Ansible Ssh Private Key

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
There are currently no responses for this story.
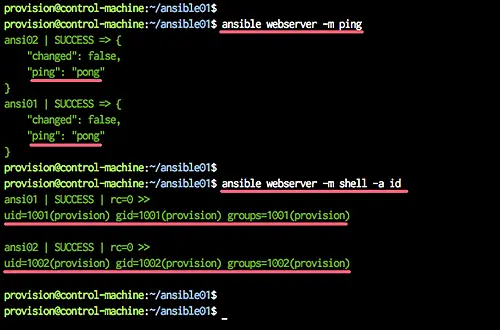
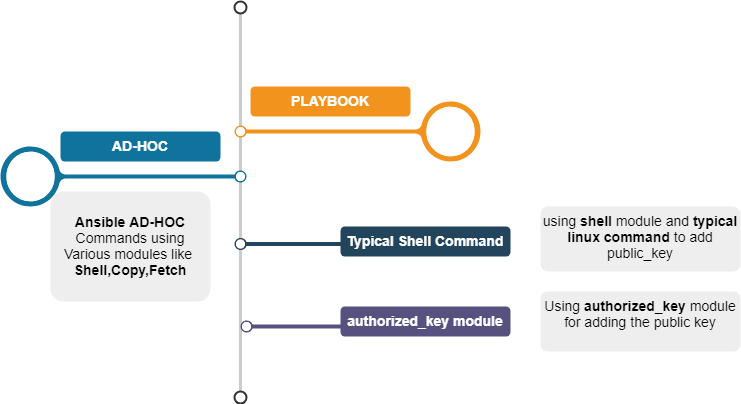
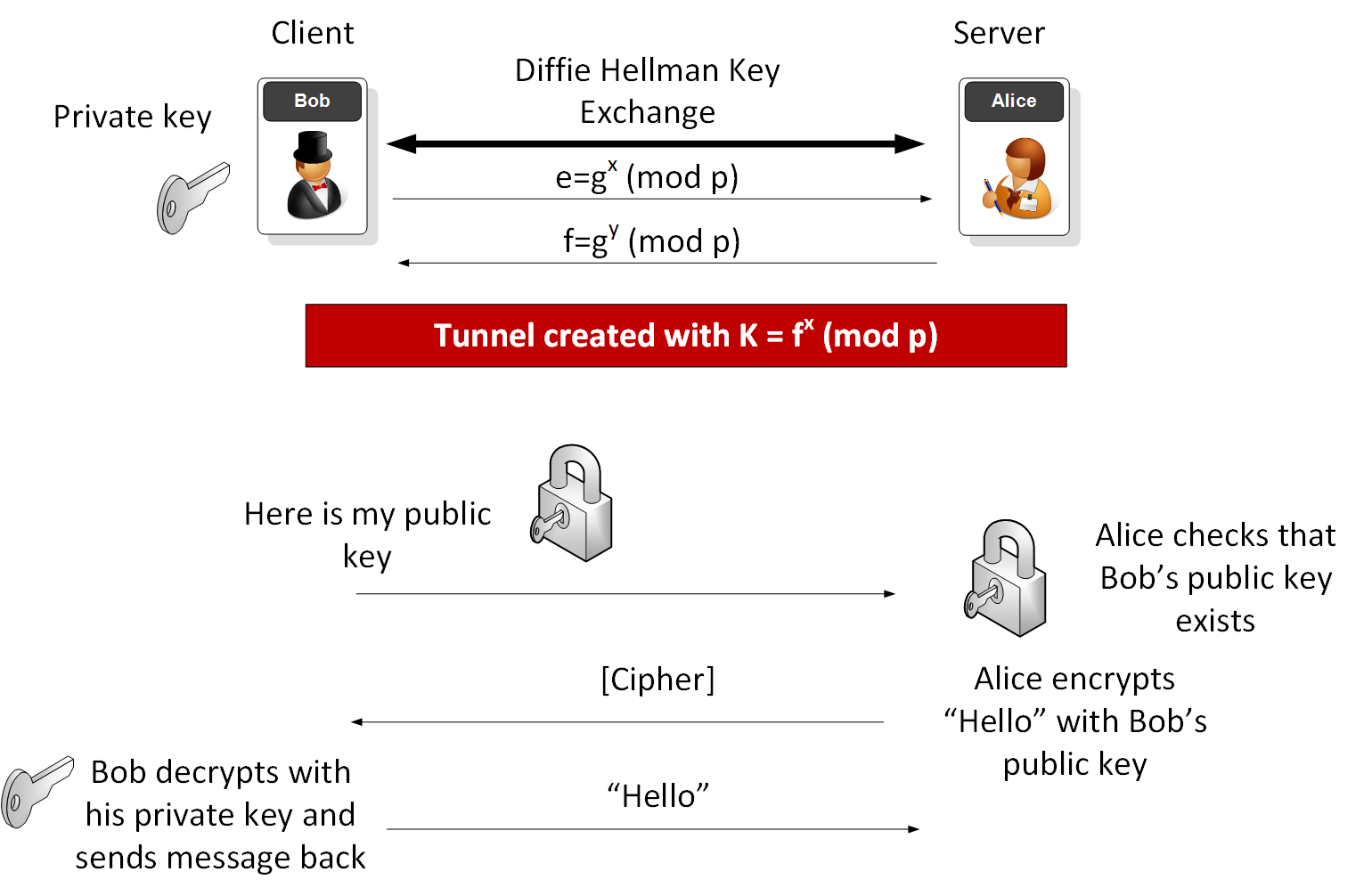
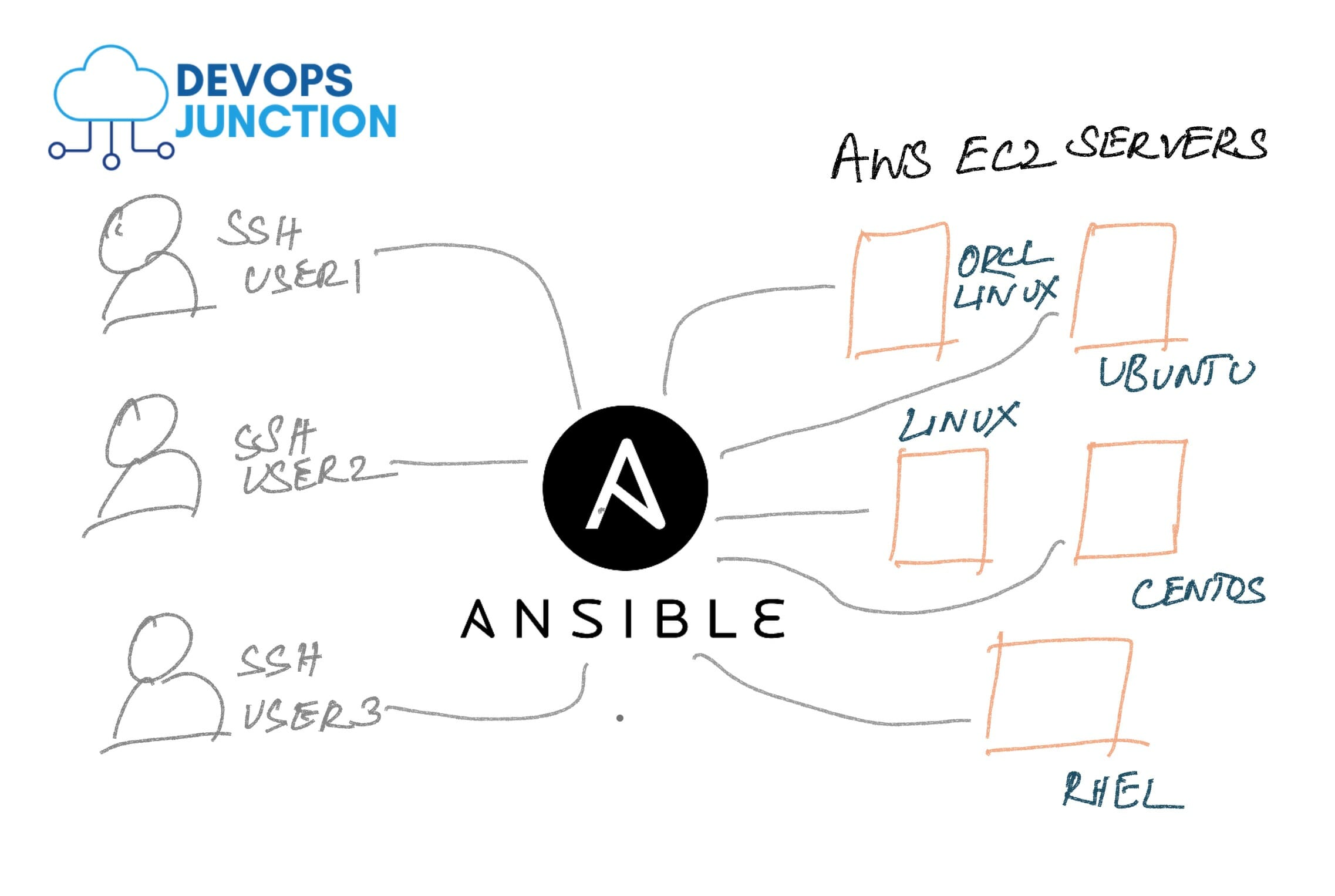
Ansible is an agentless architecture based automation tool . Only it needs ssh authentication using Ansible Control Machine private/public key pair.
Ansible Control Machine: Server where Ansible is installed.
RemoteNode: Server where we want to ssh from ansible host.
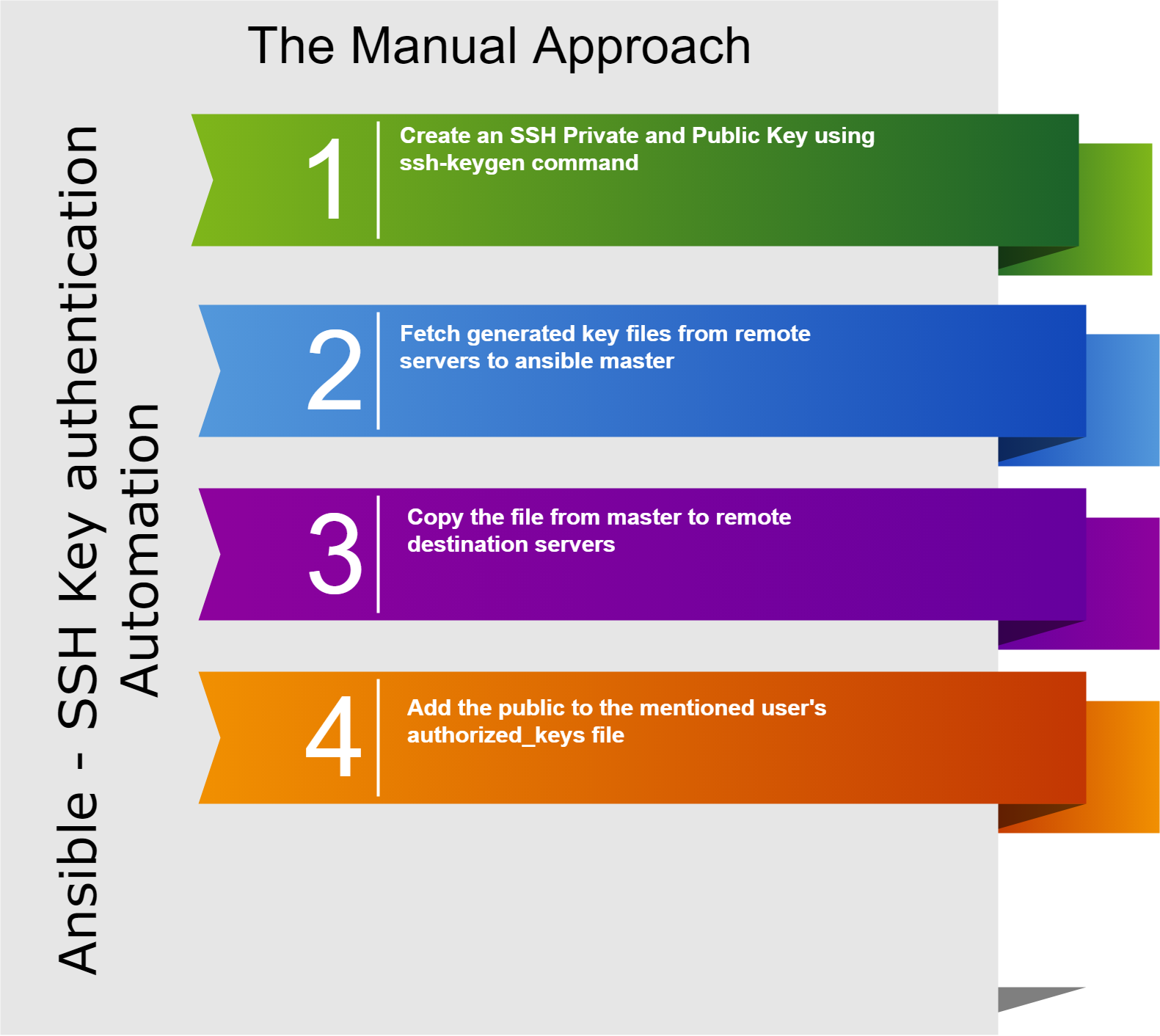
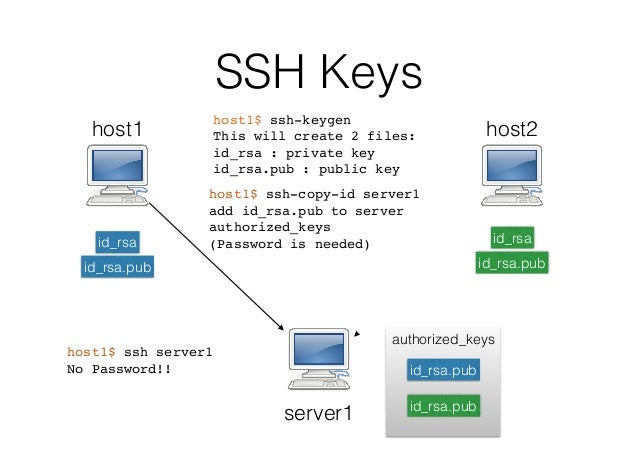
Ansible Control Machine establishes a SSH connection to Remote Node with the help of its private/public key. We need three tools to make SSH password-less connection between Ansible control Machine and Remote Node.
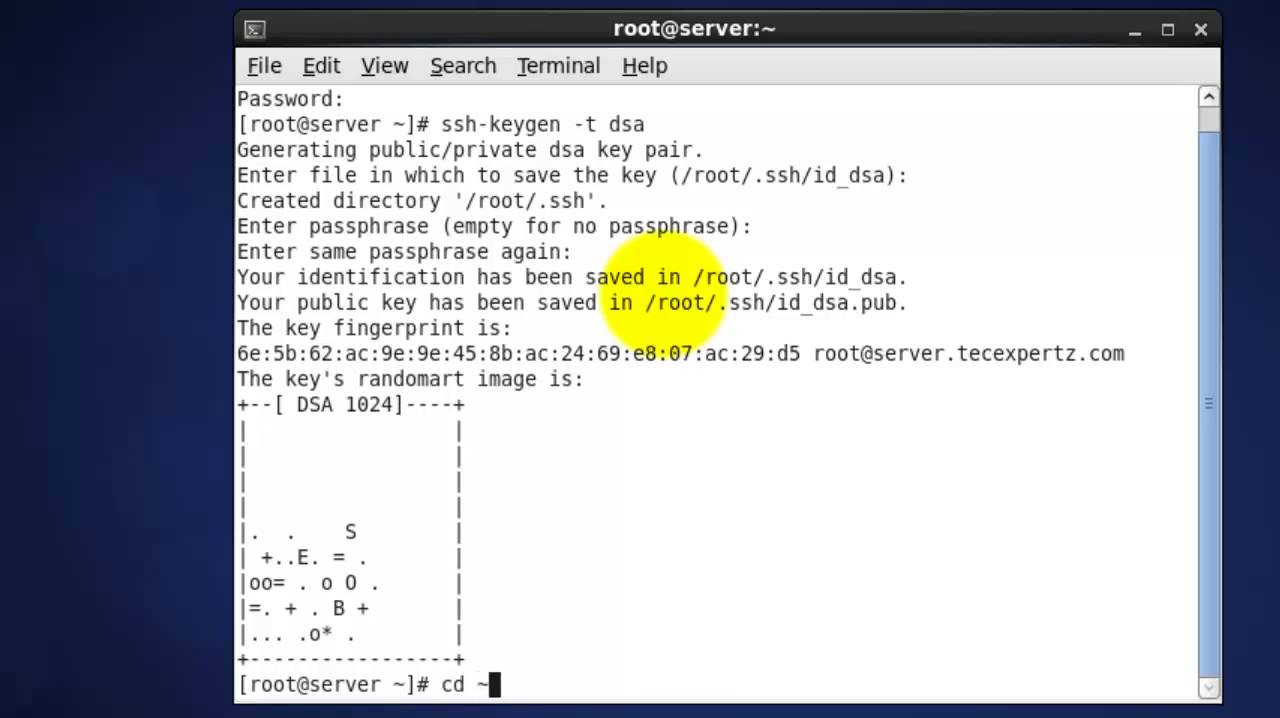
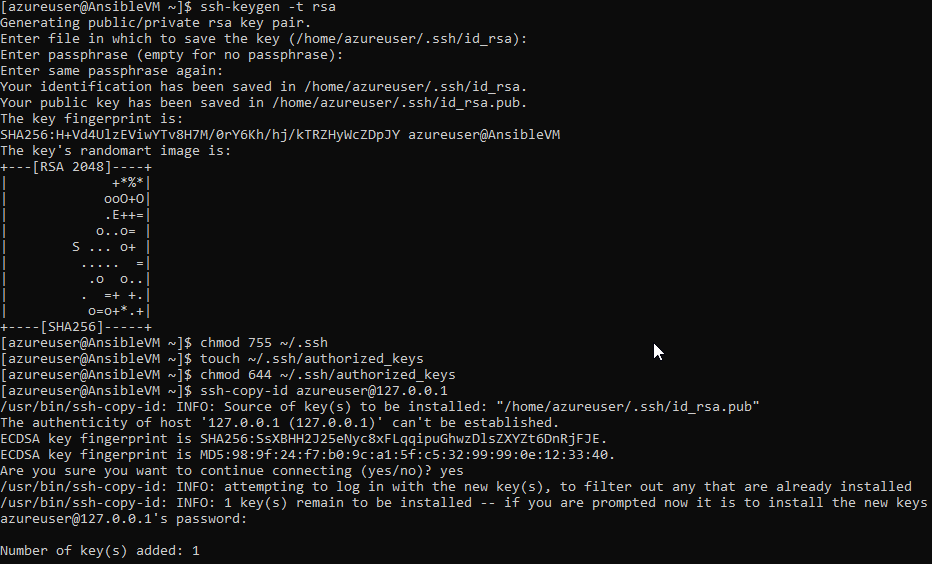
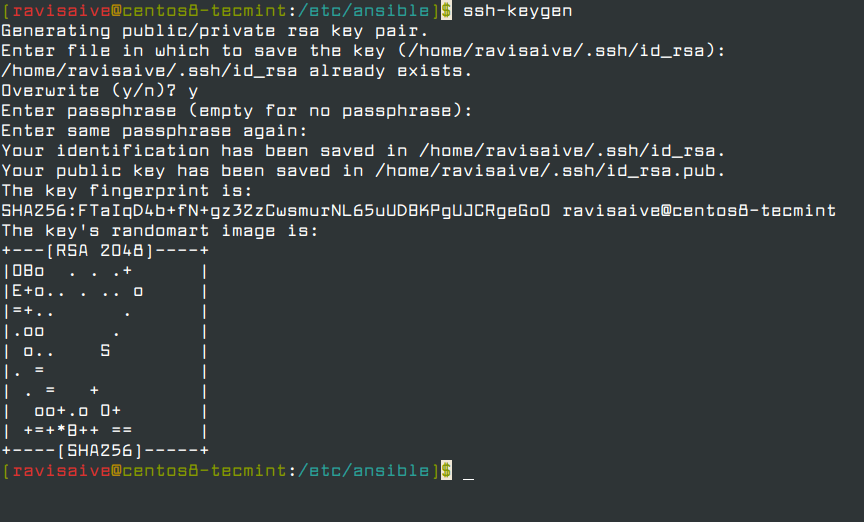
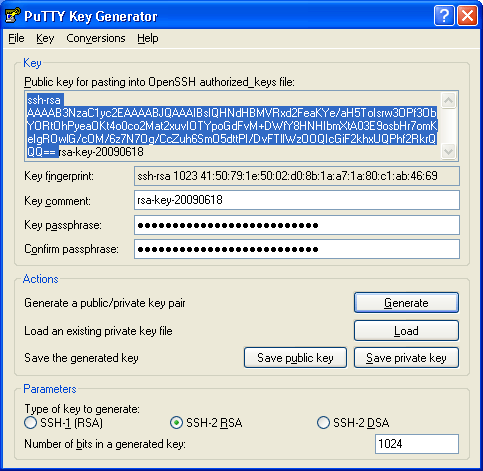
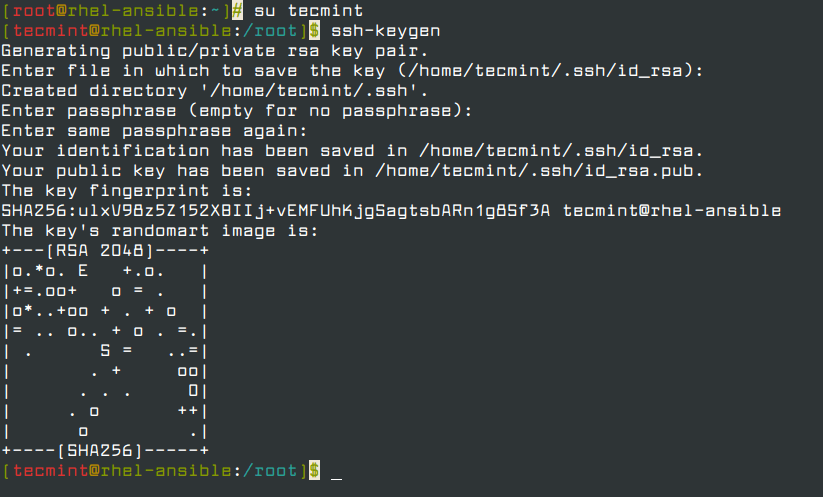
ssh-keygen tool is used to generate private/public key pair for ssh. By default, tool generates the private (id_rsa) and public (id_rsa.pub) keys in ~/.ssh/ directory. We can generate the keys using dsa algorithm as well. These key-pairs are used for password-less login, Single sign On and hosts authentication.
Deploy the ~/.ssh/id_rsa.pub key from Ansible control machine to Remote Node in a file ~/.ssh/authorized_keys. Match the contents of ~/.ssh/authorized_keys and id_rsa.pub. There should not be any difference.
Now, we are ready with SSH connection authentication. But whenever we try to connect from Ansible control machine to Remote Node, it will ask for the private key password which we have provided while generating keys using ssh-keygen. To avoid this problem we will use other two tools.
ssh-agent: It is an authentication agent which handles all the private keys password. ssh-agent command initiates a ssh agent background program which we will be used later to store private keys password.You will notice the below output on terminal. Add the output in .bash_profile to always load it automatically.
ssh-add: It is a ssh tool used to add private keys identity to authentication agent.
AnsibleControlMachine:~$ ssh-add ~/.ssh/id_rsa
Once private keys added to ssh-agent, We will be able to ssh to RemoteNode from AnsibleControlMachine without passing the password or any other key information.
It should respond with message pong.
Platform for all writers and reader who believes in quality…
Platform for all writers and reader who believes in quality content.
Platform for all writers and reader who believes in quality content.
Medium is an open platform where 170 million readers come to find insightful and dynamic thinking. Here, expert and undiscovered voices alike dive into the heart of any topic and bring new ideas to the surface. Learn more
Follow the writers, publications, and topics that matter to you, and you’ll see them on your homepage and in your inbox. Explore
If you have a story to tell, knowledge to share, or a perspective to offer — welcome home. It’s easy and free to post your thinking on any topic. Start a blog
Sign up or log in to view your list.
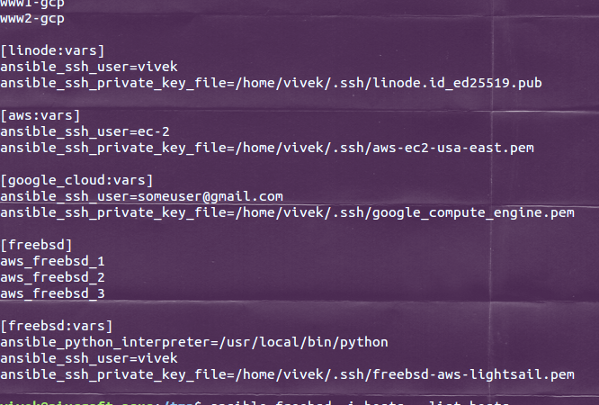
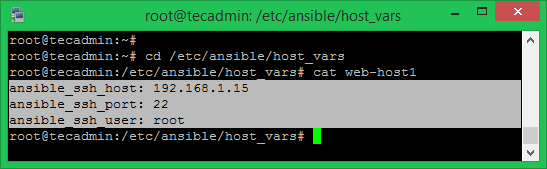
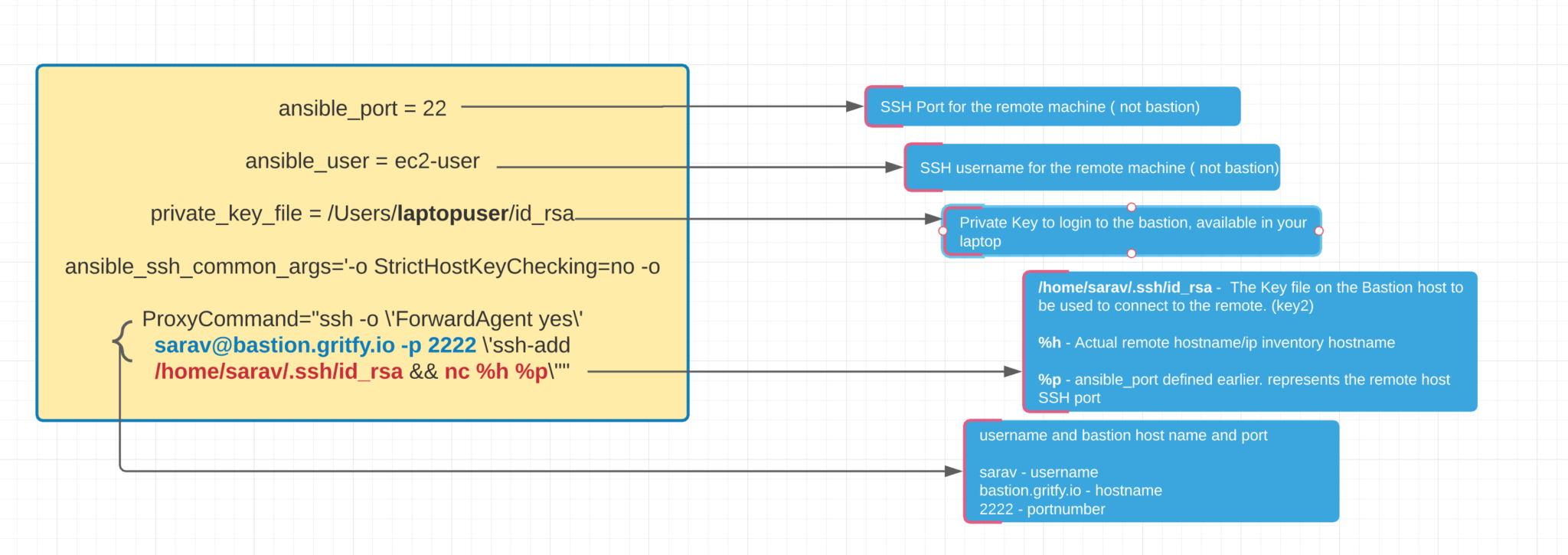
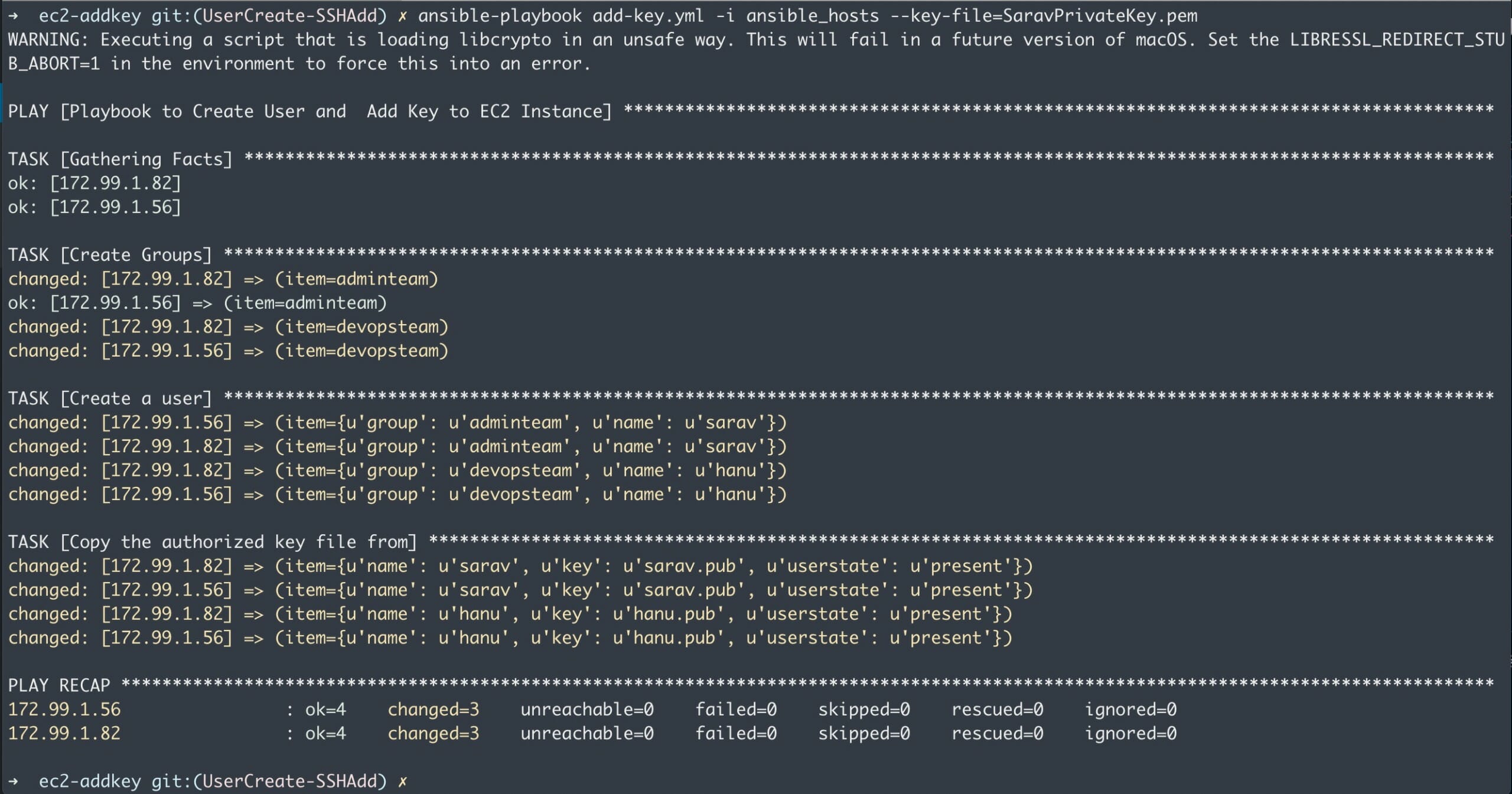
I ran into a configuration problem when coding an Ansible playbook for SSH private key files. In static Ansible inventories, I can define combinations of host servers, IP addresses, and related SSH private keys - but I have no idea how to define those with dynamic inventories.
I use the below command to call that playbook:
Clark Zheng
Clark Zheng 631●11 gold badge●55 silver badges●77 bronze badges
alex
4,843●88 gold badges●4343 silver badges●8585 bronze badges
TL;DR: Specify key file in group variable file, since 'tag_Name_server1' is a group.
Note: I'm assuming you're using the EC2 external inventory script. If you're using some other dynamic inventory approach, you might need to tweak this solution.
This is an issue I've been struggling with, on and off, for months, and I've finally found a solution, thanks to Brian Coca's suggestion here. The trick is to use Ansible's group variable mechanisms to automatically pass along the correct SSH key file for the machine you're working with.
The EC2 inventory script automatically sets up various groups that you can use to refer to hosts. You're using this in your playbook: in the first play, you're telling Ansible to apply 'role1' to the entire 'tag_Name_server1' group. We want to direct Ansible to use a specific SSH key for any host in the 'tag_Name_server1' group, which is where group variable files come in.
Assuming that your playbook is located in the 'my-playbooks' directory, create files for each group under the 'group_vars' directory:
Now, any time you refer to these groups in a playbook, Ansible will check the appropriate files, and load any variables you've defined there.
Within each group var file, we can specify the key file to use for connecting to hosts in the group:
Now, when you run your playbook, it should automatically pick up the right keys!
Using environment vars for portability
I often run playbooks on many different servers (local, remote build server, etc.), so I like to parameterize things. Rather than using a fixed path, I have an environment variable called SSH_KEYDIR that points to the directory where the SSH keys are stored.
In this case, my group vars files look like this, instead:
There's probably a bunch of neat ways this could be improved. For one thing, you still need to manually specify which key to use for each group. Since the EC2 inventory script includes details about the keypair used for each server, there's probably a way to get the key name directly from the script itself. In that case, you could supply the directory the keys are located in (as above), and have it choose the correct keys based on the inventory data.
Tiro
Tiro 1,641●1616 silver badges●1818 bronze badges
Thank you for this response. It really helped. Also, I'd like to share this: if you don't want to have to create a file in group_vars with an odd name like tag_Name_server1.yml and you happen to know that all your AWS EC2 instances might share the same SSH keys you could do something like this: ansible -i ./inventory/ec2.py --limit "tag_Name_server1" -m ping all and then just create this file: ./inventory/group_vars/all.yml . So even though you're using all the --limit option filters the number of hosts to only those with the right tag/value combination. – racl101 Jul 27 '18 at 19:18
The best solution I could find for this problem is to specify private key file in ansible.cfg (I usually keep it in the same folder as a playbook):
Though, it still sets private key globally for all hosts in playbook.
Note: You have to specify full path to the key file - ~user/.ssh/some_key_rsa silently ignored.
tchu
tchu 379●22 silver badges●66 bronze badges
Thank you tchu, that works. But it's still have some gap from my expectation, let's see whether it would get optimized in ansible 2.0+ lol – Clark Zheng Dec 21 '15 at 2:04
You can simply define the key to use directly when running the command:
kaiser
kaiser 20.1k●1616 gold badges●8383 silver badges●102102 bronze badges
I'm using the following configuration:
mangolier
mangolier 360●33 silver badges●1111 bronze badges
I had a similar issue and solved it with a patch to ec2.py and adding some configuration parameters to ec2.ini. The patch takes the value of ec2_key_name, prefixes it with the ssh_key_path, and adds the ssh_key_suffix to the end, and writes out ansible_ssh_private_key_file as this value.
The following variables have to be added to ec2.ini in a new 'ssh' section (this is optional if the defaults match your environment):
Daz
Daz 51●11 silver badge●22 bronze badges
This is really good, just what I was looking for. Did you submit a PR for this to the ansible repo? – kenske Oct 26 '17 at 17:00
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Lesbian Massage Hidden Camera
Children Nudist Videos And Photos
Model Naked Women Indonesia
Ass Is Out
Porno Cumshot Facial Photos
Define ssh key per host using ansible_ssh_private_key_file ...
How to access Ansible remote machine using SSH user and key?
ansible - Where to store private SSH keys? - Server Fault
Ansible SSH Key transfer from one host to another - local ...
Connection methods and details — Ansible Documentation
Ansible playbook文件中指定SSH密钥文件_会哭的雨@的博客-CSDN博客
ansible - Forward local ssh key to remote host - Server Fault
Allow ssh private keys to be used that are encrypted with ...
Ansible Ssh Private Key