Begin Private Key

🔞 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
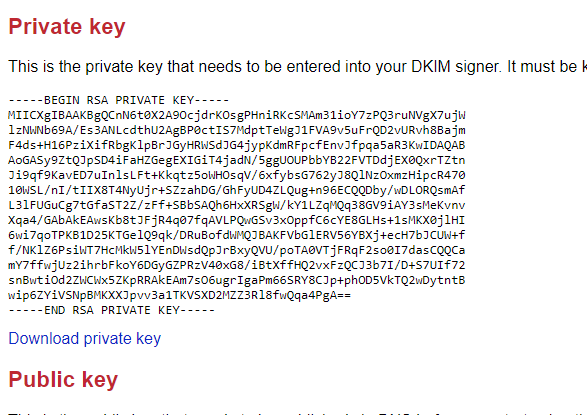
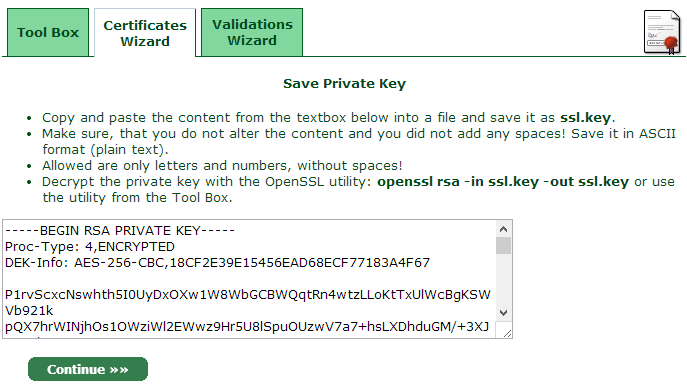
Begin Private Key
Better Ranking in Google Search
Security
Domain SSL By GoGetSSL
from $39.00 /yr
Home
Wiki
Problems & Issues
Lost private key
Opera Explorer Firefox Safari Chrome
SSL Supported by 99.6% of browsers and Mobile Devices
© 2009-2019 Copyright EnVers Group Ltd. All Rights reserved
Secured and Trusted Site
Identity Assured up to $1,750,000
EnVers Group SIA Liesmas 4-24, Riga, Latvia, LV1058
https://www.gogetssl.com 3-Feb 2021 03:02:32 Europe/Riga
Losing the private key is the most common issue webmasters faces during SSL certificate installation. This article will help you to fix that issue helping to understand possible scenarios to recover the key or to regenerate and reissue SSL.
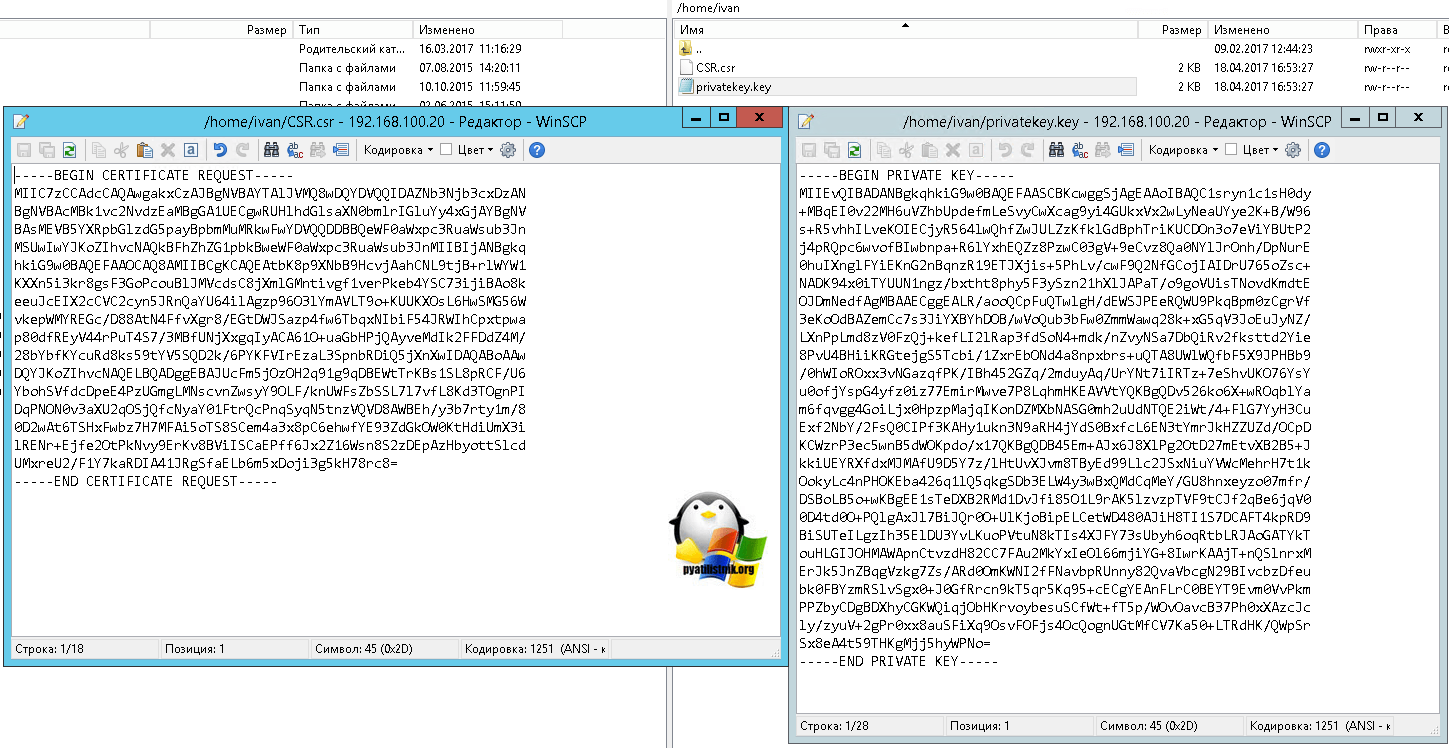
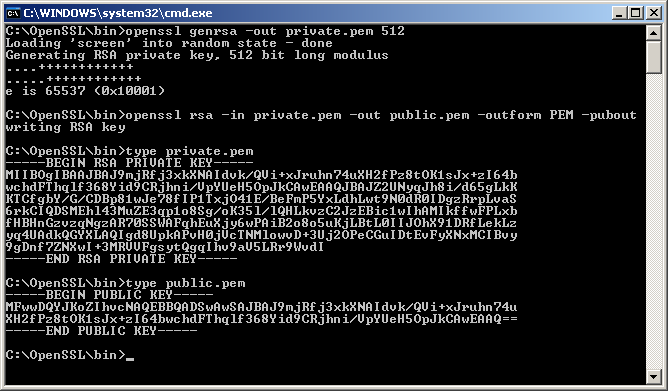
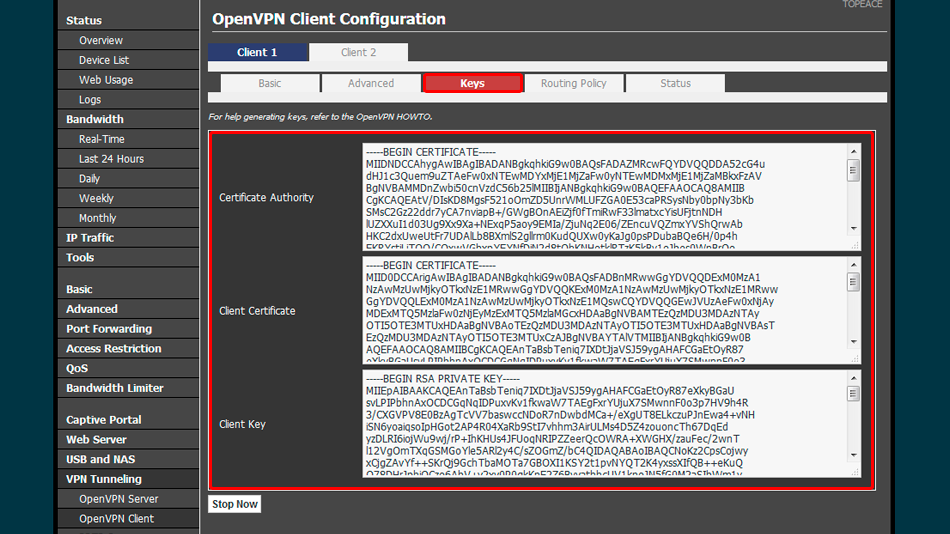
You receive a private key when generate a Certificate Signing Request (CSR). You submit the CSR code to the CA (certificate authority) and keep private key in a safe place. That means nor us (GoGetSSL), nor CAs have ever your private key. We are not able to recover it, but we can Reissue SSL with a new key. There are multiple ways where you can generate CSR/KEY:
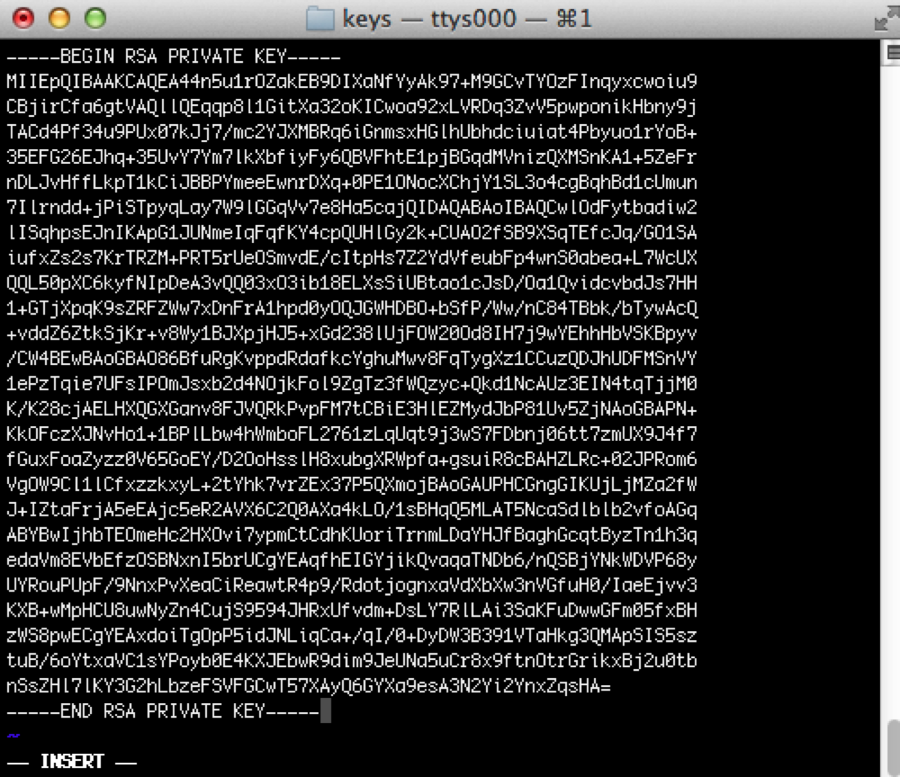
The RSA key looks like an array of encoded data, starting and ending with headers, such as -----BEGIN PRIVATE KEY----- and -----END PRIVATE KEY-----
We do not store any private keys for issued SSL certificates. The only solution we have, in case you have lost the private key, is to reissue SSL certificate following the Wiki guide .
There is no option for viewing the private key in plain text on Windows servers. The proper private key is connected automatically when you import certificate via IIS or MMC, however, the CSR and KEY should be generated on the same server.
You can export the key using a password-protected PFX (PKCS#12) file if necessary to get the private key out to install SSL on a different server. Open MMC certificates following the next steps:
Then, go to Personal > Certificates, right-click to the certificate, then "All Tasks" > "Export". You will be able to export your certificate following the instructions from the Export Wizard. Please check more instructions on Windows Docs page.
You will receive a .pfx file containing your SSL certificate, private key and CA-bundle, once the export process is done. You can use the online tool to convert your "PKCS12" file to "PEM". Once the conversion is done you will have your private key available.
There is no option getting the private key via the graphic user interface of the Keychain tool on Mac OS X. You have to use the Terminal for that. Open /etc/certificates/ directory and search for the file like "*.key.pem". Use the following terminal commands:
The private key should be stored in a password-protected Keystore file in case your Tomcat SSL connector configurated in JSSE style. You have to convert the Keystore into PFX file using the command below to get the private key:
You can convert your new PKCS12 file to PEM file to get a separate certificate, CA-bindle and key files using the terminal command below or online tool . You can rename “Private.key” to any name you wish.
You must save the private key during CSR generation using VestaCP. No key will be available in any Web Client area later. However, there is one option to recover the private key using SSH by checking a temporary file in the "/tmp" folder. The path may look like on example:
Please note, every time you reboot the server the folder will be deleted. You can try old Linux command to get the exact path to the file:
Replace "domain.tld" with the actual domain name.
An alternative option is trying the "grep" command
The Private key is saved on the server in the latest version of DirectAdmin. It will be fetched during the installation process to the "Paste a pre-generated certificate and key" field." The section will be empty if you generated CSR and Key elsewhere or panel has an internal problem. You can try using SSH to find the key, as ususlaly it is saved in the next directory:
where and are your DirectAdmin username and the domain you are trying to recover the key for.
It is a simple task to recover the Private key on Webuzo management in case a pair of CSR and Private Key were generated using that panel.
Lossing the private key is not fatal in case you were using management panels. However, we highly suggest keeping a private key in a very safe place. Reissue SSL if you suspect the key could get to 3rd party hands.
Get a Domain Validation SSL certificate within just 5 minutes using our friendly and automated system. No paperwork, callback or company required.
Found a better price? We will match it - guaranteed. Get the best possible price in the World with us. The correct place to save your money.
Try 90-day Trial SSL Certificate before the real purchase to test cert's functionality. 99.9% browser and mobile support. Unlimited prolongation.
Customer satisfaction is our major concern. Get a full refund within 30 days for any purchase of SSL certificates with 100% guarantee.
GoGetSSL™ now offering fastest issuance of SSL on planet due to use of LEI code and API automation. Legal Entity Identifier (or LEI) is a global identity code, just like DUNS. Learn now how LEI may help you.
This website uses cookies in order to improve your web experience. Privacy Policy
Parse RSA public and private key pair from string in Java · GitHub
Lost Private key | SSL Wiki
Is there a specification for the " BEGIN RSA PRIVATE KEY " format?
Key File Formats | Programster's Blog | Private Key
PKCS #8 PrivateKeyInfo Unencrypted: ----- BEGIN PRIVATE KEY ... | Limilabs
The best answers are voted up and rise to the top
Asked
3 years, 9 months ago
Active
3 years, 3 months ago
250 1 1 gold badge 2 2 silver badges 7 7 bronze badges
The OpenPGP specification describes similar ASCII-Armor formats.
– CodesInChaos
Apr 25 '17 at 11:27
The most of PEM formats (also other than RSA Private Key) are documented in RFC 7468: Textual Encodings of PKIX, PKCS, and CMS Structures . There are e.g. some guidance on topic of whitespace handling. That RFC basically notes that details vary according to parser.
– user4982
Apr 25 '17 at 13:09
Thanks to user4982: This is the kind of source I am looking for. However, RFC 7468 contains information regarding the label "ENCRYPTED PRIVATE KEY", but it doesn't for "RSA PRIVATE KEY".
– Gustave
Apr 25 '17 at 15:06
PEM is defined in RFC 1421 which describes the overall format of the header, etc. But I couldn't find about the "RSA PRIVATE KEY". This article from 1997 already mentions OpenSSL using it.
– Conrado
Apr 25 '17 at 16:46
I'm here, because, I'm asking myself the same question as the OP. --- To clarify: is this your answer to the question asked above, or are you actually asking yourself the same question?
– e-sushi
May 15 '17 at 19:03
781 6 6 silver badges 12 12 bronze badges
337 4 4 silver badges 13 13 bronze badges
I am asking about "RSA PRIVATE KEY", not about "CERTIFICATE REQUEST". By the way, I would expect PKCS #8 or PKCS #1, not PKCS #10. Chapter 10 would be closer. But it doesn't specify RSA in the label, so it makes sense to use PKCS #8 here. As the key algorithm would be specified redundantly, it could be OK (and I saw examples) to put PKCS #1 in a "RSA PRIVATE KEY" file.
– Gustave
Apr 28 '17 at 19:10
@As I already said, I am looking for "RSA PRIVATE KEY", not for "PRIVATE KEY". So, even chapter 10 is not applicable, and RFC7468 is a wrong answer.
– Gustave
May 11 '17 at 5:33
@Gustave I'm aware you wrote "RSA PRIVATE KEY", however specifying the format of the private key in the header is unnecessary and the spec is relevant.
– mikemaccana
May 12 '17 at 12:42
The ABNF reads <> and <>. So, why do you think the header is unnecessary?
– Gustave
May 16 '17 at 6:33
PKCS #1 ( tools.ietf.org/html/rfc8017#appendix-A.1.2 ) doesn't specify any ASCII base64 encoding, and it also doesn't specify the -----BEGIN RSA PRIVATE KEY----- header. PKCS #8 doesn't specify any ASCII base64 encoding either. Chapter 10 indeed specifies -----BEGIN PRIVATE KEY----- . Do you have a link to a standard which specifies the the -----BEGIN RSA PRIVATE KEY----- header?
– pts
May 1 '20 at 21:54
Cryptography
Tour
Help
Chat
Contact
Feedback
Mobile
Disable Responsiveness
Company
Stack Overflow
For Teams
Advertise With Us
Hire a Developer
Developer Jobs
About
Press
Legal
Privacy Policy
Terms of Service
Stack Exchange Network
Technology
Life / Arts
Culture / Recreation
Science
Other
Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. It only takes a minute to sign up.
Until now I didn't find a specification (RFC or similar) for the file format that uses the BEGIN RSA PRIVATE KEY prefix and END RSA PRIVATE KEY suffix. Where is it defined? Is there an official name for it? It seems to be at least related to the series of PEM RFCs.
I am looking for reference information about the details of whitespace handling,
base64 details, joining of different keys in one file etc..
This question is NOT about the ASN encoding of the payload.
I'm here, because, I'm asking myself the same question as the OP.
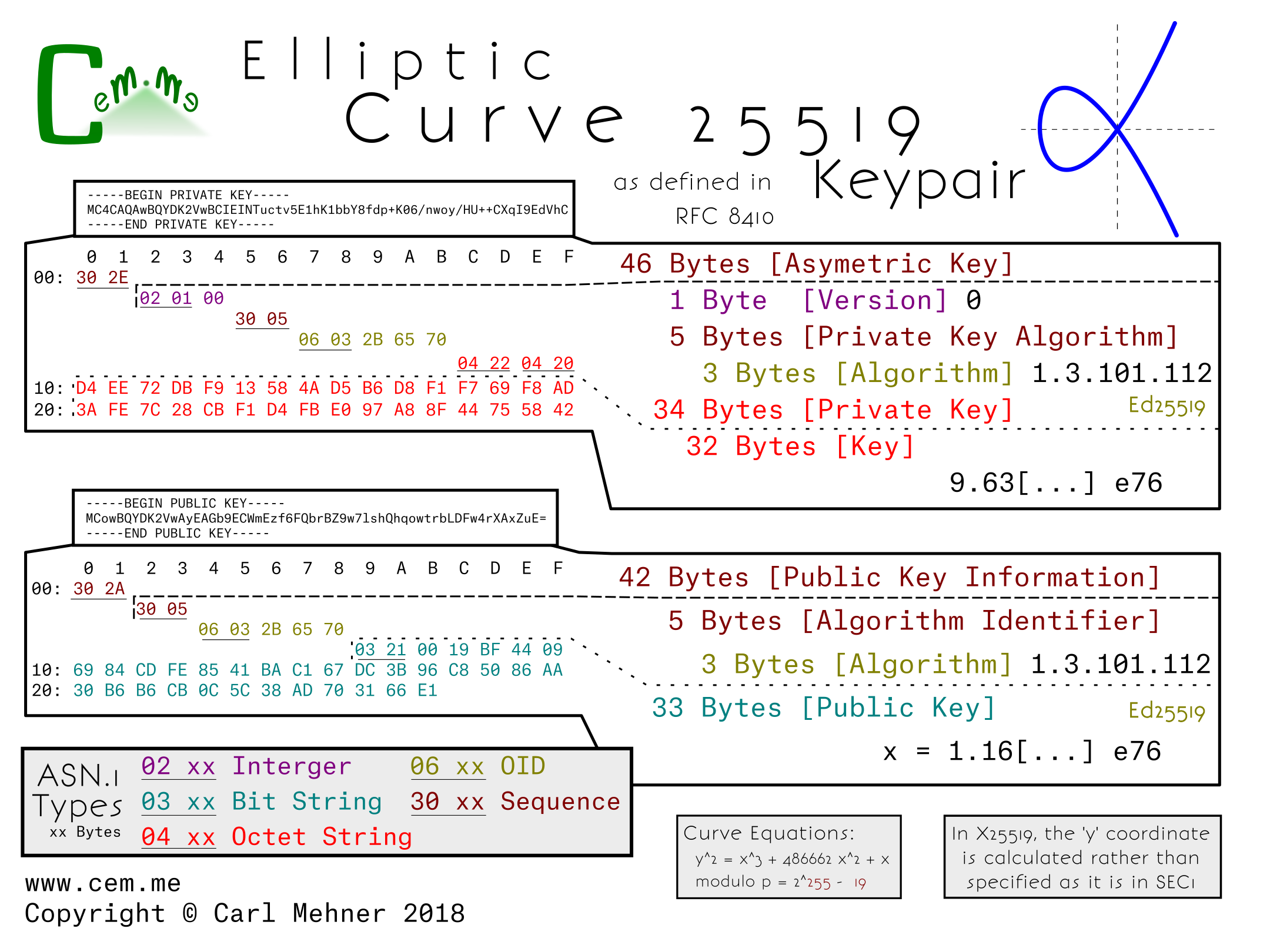
PKCS#1 (RFC 3447) defines the ASN.1 structure: RSAPrivateKey, permitting the
expression of an RSA private key only.
PKCS#8 (RFC 5208) defines the ASN.1 structure: PrivateKeyInfo, permitting the
expression of any private key. (For an RSA private key, PrivateKeyInfo is some
packaging information, and a reuse of RSAPrivateKey from PKCS#1).
PEM (Privacy Enhanced Mail), is a defunct method for secure email. But, its
container format was borrowed for packaging cryptographic items.
RFC 7468 (Introduction): " For reasons that basically boil down to non-coordination or inattention, many
PKIX, PKCS, and CMS libraries implement a textbased encoding that is similar to
-- but not identical with -- PEM encoding ."
Which reads as: Um, folk have decided to use bits of PEM to package thier
crypto files. Here we have a jolly good effort to try and formalise that...
Alas, RFC 7468 clarifies the PKCS#8/PrivateKeyInfo packaging as "BEGIN PRIVATE
KEY". But not the packaging of PKCS#1/RSAPrivateKey as "BEGIN RSA
PRIVATE KEY".
The "BEGIN RSA PRIVATE KEY" packaging is sometimes called: "SSLeay format" or
"traditional format" for private key. Which, as least, gives us a name for this
format, but, like yourself, I cannot find, and would welcome, something that
approaches a formal description of this format. I suspect this does not exist.
The format of the base64 contents inside:
You already know how to encode that using the DER flavor of ASN.1; and the question is about how to actually write that DER binary data to a file.
There is then the "Encapsulation Boundary" (EB), used to delimit encapsulated PEM messages.
It was the defuct Privacy Enhanced Mail that used:
Those PEM conventions were carried over for public key, private key, and certificates, but with suitable changed wording:
This document articulates the de facto rules by which existing implementations operate and defines them so that future implementations can interoperate.
10. One Asymmetric Key and the Textual Encoding of PKCS #8 Private Key
Info
Unencrypted PKCS #8 Private Key Information Syntax structures
(PrivateKeyInfo), renamed to Asymmetric Key Packages
(OneAsymmetricKey), are encoded using the "PRIVATE KEY" label. The
encoded data MUST be a BER (DER preferred; see Appendix B) encoded
ASN.1 PrivateKeyInfo structure as described in PKCS #8 [RFC5208], or
a OneAsymmetricKey structure as described in [RFC5958]. The two are
semantically identical and can be distinguished by version number.
By clicking “Post Your Answer”, you agree to our terms of service , privacy policy and cookie policy
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
site design / logo © 2021 Stack Exchange Inc; user contributions licensed under cc by-sa . rev 2021.2.2.38474
Peeing Forum
Subbygirls Her Oral Alarm Clock Porn
Huge Tits Pee
Naked College Girls
Overwatch Background