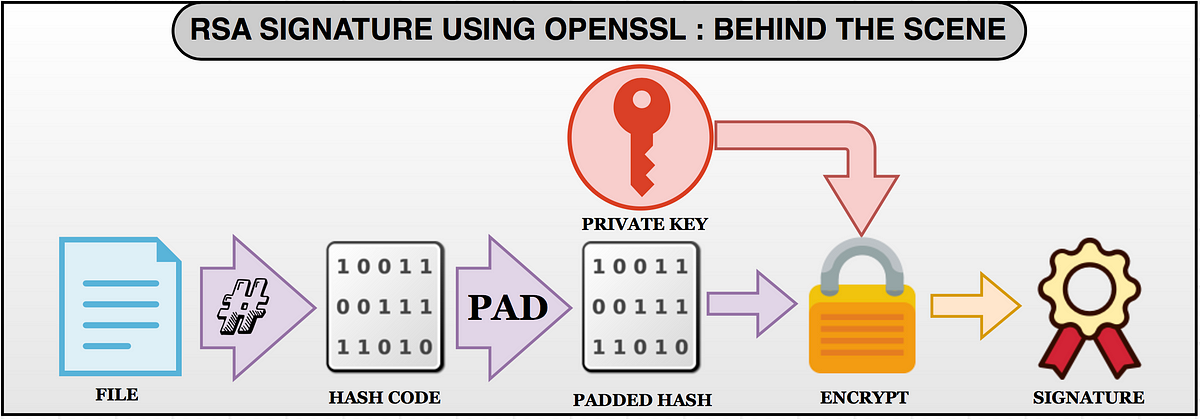
RSA (Rivest–Shamir–Adleman) is one of the first public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and distinct from the decryption key which is kept secret (private).
Unlike HMAC where it uses a shared secret key across many applications - a.k.a symmetric primitive, RSA uses a pair of private and public keys to validate the token - a.k.a asymmetric primitive. In other words, with RSA, your service will use a private key to sign the JWT, and all other applications may use the public key to verify the token's validity and integrity.
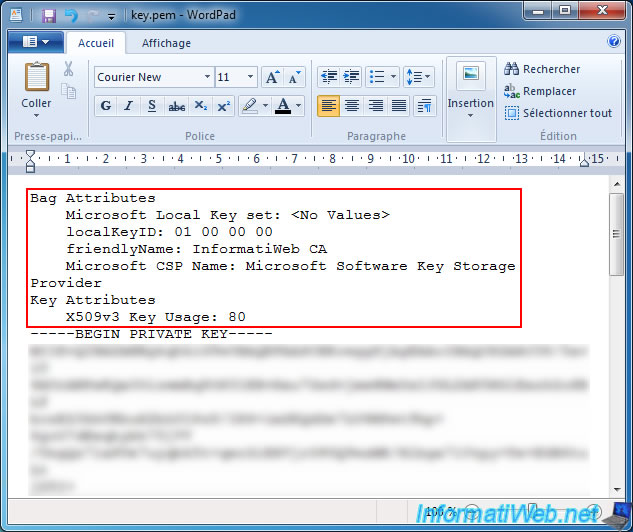
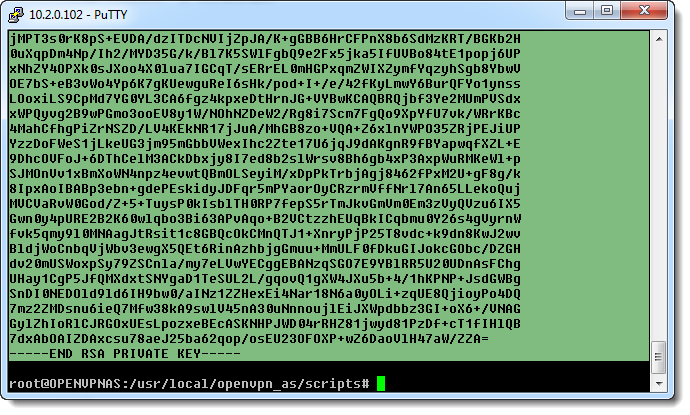
Assuming that you already have the RSA private key given to you by your external client. Typically the key should be in the following format:
The BEGIN and END lines represent the header and the footer for the key. Within that is the actual key
that represents a base64-encoded text format based from the PKCS #1: RSA Cryptography Specifications, which is just an Abstract Syntax Notation One Sequence of integers that makes up the RSA key.
For the simplicity of this demo, let's just use the appsettings.json file store the keys and other required information. Please note that you should consider storing secrets and sensitive information in a vault or secrets manager.
Here's the entry within the appsettings.json file:
Most of the values in the appsettings.json should come from your external client. If you are only given the private key, you can generate the public key using the openssl RSA command by following these simple steps:
The command above should give you the matching RSA public key as shown in the following:
We will use the public key later to perform token validation.
Tip:
Note that the RSA keys base64-encoded text are formatted with carriage return, so be sure to make it one-liner when storing them in appsettings.json, vault or variable. Also don't include the header and footer when storing the RSA keys. Just set the base64-encoded text in the RsaPrivateKey and RsaPublicKey attributes.
I'd like to point out that we will not be implementing an Authentication scheme for this demo as we will not be protecting any resources here, instead your service will act as the proxy to your external client for issuing and signing JWT's. Your external client will be the one to protect their resource and only authorize access to requests with the signed JWT that we are going to implement.
Now that we have our appsettings.json configured, let's create the following simple class that we can use to bind the values from appsettings.json:
Next is add the following code below within the ConfigureServices() method of Startup.cs file:
The preceding binds the configuration that we have defined within appsettings.json under ExternalClientServer node. This allow us to access strongly typed object via IOptions by registering the ExternalClientJsonConfiguration class into the DI service container.
Now let's create the following classes below:
The code above is nothing but just simple classes that house some properties. The JwtCustomClaims class holds the custom claims that we are going to pass in the JWT. The JwtResponse class holds two main properties that we are going to return for testing purposes.
Next, let's create the following interface below:
The interface above holds two main methods: The CreateToken which takes a JwtCustomClaims as a parameter and returns a JwtResponse. The ValidateToken method takes a token (JWT) as the parameter which returns a boolean. Simple as that!
At this point, we already have the basic requirements that we need to implement the JWT handler. In this demo, we are going to use the System.IdentityModel.Tokens.Jwt Nuget package as it provides a rich support for creating, serializing and validating JSON Web Tokens in .NET Core. Let's go head and install that using the following command:
Here's the class implementation below:
Let's take a look at what we did in the preceding code above.
First we created an extension method called TypeConverterExtension which converts string to byte[] using the Convert.FromBase64String() method. Nothing fancy.
Next is the JWT handler class that implements the IJwtHandler interface. You will notice that we have injected the ExternalClientJsonConfiguration class as an IOptions in the class constructor to be able to automatically access the values we defined the appsettings.json in a strongly-type manner. This process is called "Constructor Injection".
Within the JwtHandler class, you will see that we have implemented the interface methods called CreateToken and ValidateToken.
The CreateToken method is where we implement the the RSA Private Key importing and signing of JWT. Let's start digging into the specific code snippet below:
The preceding code reads the RSA private key from appsettings.json and translate that to byte array using the ToByteArray() extension method. We then call RSA.Create() and then import the RSA private key byte array format using ImportRSAPrivateKey method that is built-in to .NET Core 3.x. I use the _ (discard) to indicate that the second parameter should be ignored because we don't need the value for the bytesRead.
The next step in the code is setting up the signing credentials in the following manner:
The preceding code creates a new instance of SigningCredentials method and passing in the RSA Private Key and security signature algorithm to RsaSha256. Notice that I set the CacheSignatureProviders to false because it will throw the following error below on subsequent requests:
If you know a hack on how to fix the error above without turning off the CacheSignatureProviders, please let me know by dropping your comments. I would truly appreciate it :)
The following block of code is the typical implementation of generating JWT in .NET Core:
The preceding code constructs the structure of the JWT using the JwtSecurityToken object and setting in the required metadata such as audience, issuer, expires, notBefore, basic claims, custom claims and the signature of the token expressed in signingCredentials meta.
It then generates a token by invoking a new instance of JwtSecurityTokenHandler().WriteToken() method.
And finally, we return the response containing the JWT and expiry.
The ValidateToken method on the other hand seems to be very straight-forward. Let's start with the following code block:
As you can see, the implementation is somewhat similar to importing the RSA private key, except that for validation, it uses the RSA public key and uses the ImportRSAPublicKey method which is also built-in to .NET Core.
The next code block is the typical implementation for setting token validation parameters for JWTs:
The preceding code configures the validation parameters including the issuer, audience and the signature. We've also disabled caching the signature provider associated with keys from a TokenValidationParameters object.
Finally, we use the ValidateToken method of JwtSecurityTokenHandler object to validate the JWT based on the validation parameters we configured in the previous code:
If the call to ValidateToken method fails, we simply return false, otherwise we return true. If you like, you can use the value of validatedSecurityToken variable to look into the validated JWT.
Now that we have our JWT handler all setup, the last thing we need to do is to register the contract mapping between our IJwtHandler interface and the concrete implementation. Let's go ahead and add the following code in the ConfigureServices method of Startup.cs file:
To test the JwtHandler methods, let's create a simple API Controllers containing two endpoints. Here's the code block:
Nothing fancy there, we basically just expose the following endpoints for us to test:
Because we registered our IJwtHandler interface and it's mapping into the DI service container, injecting the interface into the Controller's constructor will enable us to access the available methods and it will automatically resolved them at run time.
Here are the sample requests and the corresponding test results that I ran in POSTMAN.
Pasting the JWT to jwt.io should result to something like this:
And you can use the Public Key to validate the signature via jwt.io as well.
Now that we are able to generate JWTs, generating links should be very straight-forward. For example, in the JwtHandler class you could add a new method like this:
That's it! Thanks for reading and I hope you find this post useful. Source code is available here: https://github.com/proudmonkey/NetCoreJwtRsaDemo
Get the latest posts delivered right to your inbox
Great! Check your inbox and click the link to confirm your subscription.
Please enter a valid email address!
You've successfully subscribed to ProudMonkey!
Could not sign up! Invalid sign up link.
Stay up to date! Get all the latest & greatest posts delivered straight to your inbox
Great! Check your inbox and click the link to confirm your subscription.
Please enter a valid email address!
Lesbian Fisting Pissing
Good Wife Bad Wife
Vintage Video Ru
Xnxx Ass Shemale
Xvideo Public Fuck
Is there a specification for the "BEGIN RSA PRIVATE KEY ...
Различия между «BEGIN RSA PRIVATE KEY» и «BEGIN PRIVATE KEY»
Import and Export RSA Key Formats in .NET Core 3
private-key-github-concourse: | -----BEGIN RSA PRIVATE KEY ...
BEGIN RSA PRIVATE KEY ...
Rsa Private Key: Understanding public/private RSA keys ...
Error Private key must begin with -----BEGIN RSA PRIVATE ...
Begin Rsa Private Key Mii
.png)