3 Tips For Choosing The Best Access Control Software System
Tips for Hiring the Right Access Control For Parking
Table of Contents
How to Pick the Best Parking Access Control System
Tips For Choosing a Commercial Face Recognition Access Control
4 Tips for Choosing a Temperature Access Control
Find a Access Control For Parking
Top Tips for Finding the Best Access Control For Parking
Tips on Finding a Good Parking Access Control Software
How to Choose a Entry And Exit Access Control Systems
The Best Tips For Choosing Parking Access Control Systems
Subjects and items should both be thought about as software entities, rather than as human users: any human users can only have an effect on the system by means of the software entities that they control. [] Although some systems correspond topics with user IDs, so that all procedures begun by a user by default have the exact same authority, this level of control is not fine-grained sufficient to please the principle of least privilege, and perhaps is accountable for the prevalence of malware in such systems (see computer insecurity). [] In some designs, for instance the object-capability design, any software application entity can potentially serve as both subject and item. [] As of 2014, access-control models tend to fall under one of two classes: those based upon abilities and those based upon gain access to control lists (ACLs).
Both capability-based and ACL-based models have mechanisms to enable gain access to rights to be given to all members of a group of subjects (typically the group is itself modeled as a topic). Access to accounts can be implemented through lots of types of controls.
7 Tips to Find (& Hire) the Best Parking Access Control Software

(HPBAC)Access control to resources is specified in terms of presence policies that require to be satisfied by existence records stored by the requestor.

An example policy would be "The requestor has made k different visitations, all within last week, and no 2 successive visitations are apart by more than T hours." Identity-Based Gain Access To Control (IBAC)Using this network administrators can better handle activity and gain access to based on specific needs. Lattice-Based Access Control (LBAC)A lattice is utilized to specify the levels of security that an object might have which a topic might have access to.
Tips For Finding A Access Control Gate
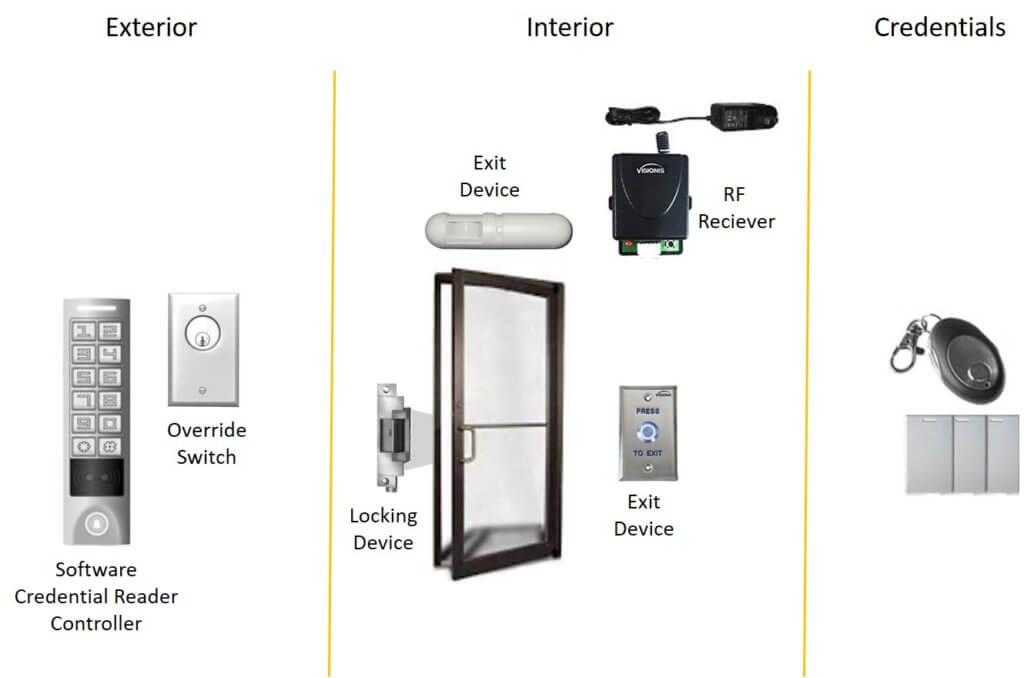
The facilities elements are the ones that depend on your building infrastructure in order to function. The most apparent parts are locks, however there are other components, such as the controller, server, and cables. Access Control Locks Electronic locks are used to electrically unlock the door on which it's installed.
Get Access Control Now - - Get Access Control System
Access Control by Fresh USA
9 Mc Gregor Ct, Hawthorn Woods, IL 60047
Click here learn more about Access Control
Some locks will lock when they are supplied with power, while others unlock when provided with power. The first ones are called fail-safe locks and the 2nd ones are understood as fail-secure. The choice of which to use depends upon the area being secured - face recognition access control. Entry doors call for reliable locks, because they need to comply with building regulations and fire policies that call for individuals to be able to exit at any time, even in case of a power failure.
How To Choose The Best Parking Access Control Software
When a legitimate credential is provided at the door reader, the panel gets its demand to open a specific relay, which is linked to the particular door wire. Gain Access To Control Server Every access control system requires a server where the consents are saved in an access database. It acts as the center, or "brain," of the access control system.
The server can be a dedicated local Windows or Linux computer system, a cloud server, and even a decentralized server (when the permissions are stored in the door reader). The server also tracks and tapes activity and events relating to access, and it allows administrators to pull reports of past information events for a given period.
4 tips on finding a good Temperature Access Control

Handling it requires the administrator to be on-site. Because having to contend with several regional servers can end up being made complex for multi-facility management, cloud-based servers are acquiring a great deal of traction in this location. Low-Voltage Cables Cables are a critical part of gain access to control and can prove to be very pricey if installed incorrectly, so they should never be neglected in planning a gain access to control system.
Access Control by Fresh USA
Address: 9 Mc Gregor Ct, Hawthorn Woods, IL 60047
Phone: +1 (312) 312-9608
Email: order@fresh222.com
Click here to learn more about Access Control
If the cables are not planned for at this moment, they will need to be included later: This suggests somebody will have to drill into, or lay cable televisions on, all the newly-painted walls. access control software.
8 Tips for Choosing the Right Vehicle Access Control Gates
A gain access to control system not only conserves time for those accessing limited areas however can also prevent check outs from the locksmith professional if secrets are lost or taken. As keys can be easily duplicated, this also adds a security issue if a worker leaves and doesn't hand the secrets back or keys are lost or taken.
Given that qualifications are needed prior to a door will open, only those with accepted gain access to qualifications can enter. With this system in location, you can rest ensured everybody in your structure is supposed to be there. Workers in some cases work various shift times; an Access Control system means they can go into whenever they require to without waiting on someone to open the doors or having a door that is always open without security procedures.
10 Steps to Choosing the Right Face Recognition Access Control
Find out more ... What are the various types of Access Control? There are 5 main various types of gain access to control: Utilizes individuals to secure particular access points, for example doormen or stewards.
This also keeps record of who has travelled through the area/ when. Utilized for single access points. Access is permitted or rejected on the basis of access permissions in your area in the standalone part. These systems are not wired, this implies setup requirements are less, this conserves time on website and permits for easy retrofitting of elements.
Finding the Best Face Recognition Access Control
Standalone elements can be integrated into larger access control systems utilizing a combination of both online and standalone elements. An examples of standalone elements consist of Digital Cylinders, Mechatronic (Electronic and Mechanical mix) Cylinders, and Electronic Door Locks. Utilized for bigger websites with high access rates, these systems are wired and connected to the host system's gain access to control software.