Singapore Research Team Codifies 3 New Ethereum VM Vulnerabilities
Smart PlanetIn a paper published on February 16th, a team of blockchain researchers from the National University of Singapore have discovered and codified a new class of smart contract vulnerabilities endemic to Ethereum Virtual Machine-based implementations of the tech.
Trace Vulnerabilities and the EVM
The paper deals with a serious type of smart contract exploit that permanently affects its function, which the researchers class as “trace vulnerabilities.” In their survey of nearly a million contracts running on the Ethereum blockchain, close to four percent of them are vulnerable to this class of exploit.
Smart contracts with trace vulnerabilities fall into three major categories according to the paper — Greedy, Prodigal, and Suicidal. All of them permanently cripple the intended behavior of their host smart contracts, but they differ in what happens to the balance on the contract when executed.
Greedy contracts lock the funds in them when exploited, prodigal contracts allow unaffiliated accounts to extract funds, and Suicidal contracts cease functioning entirely.
These Exploits Should Sound Familiar
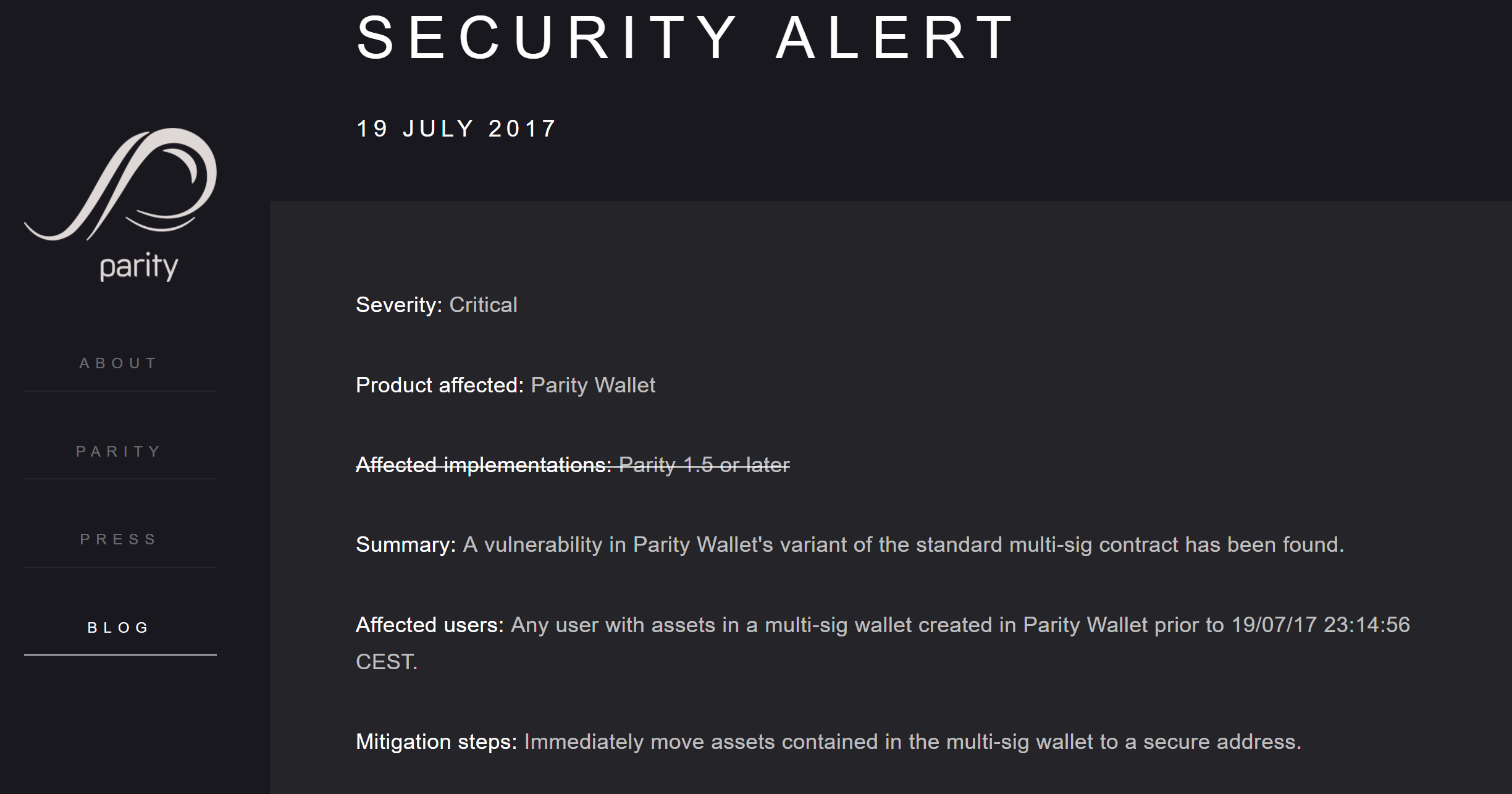
While this is the first study to codify and analyze the frequency of these exploits, examples of them have been found in the wild since the inception of Ethereum. Notably, the Parity bug that locked up $200 million USD, and the DAO implosion, which ended in a rollback and fork of the network.
At press time, three to four percent of the smart contracts on Ethereum’s blockchain still contain trace vulnerabilities, according to the researchers’ new analysis methodology.
This rate may sound small, but value is stored directly on many of these contracts, which is a massive incentive to find and exploit that fraction. Because smart contracts can’t be updated, and the value on the Ethereum network being what it is, another massive theft or disruption could be just around the corner.
Opacity Is Hampering Ethereum Security
Another interesting point raised in the paper is the unavailability of smart contract source code for Ethereum smart contracts, estimating the number at only one percent of the 970 thousand contracts they analyzed.
Fixing serious security vulnerabilities at scale requires peer review, and the culture of propriety on the Ethereum network forced the research team to directly analyze EVM bytecode instead of the sources to complete their research. Were the source code for these contracts more available and reviewed, Trace Vulnerabilities on Ethereum may not have proliferated in the first place.