Aws Api Gateway Private Fargate

💣 👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
This sample project demonstrates how to use Step Functions to make a call to API Gateway in order to interact with a service on AWS Fargate, and also to check whether the call succeeded. This sample project creates the following:
An Amazon API Gateway HTTP API that is called by the state machine.
An Amazon API Gateway Amazon VPC Link.
Related AWS Identity and Access Management (IAM) roles
Several additional services that are required to enable these resources to work together.
For more information about API Gateway and Step Functions service integrations, see the following:
This sample project may incur charges.
For new AWS users, a free usage tier is available. On this tier, services are free below a certain level of usage. For more information about AWS costs and the Free Tier, see Pricing.
Open the Step Functions console and choose Create a state machine.
Choose Sample Projects, and then choose Call a microservice with API Gateway.
The state machine Code and Visual Workflow are displayed.
The Deploy resources page is displayed, listing the resources that will be created. For this sample project, the resources include:
Several additional services that are required to enable these resources to work together.
It can take up to 10 minutes for these resources and related IAM permissions to be created. While the Deploy resources page is displayed, you can open the Stack ID link to see which resources are being provisioned.
On the State machines page, choose the ApiGatewayECSStateMachine state machine that was created by the sample project, and then choose Start execution.
On the New execution page, enter an execution name (optional), and then choose Start Execution.
(Optional) To help identify your execution, you can specify an ID for it in the Enter an execution name box. If you don't enter an ID, Step Functions generates a unique ID automatically.
Step Functions allows you to create state machine, execution, and activity names that contain non-ASCII characters. These non-ASCII names don't work with Amazon CloudWatch. To ensure that you can track CloudWatch metrics, choose a name that uses only ASCII characters.
(Optional) Go to the newly created state machine on the Step Functions Dashboard, and then choose New execution.
When an execution is complete, you can select states on the Visual workflow and browse the Input and Output under Step details.
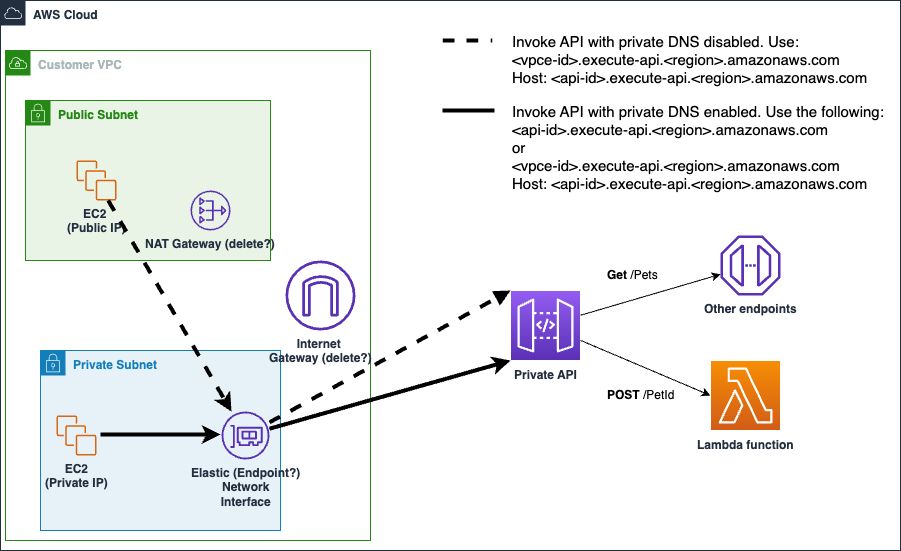
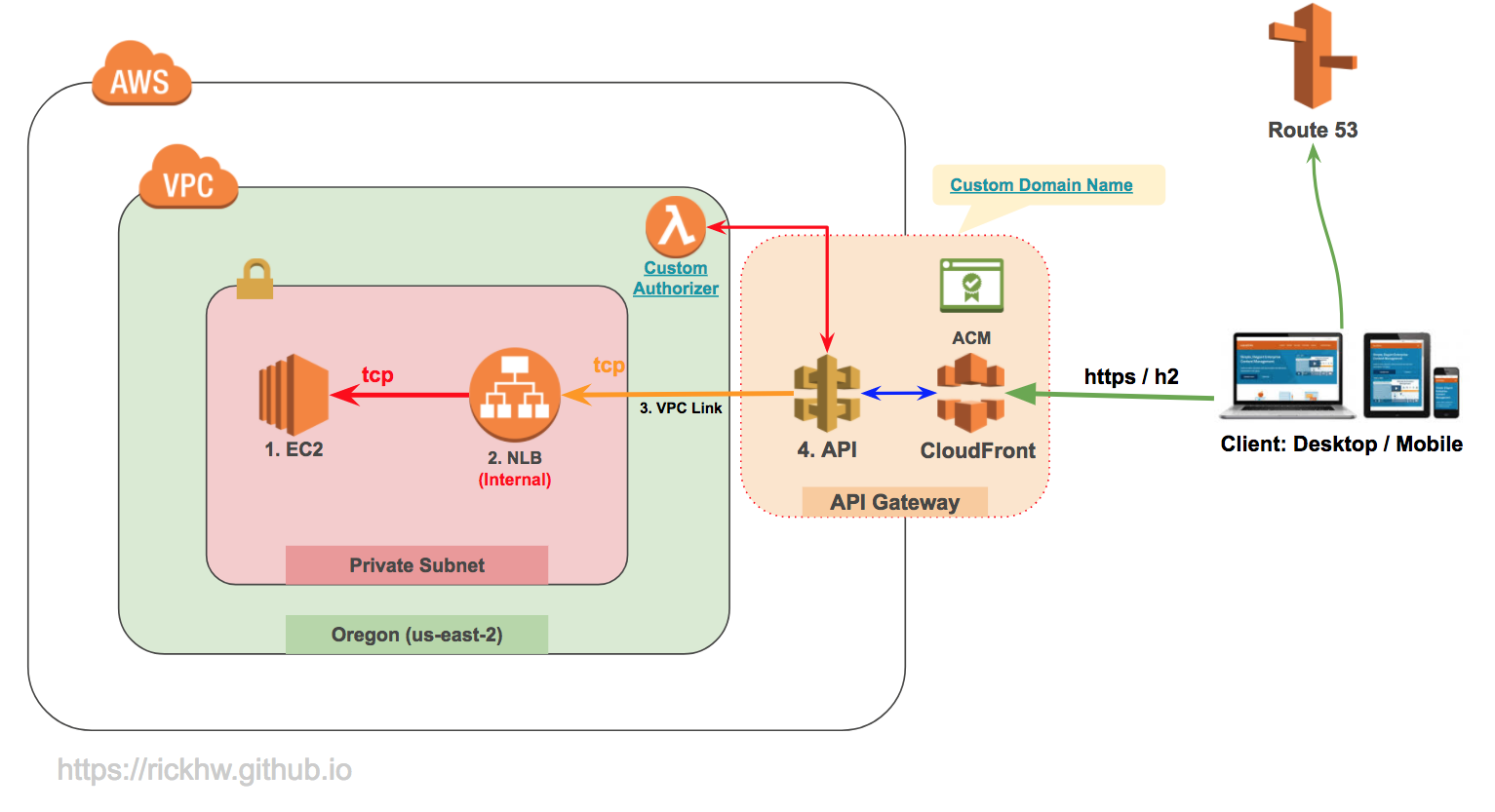
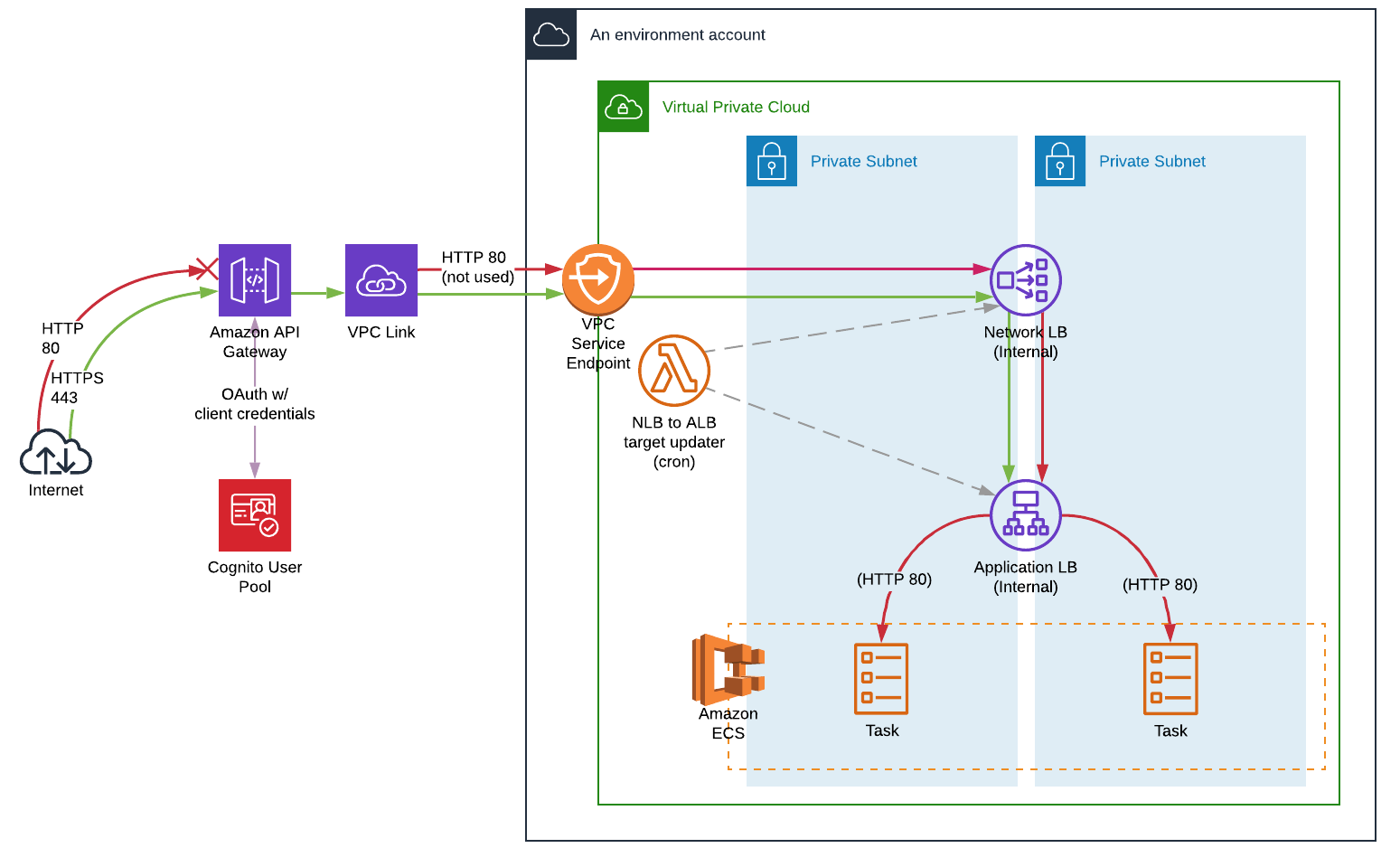
The state machine in this sample project integrates with API Gateway by calling an API Gateway HTTP API that is connected to a service on Fargate. This is hosted on a private subnet, and accessed through a private application load balancer.
Browse through this example state machine to see how Step Functions interacts with API Gateway and returns results.
For more information about how AWS Step Functions can control other AWS services, see Using AWS Step Functions with other services.
For information about how to configure IAM when using Step Functions with other AWS services, see IAM Policies for Integrated Services.
These example AWS Identity and Access Management (IAM) policies generated by the sample project include the least privilege necessary to execute the state machine and related resources. We recommend that you include only those permissions that are necessary in your IAM policies.
For information about how to configure IAM when using Step Functions with other AWS services, see IAM Policies for Integrated Services.
© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Thanks for letting us know we're doing a good job!
If you've got a moment, please tell us what we did right so we can do more of it.
Thanks for letting us know this page needs work. We're sorry we let you down.
If you've got a moment, please tell us how we can make the documentation better.
© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
This post is contributed by Mani Chandrasekaran | Solutions Architect, AWS
Customers would like to run container-based applications in a private subnet inside a virtual private cloud (VPC), where there is no direct connectivity from the outside world to these applications. This is a very secure way of running applications which do not want to be directly exposed to the internet.
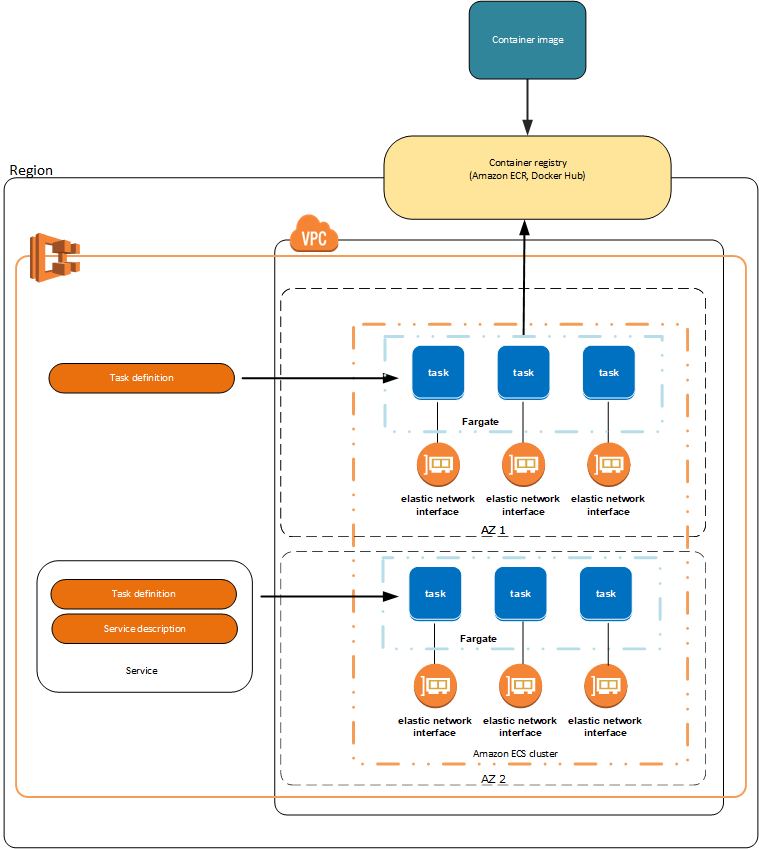
AWS Fargate is a compute engine for Amazon ECS that enables you to run containers without having to manage servers or clusters. With AWS Fargate with Amazon ECS, you don’t have to provision, configure, and scale clusters of virtual machines to run containers.
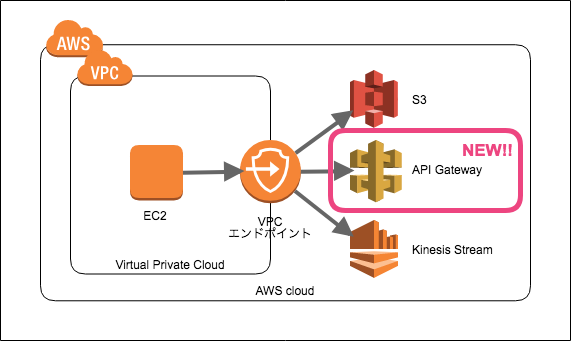
Amazon API Gateway is a fully managed service that makes it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale. The API Gateway private integration makes it simple to expose your HTTP and HTTPS resources behind a virtual private cloud (VPC) with Amazon VPC private endpoints. This allows access by clients outside of the VPC without exposing the resources to the internet.
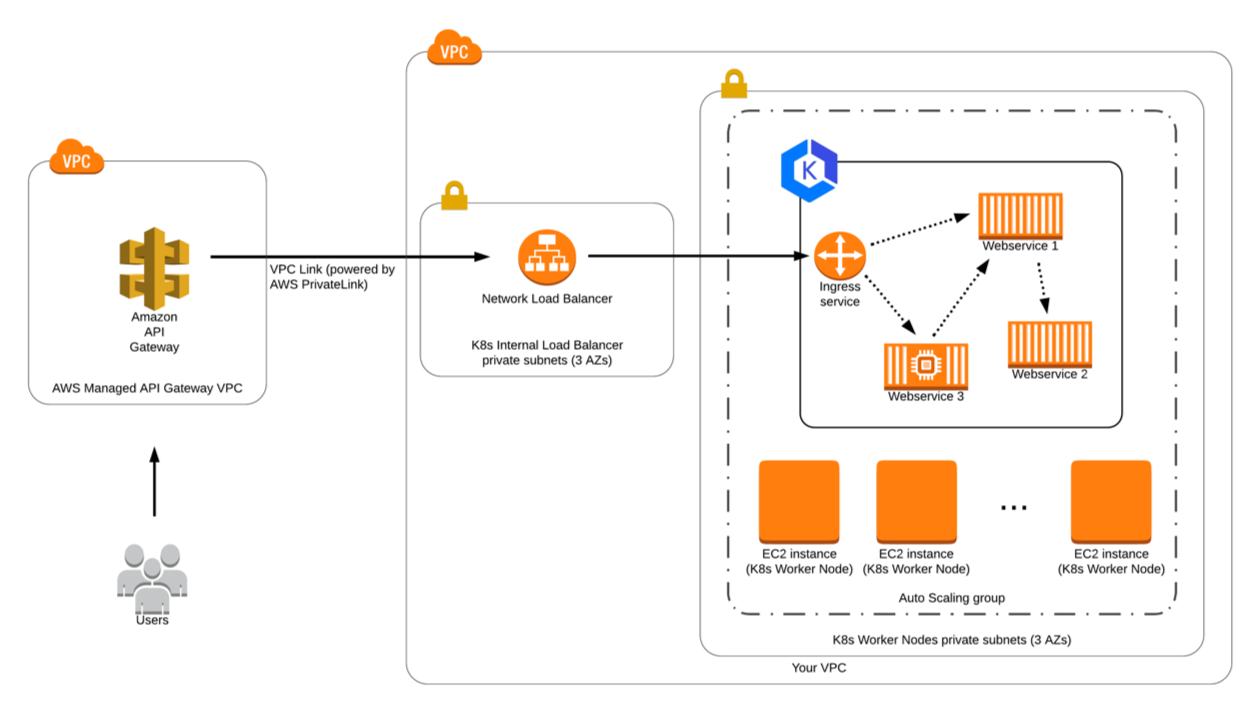
This post shows how API Gateway can be used to expose an application running on Fargate in a private subnet in a VPC using API Gateway private integration through AWS PrivateLink. With the API Gateway private integration, you can enable access to HTTP and HTTPS resources in a VPC without detailed knowledge of private network configurations or technology-specific appliances.
You deploy a simple NGINX application running on Fargate within a private subnet as a first step, and then expose this NGINX application to the internet using the API.
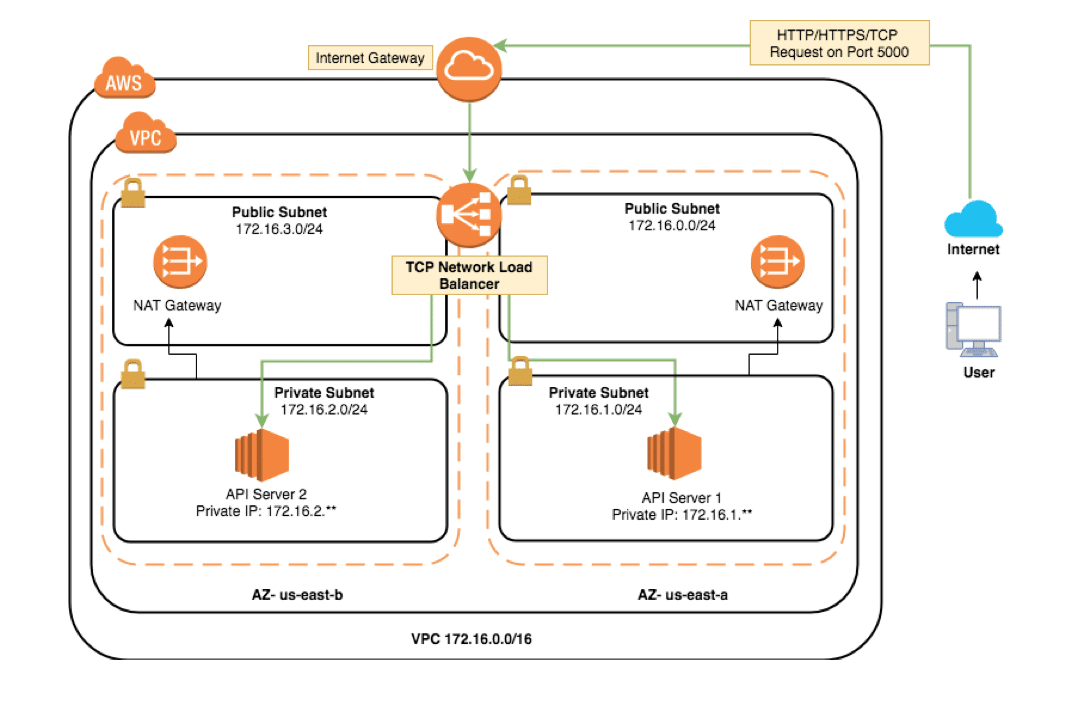
As shown in the architecture in the following diagram, you create a VPC with two private subnets and two public subnets. To enable the Fargate tasks to download Docker images from Amazon ECR, you deploy two network address translation (NAT) gateways in the public subnets.
You also deploy a container application, NGINX, as an ECS service with one or more Fargate tasks running inside the private subnets. You provision an internal Network Load Balancer in the VPC private subnets and target the ECS service running as Fargate tasks. This is provisioned using an AWS CloudFormation template (link provided later in this post).
The integration between API Gateway and the Network Load Balancer inside the private subnet uses an API Gateway VpcLink resource. The VpcLink encapsulates connections between the API and targeted VPC resources when the application is hosted on Fargate. You set up an API with the private integration by creating a VpcLink that targets the Network Load Balancer and then uses the VpcLink as an integration endpoint .
Here are the steps to deploy this solution:
Step 1 — Deploy an application on AWS Fargate
I’ve created an AWS CloudFormation template to make it easier for you to get started.
When the process is finished, the status changes to CREATE_COMPLETE and the details of the Network Load Balancer, VPC, subnets, and ECS cluster name appear on the Outputs tab.
Step 2 — Set up an API Gateway Private Integration
Next, set up an API Gateway API with private integrations using the AWS CLI and specify the AWS Region in all the AWS CLI commands.
1. Create a VPCLink in API Gateway with the ARN of the Network Load Balancer that you provisioned. Make sure that you specify the correct endpoint URL and Region based on the AWS Region that you selected for the CloudFormation template. Run the following command:
aws apigateway create-vpc-link \
--name fargate-nlb-private-link \
--target-arns arn:aws:elasticloadbalancing:ap-south-1:xxx:loadbalancer/net/Farga-Netwo-XX/xx \
--endpoint-url https://apigateway.ap-south-1.amazonaws.com \
--region ap-south-1
The command immediately returns the following response, acknowledges the receipt of the request, and shows the PENDING status for the new VpcLink:
{
"id": "alnXXYY",
"name": "fargate-nlb-private-link",
"targetArns": [
" arn:aws:elasticloadbalancing:ap-south-1:xxx:loadbalancer/net/Farga-Netwo-XX/xx"
],
"status": "PENDING"
}
It takes 2–4 minutes for API Gateway to create the VpcLink. When the operation finishes successfully, the status changes to AVAILABLE.
2. To verify that the VpcLink was successfully created, run the following command:
aws apigateway get-vpc-link --vpc-link-id alnXXYY --region ap-south-1
When the VpcLink status is AVAILABLE, you can create the API and integrate it with the VPC resource through the VpcLink.
3. To set up an API, run the following command to create an API Gateway RestApi resource
aws apigateway create-rest-api --name 'API Gateway VPC Link NLB Fargate Test' --region ap-south-1
Find the ID value of the RestApi in the returned result. In this example, it is qc83xxxx. Use this ID to finish the operations on the API, including methods and integrations setup.
4. In this example, you create an API with only a GET method on the root resource (/) and integrate the method with the VpcLink.
Set up the GET / method. First, get the identifier of the root resource (/):
aws apigateway get-resources --rest-api-id qc83xxxx --region ap-south-1
In the output, find the ID value of the / path. In this example, it is mq165xxxx.
5. Set up the method request for the API method of GET /:
aws apigateway put-method \
--rest-api-id qc83xxxx \
--resource-id mq165xxxx \
--http-method GET \
--authorization-type "NONE" --region ap-south-1
6. Set up the private integration of the HTTP_PROXY type and call the put-integration command:
For a private integration, you must set connection-type to VPC_LINK and set connection-id to the VpcLink identifier, alnXXYY in this example. The URI parameter is not used to route requests to your endpoint, but is used to set the host header and for certificate validation.
To test the API, run the following command to deploy the API:
aws apigateway create-deployment \
--rest-api-id qc83xxxx \
--stage-name test \
--variables vpcLinkId= alnXXYY --region ap-south-1
Test the APIs with tools such as Postman or the curl command. To call a deployed API, you must submit requests to the URL for the API Gateway component service for API execution, known as execute-api.
The base URL for REST APIs is in this format:
https://{restapi_id}.execute-api.{region}.amazonaws.com/{stage_name}/
Replace {restapi_id} with the API identifier, {region} with the Region, and {stage_name} with the stage name of the API deployment.
To test the API with curl, run the following command:
curl -X GET https://qc83xxxx.execute-api.ap-south-1.amazonaws.com/test/
The curl response should be the NGINX home page.
To test the API with Postman, place the Invoke URL into Postman and choose GET as the method. Choose Send.
The returned result (the NGINX home page) appears.
After you finish your deployment test, make sure to delete the following resources to avoid incurring future charges.
1. Delete the REST API created in the API Gateway and Amazon VPC endpoint services using the console.
Or, in the AWS CLI, run the following command:
aws apigateway delete-rest-api --rest-api-id qc83xxxx --region ap-south-1
aws apigateway delete-vpc-link --vpc-link-id alnXXYY --region ap-south-1
2. To delete the Fargate-related resources created in CloudFormation, in the console, choose Delete Stack.
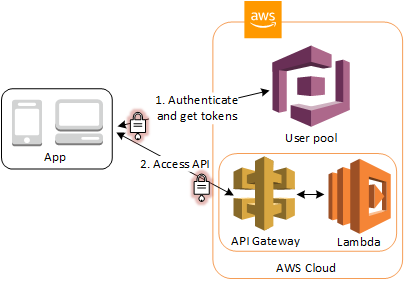
API Gateway private endpoints enable use cases for building private API–based services running on Fargate inside your own VPCs. You can take advantage of advanced features of API Gateway, such as custom authorizers, Amazon Cognito User Pools integration, usage tiers, throttling, deployment canaries, and API keys. At the same time, you can make sure the APIs or applications running in Fargate are not exposed to the internet.
By continuing to use the site, you agree to the use of cookies. more information Accept
The cookie settings on this website are set to "allow cookies" to give you the best browsing experience possible. If you continue to use this website without changing your cookie settings or you click "Accept" below then you are consenting to this.
Milf Boobs Foto
Salgado Incest Hentai
Xxx Vintage Big Ass
Real Dp Orgasm
Lesbian Video First
Access Private applications on AWS Fargate using Amazon ...
Call a microservice running on Fargate using API Gateway ...
Access Private applications on AWS Fargate using Amazon ...
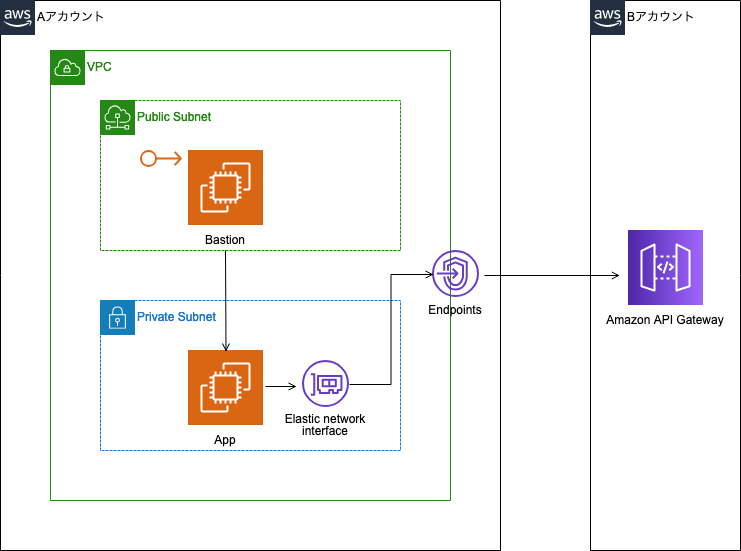
Building private cross-account APIs using Amazon API ...
Creating a private API in Amazon API Gateway
Deploy Container in ECS Fargate behind API Gateway & NLB ...
amazon web services - AWS API Gateway to Fargate, only ...
HTTP API のプライベート統合でプライベートサブネット内の …
Aws Api Gateway Private Fargate