Dark web
Telegram Technical UniversityTelegram : @tele_university
Dark Web | Beginner to advanced

Contents
1 What is Dark Web
2 Deep Web vs Dark Web
3 Deep Web Levels
4 How to access dark web safely
5 The Dark Web Isn’t Just for Criminals
6 Surfing the Dark Web Isn’t Illegal, but It Can be Dangerous
7 Is the Tor Browser Completely Anonymous?
8 Criminal Cases Involving the Dark Web
9 Dark Web Search Engines
10 Required tools for accesing dark web
11 SOME DARK WEB LINKS (upated july 2020)
12. Movies and series related to darkWeb
" It is extremely easy to access the dark web and even easier to be detected on it if you don’t take precautions. If you are new to the darknet, this guide will help you on your way. "
1 . What is Dark Web
The Dark Web, or Darknet, is a general term for a collection of websites on an encrypted network with hidden IP addresses – all of which gives users strong anonymity protection . Because they are not indexed by traditional search engines, you can only access them with special anonymity browsers, such as I2P , Freenet , and the most common, The Onion Router (TOR) bundle.
2 . The Dark Web is Not the Same as the Deep Web
The Deep Web is all the sites on the web that can’t be reached with a search engine . Although this includes sites on the Dark Web, it also includes sites that serve more mundane functions, such as business intranets, webmail platforms, databases, online banking platforms, and services that usually require a password or other means of authentication.
These are found and accessed directly with a URL or IP address, and are hidden behind firewalls, paywalls and HTML forms. Because all these other pages are included in the Deep Web, the Deep Web is actually far more vast than the regular internet (also known as the Clear Web).
3. Deep Web Levels (full explanation)

In order to better understand the concept of Deep Web, it is necessary to look at the structure of the internet. The Internet consists of multi-level layers. Content, security and accessibility differ in each layer. It would be useful to visualize the movie Matrix in your eyes.
Level 0 (Common Web): It is the layer that makes up the internet we use daily.
Level 1 (Surface Web): LSurface Internet. To reach the internet you need to make some simple queries through the search engines. Security cameras servers, Access databases are examples. Temp mail services provide this level of service on sites that provide DNS inquiry services.
Level 2 (Bergie Web): Internet only. At this level, there are sites where search engines lock search results, FTP servers, non-indexed adult movies. You may need to make detailed queries in the search engines to reach. Many sites that enter this level are thrown to the last pages in the search results. This level is the last level you can reach in normal ways
---- Requires the use of a proxy to access the next layers. ----
Level 3 (Deep Web): Beginner Deep Web Level. Is divided into two.
1. Proxy Level: It is the level where there are any .onion sites but all kinds of illegal sites. Often they are not indexed by search engines. Many use servers. It is found in PHP coding sites. Examples of those at this level are: Illegal research results, mildly illegal adult movies, hacker groups, viruses, script threats, celebrity scandals, VIP rumors, computer security related issues, assassination videos, etc. These contents are generally hosted on illegal forum-style sites
---- It requires the use of tor to access the next layers .----
2. TOR Level: .onion is the level at which sites are involved. The sites are generally on personal servers. To give an example to those at this level: ELIZA data, hacked servers information, data traders, secret government documents, wikileaks documents, spies selling state secrets, terrorist organizations, bomb and weapon training, federal information, intelligence secrets, illegal scientific research, scientists, shell network, assembly programmers, real hackers, microsoft confidential network information, security and data analysts etc. These contents are generally hosted on html coding sites and personal servers. Server owners can do anything to protect their servers.
Level 4 (Charter Web): Exclusive Deep Web Level. It is not easy to reach this level, but if you can reach it, there will be little things that will return to you. Is divided into two.
1. TOR Level: It is the level that can be reached only by using Tor browser without doing anything additional. At this level; secret company and market information, predefined million betting results, bilion dollar sales, world-famous weapon smugglers, tank-missile-defense system sales, banned movies - videos - books - music, government spies on top positions, important sound recordings, mercenaries soldiers, mercenary armies, mercenary special teams, black boxes, excessively illegal and forbidden adult content, sex tapes of government officials, detailed secret wiki encyclopedias, human trafficking, drug trafficking, trade of prohibited chemicals and drugs, trade of blood kidnapped from blood banks, child ** There are things like ***, vampires' search for people to kill, search for human subjects for illegal experiments, snipers, mafia, pedopholies. General of this level consists of .onion sites. It is from dangerous levels.
---- After that, closed access is required. ----
2. Special Access Level: It is the level that can not be controlled absolutely. It is the most dangerous level ever achieved. Tor browsers are insufficient for you to reach. There is a special method of reaching called "Closed Shell System". If we want to give an example of what is at this level: AI measurement machines, AI processors, GGGEQP processors, Tesla's plans, crystalline power controllers, weather-changing devices, hidden HAARP projects, the location of Atlantis, and hidden research about Atlantis. detailed locations of the location, plans of custom-made engines, those who do not accept God and their proofs, masons, illuminati, secret algorithms and calculations, global terror network, global murder network, global drug network, global human trafficking network, supercomputers and artificial intelligence etc. etc. Scientists make up the entire category. All of the sites are on personal servers or private servers. There are proven experiments that will change the world when applied at this level. Normal computers and internet networks may be insufficient to reach.
The levels described so far constitute 80% of Deep Web. So what's the remaining 20%?
---- From here on, devices that use Quantum technology and the Internet are required. ----
Level 5 (Marianas Web): We don't know much about this level. Because it has not been reached yet. The technology we use now is insufficient to reach this level. We need computers and the internet that work with quantum technology. It is one of the most dangerous levels known. It takes its name from the deepest hole in the world, Mariana Trench. The limits of the level are uncertain, but it has an end. It is known that the sites in it can change the world. For this level, it is said that “If it is reached one day, the war on the internet will end”. Many scientists in high-tech R&D laboratories are said to have reached this level and shared information. It has been stated by some scientific circles that the information contained here has the power to change the life of the whole world and to dominate the world. Some states and hacker groups are also said to have access to these systems, but there is no information on this. According to reports leaked from some scientific circles, nuclear missiles around the world can be operated with the information here. It is alleged that intelligence agencies offer jobs to hackers here to destroy nuclear systems.
Level 6: It is the most dangerous level known. There is no information about. Its borders are uncertain and its end is uncertain. It has not been able to access even with the most advanced technology.
Level 7 (The Fog / Virus Soup): The 7th level is called the war zone. If one day can be reached, everyone will fight for themselves. The aim is to prevent other people from reaching level 8.
Level 8 (The Primarch System): Level 8 is not directly accessible. It is controlled by a Primarch System that neither a government or organization nor anyone knows exactly. This system was first discovered by chance in the 2000s. The system sends random commands that are unresponsive and cannot be changed across the internet. Level 8 uses "level 17 quantum t.r.001 level function lock", which is a huge processing power that today's computers cannot handle. Finally, level 8 is referred to as the "Last Boss of the Internet".
4. How to Access the Dark Web Safely
The main gateway to the Dark Web is the Tor browser. This is an encrypted network of volunteer relays around the world through which users’ internet connections are routed.
Although the relays are an integral part of what makes Tor anonymous, they can also lead to slow connections . This is because rather than connecting directly to the server of the website you want to get to, you first have to go through the relays, which are often purposely scattered around the globe. Also, since the system is decentralized, not all the relays have the same CPU, meaning that while some are fast and powerful, others might operate at a snail’s pace.
The easiest way to browse web pages is to download and install the Tor browser bundle. Tor URLs end in the suffix .onion . Unlike .com websites, the URLs are usually complex and difficult to remember, and websites will often change their URLs in order to evade detection and DDoS attacks.
When you’re on the Dark Web, ISPs – and by extension, the government – might not be able to view your activity, but they will know you are on the Tor Network. This alone is enough to raise eyebrows in some countries.
That’s why we recommend accessing Tor using a VPN. That way, your internet traffic is routed through the VPN before going through the Tor Network and finally reaching its destination. With this method, your ISP only sees the encrypted VPN traffic, and won’t know you’re on the Tor network .
The major concern with using Tor over a VPN is that it requires you to trust your VPN provider, as the provider may see that you are using Tor. To mitigate this issue, use a VPN that does not log your activities, and connect to your VPN before opening the Tor browser .
Use These Steps as a Guide
Step 1. Get yourself a good VPN service
That means one that doesn’t keep logs, has no DNS leaks, is fast, is compatible with Tor, and which (preferably) accepts Bitcoin as payment.
We recommend Nordvpn or Express VPN as the best VPN available on the market with its amazing features and military grade encryption.
Step 2: Download and install the Tor browser bundle
Before you do though, check that your VPN is running . Also be sure to download Tor from the official Tor project website. 86
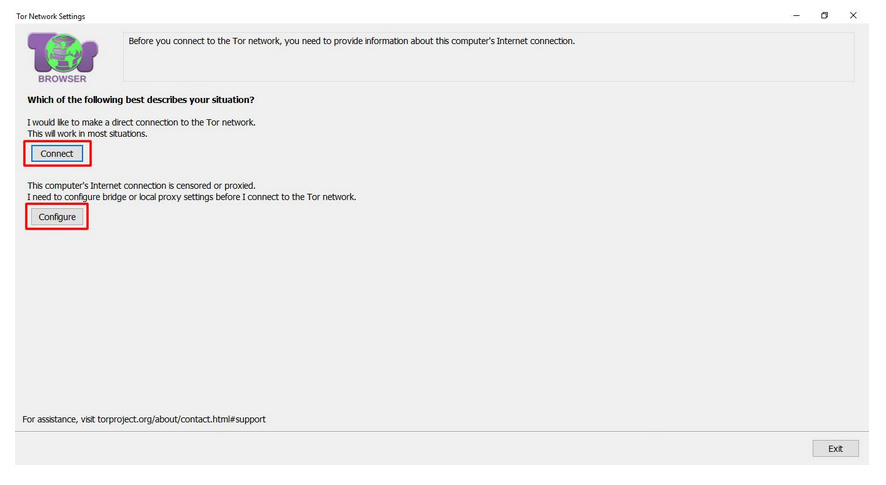
Once it’s installed, look for the Tor Browser folder and click on the “Start Tor Browser” file inside it.
A new window will open asking you to either click on the “Connect” or “Configure” button. Click on the “Connect” option to open the browser window.
Step 3. Start browsing .onion websites
When you open Tor on your computer, you’ll automatically be directed to the search engine DuckDuckGo. While DuckDuckGo is designed to provide extra privacy and encryption while searching the web, you shouldn’t think of it as the dark web version of Google.
That’s because even in Tor, DuckDuckGo searches the clear web . That means if you do a keyword search, you’re results are going to be basically the same as what you would find on the regular internet.
Fortunately, there are Dark Web search engines (mentioned in the end) that will bring you to .onion sites . These include:
- Welcome to Dark Web Links (http://bznjtqphs2lp4xdd.onion/ )
- Candle (http://gjobqjj7wyczbqie.onion/ )
- not Evil (http://hss3uro2hsxfogfq.onion/ )
Just make sure to always turn on your VPN before opening Tor and starting a web surfing session.
5 . The Dark Web Isn’t Just for Criminals
The anonymity provided by the Dark Web is certainly attractive to those looking to buy or sell illegal goods such as drugs, weapons, or stolen data.
But there are also legitimate reasons for using the Dark Web. In past years it has gained popularity as a safe haven for whistleblowers, activists, journalists , and others who need to share sensitive information, but can’t do so out in the open for fear of political persecution or retribution by their government or other powerful actors.
Police and intelligence agencies also use it to monitor terror groups and keep tabs on cybercriminals . Additionally, corporate IT departments frequently crawl the Dark Web in search of stolen data and compromised accounts, and individuals may use it to look for signs of identity theft.
In many circles, the Dark Web has become synonymous with internet freedom , especially as nation states continue to clamp down on it. It now plays host to a number of media organizations involved in investigative journalism, such as ProPublica and the Intercept . Most notably, WikiLeaks – the website that publishes classified official materials – also has a home on the Dark Web. Even Facebook maintains a presence there in order to make itself accessible in countries where it is censored by the government.
6. Surfing the Dark Web Isn’t Illegal, but It Can be Dangerous
You can’t be charged with a criminal offense for simply searching the Dark Web, but you can get in trouble for using it to carry out illegal activity ; headlines about police operations that involved the Dark Web and child pornography, drugs, or hackers dumping stolen data are not infrequent.
Moreover, the anonymity of the Dark Web also makes it notoriously risky. Since there’s no oversight, it’s teeming with scammers. That said, one can maintain one’s safety by simply following the same basic security rules that apply to the normal web: Always be careful about the links you click because some can be misleading, and avoid sites or links that advertise illegal, disturbing, or dangerous content you don’t want to see.
7. Is the Tor Browser Completely Anonymous?
In 2014 the FBI – with assistance from researchers at Carnegie Mellon University – developed an exploit based on a Firefox JavaScript flaw that successfully de-anonymized some Tor users, including the operators of the popular Silk Road website. Although the vulnerability that allowed those attacks was fixed within days of its discovery, the incident nonetheless created fear among Tor users that it may not be 100% secure after all .
Similarly, in October 2017 the security firm We Are Segment identified a vulnerability in Tor that was affecting some Mac and Linux users. This vulnerability, which became known as TorMoil, caused IP addresses to be leaked when users accessed URLs that began with file://, rather than http:// or https://. We Are Segment notified the Tor developers, who promptly fixed the error by updating to a new version of the web browser.
In order to address these issues, the Tor Project has recently improved security and privacy by strengthening its encryption . It also gives web developers the tools to build fully anonymous Darknet sites (known as hidden services, or rendezvous points) that can only be discovered by those who know the site’s URL.
8 . Criminal Cases Involving the Dark Web
Although we believe the Dark Web should be used for promoting free speech and bypassing censorship, there’s no denying that the press tends to focus on the more shady activity that goes on there. Here are some of the most high profile stories that have come out in recent years:
- Silk Road: Perhaps more than any other website, the Dark Web brings to mind Silk Road. Silk Road began as the invention of a libertarian idealist who wanted to sell home-grown mushrooms for Bitcoin, and ended up hosting 1.2 billion dollars worth of deals involving drugs, firearms, hits, counterfeit cash, and hacker tools.Five of the hits were commissioned by the site’s creator, Ross Ulbricht, known on Silk Road as the Dread Pirate Roberts. Ulricht was ultimately caught because of an old post to a regular website in which he promoted Silk Road in its early days. His mistake: using his real email address.
- AlphaBay: Following the shuttering of Silk Road, AlphaBay became the most prominent Dark Web marketplace. When AlphaBay went down in 2017, it was because of security missteps even more basic than those of the Dread Pirate Roberts.Among other blunders, founder Alexandre Cazes used his legitimate email address for communications on the site (pimp_alex_91@hotmail.com), kept several unencrypted cryptocurrency wallets constantly open, and re-used the same pseudonym on and off the Dark Web. And when the cops busted into his home in Thailand to arrest him, he was logged onto the AlphaBay server with the username “admin.”The computer was unlocked and unencrypted, and contained text files of passwords used on the site, as well as a document listing the type and location of all his financial holdings that was titled in bold “TOTAL NET WORTH.” Several days after his arrest, Alex Cazes was found dead in his prison cell, apparently having committed suicide.
- The Playpen Case: Although it only existed for seven months, the child pornography site Playpen managed to amass 215,000 users before the FBI gained access to its host server via information provided by a foreign law enforcement agency (which has not been publicly identified).Instead of just shutting the site down, the FBI continued to host it on its own servers for two weeks, during which it used a Flash app to capture 1,300 IP addresses belonging to site visitors. This led to the arrest of nearly 900 users around the globe, including Playpen’s creator, Steven Chase (may he burn in hell).
- The Ashley Madison Case: In 2015, the hacker group, the Impact Team, breached a dating site for extramarital affairs called Ashley Madison. The hackers threatened to release users’ personal information unless the website and its sister site, Established Men, were shut down. A month later, when their deadline wasn’t met, the Impact Team started publishing data on the Dark Web.Over the course of several dumps, information was revealed that included the email and IP addresses of 32 million members, the email correspondences of the CEO of Ashley Madison’s parent company, and the website’s source code.The hacker’s stated motivation was 1) an objection to the site’s primary purpose, and 2) the site’s practice of forcing users to pay to delete their accounts (which were even then not fully scrubbed from the servers).Because Ashley Madison didn’t require email verification to create a profile, it would have been easy to create accounts using someone else’s email address, and then use this to extort them. Although we still don’t know who was responsible for the attack, one can speculate that they were someone affected by these poor security practices.
Bonus Security Steps For the Dark Web
DO NOT change the TOR browser window size unless you like living dangerously. The FEDS have programs that can match identities on random things such and matching time online and other things with the browser window size, I shit you not. If you don’t change the size then it is the same as most other people.
You MUST use a VPN whenever you are connected to the TOR Network
Please remember that TOR isn’t necessarily 100% anonymous, you should turn off JavaScript within the dark web browser settings to help. See our privacy and information tools for additional tricks.
Disconnect your webcam or block the camera with some black tape. Hackers and governments have ways of getting into your computer and turning on the video and cameras. You can have intimate images of you be used as blackmail or extortion, or even worse, used by the feds.
Disconnect your microphone or cover it with tape to muffle it good. The same goes for the microphone as the camera, the last thing you want is to be recorded saying incriminating things at home. It doesn’t even have to be while on the dark net. Even the Facebook creator Mark Zuckerberg does it as he knows the dangers.
NEVER use your real name, photos, email, or even password that you have used before on the dark web. This is the fastest way to be tracked. Use an anonymous email 23 account / secure messaging apps 10 and aliases that have nothing to do with you that you have never used before.
If you are using TOR on the dark web for anything other than looking at cute pictures of kittens, you should think seriously about your privacy and security.
On a final note, we encourage everyone who uses the Dark Web to do so responsibly. Stay SAFE and make sure your VPN is connected!
9 . Dark Web Search Engines
- Pipl
- MyLife
- Yippy
- SurfWax
- Torch
- Google Scholar
- DuckDuckGo
- Fazzle
- Not Evil
- Start Page
- Wayback machine
- Candle
- Ahmia Deep Web Search Engine
- Searx Search Engine
Darknet Markets
- Agartha Market
- Apollon Market
- Berlusconi Market
- Cryptonia Market
- Empire Market
- Genesis Market
- Nightmare Market
- Tochka Market
- Yellow Brick Market
(Simply Google Them)
10 . Required tools for accesing dark web
1. Cleanup Computer
You can use Windows or Linux to connect to the Dark Web.
Clear cache, trackers, cookies, viruses and adware that’s currently on your machine with the following tools.
Cleanup Tools (Removes cache, history, cookies etc)
Remove Malware, PUP’s and Adware
- Malwarebytes & Adwcleaner (Windows)
- ClamAV , Lynis & RKhunter (Linux)
Run windows/linux commands to verify and repair integrity of system files
- sfc /scannow for Windows (Run command prompt as administrator)
- debsums for Linux (To install “apt install debsums” and then execute program “debsums -s”)
After all scans completed, reboot your system and continue with step 2 (#Install Tools)
2. Install Tools
Must Have Tools
- Get a VPN
- Download the latest TOR Browser
- Install browser extensions and maximize browser security
- Change your DNS manually using uncensored DNS IP
Additional/Optional Anonymity Tools for more security
3. Create Fake Identity
If you’ll be using any services on the dark web then you definately will need to create a fake identity that has nothing in common with your real life.
The below services are for anyone that wants to protect their online identity.
Before Signing up with the below free services, make sure you are connected to your VPNand TOR browser 86 already.
Keep in mind that every time you create an account on any website or login to a service, your public IP have already been logged. > Go back to step 1 to clean and clear your machine. Then connect to your VPN and TOR to create your fake online identity with the below services.
Name Profile Generator
Encrypted Email Services
Encrypted Messaging Apps
Encryption Tools
- Smartninja – Online PGP Tool
- CyberChef – Web App Encryption Tool
- Kleopatra with GPG4win
- Veracrypt
Ready for Action > After you completed all the steps you are now ready to wander around the dark web.
11 . SOME DARK WEB LINKS (upated july 2020)

Dark web link collections: http://onionlinksv3zit3.onion/ OnionLinks v3
http://hiddenwikiwpn2ed.onion/ The Hidden Wiki
http://wikikijoy3lk2anu.onion/ Another Hidden Wiki
http://thedarkwebpugv5m.onion/ Pug's Ultimate Dark Web Guide
Commercial links:
http://ziagmjbpt47drkrk.onion/ Dark Web Hackers for hire
http://accsaphx55wcxaxd.onion/ AccMarket - Premium Paypal, Ebay and bank accounts
http://cardsa2u7pvmdamw.onion/ Cardshop - USA CVV KNOWN BALANCE & Worldwide CC & CVV
http://dcukmmtrhqouetep.onion/ DCdutchconnectionUK - The dutch connection for the UK
http://docchrstunztkk7c.onion/ DrChronic - Weed straight from the source
http://tandj5f5zdzkm5hl.onion/ TomAndJerry - Cocaine, Heroin, MDMA and LSD from NL
http://primelpds4neewmw.onion/ 420prime - Cannabis in dispensary quality from the UK
http://mixerpkpxev6qruk.onion/ Dark Mixer - Anonymous bitcoin mixer
http://freshbowfjqvyrxm.onion/ VirginBitcoins - Buy freshly mined clean bitcoins
http://mixbitw5m5zh4m7u.onion/ Mixabit - Bitcoin mixer
http://miningbf34ktfupa.onion/ Darkmining - Bitcoin mining with stolen electricity
http://invest775zkbmhiy.onion/ Bitcoin Investment Trust - earn 5-9% per week!
http://ybiaxhp2mhn4dtog.onion/ Mobile Store - Best unlocked cell phones vendor
http://4t2qo5bgrwicvqw7.onion/ Kamagra 4 Bitcoin - Like Viagra but cheaper
http://c6qolqd4nuvdymhn.onion/ Bitpharma - Biggest european .onion drug store
http://xnwpwzm5dn5fi6kf.onion/ EuCanna - First Class Cannabis
http://tugvveav653hfqig.onion/ TorShops - Create your own .onion store
http://d6d6qr5r5jurtvjh.onion/ Smokeables - Finest organic cannabis from the USA
http://kkf7wy3uu7kgbaa6.onion/ OnionIdentityServices - Fake passports and ID cards for bitcoin
http://yibhdid4wssp4rly.onion/ Uk Guns and Ammo Store
http://efby23qxgt6rb6vc.onion/ CannabisUK - UK wholesale cannabis supplier
http://t4wjrh634dnlue6i.onion/ USfakeIDs - US fake ID store
http://hntpud2v7otxphgf.onion/ Counterfeit USD - High Quality USD counterfeits
http://sbqaxe6dwiydetyr.onion/ Onionwallet - Anonymous and secure bitcoin wallet and mixer
http://tcc26dp2rs6g3v6c.onion/ USAcitizenship - become a citizen of the USA
http://3pdx7y4r2mc3zuxw.onion/ Brainmagic - Best Darkweb psychedelics
http://dunl4qc7zlaqmavm.onion/ NLGrowers - Coffee Shop grade Cannabis from the Netherlands
http://wi3dg355dpiy2g5k.onion/ EasyCoin - Bitcoin Wallet and Mixer
http://qbbiczdj4ldi2ovt.onion/ EuroGuns
http://v5dbacb4vw3cxtzp.onion/ Apples4Bitcoin - Iphones, Ipads and more for bitcoin
http://2junuwyqfrfgtlfn.onion/ Peoples Drug Store - The Darkwebs best Drug supplier!
http://zlvpbozpgrq7uwqc.onion/ UKpassports - real UK passports
http://55bk7hkfqlyo2xg3.onion/ ccPal - PayPals, Ebays, CCs and more
http://bbk7vwlok5a3eika.onion/ DeDope - German Weed Store
http://tsyyky3oc7fngj5l.onion/ Rent-A-Hacker - Hire a hacker for Bitcoin
http://egixqvttogpxc75f.onion/ Webuybitcoins - Sell your Bitcoins for Cash, Paypal, WU etc
http://q3xlqv65nhypm6tn.onion/ HQER - High Quality Euro bill counterfeits
Non-commercial links:
http://tinhat233xymse34.onion/ The Tin Hat
http://pastgoldwshgmey2.onion/ Opsec by Example
http://autinv5q6en4gpf4.onion/ autistici.org - Welcome to Autistici/Inventati
http://danschatjr7qbwip.onion/ Daniel's Chat
http://torvps7kzis5ujfz.onion/ TorVPS
http://qlast7washjzrlkn.onion/ blogthe last wash
http://suprbayoubiexnmp.onion/ Suprbay
http://cmoqohtgyilgec7y.onion/ CryptoParty Austria
http://matrixtxri745dfw.onion/neo/uploader.php Matrix Image Uploader
http://uwd57qermcote3au.onion/ Whistleblower Aid
http://xdm7flvwt3uvsrrd.onion/ Financial Times
http://danielas3rtn54uwmofdo3x2bsdifr47huasnmbgqzfrec5ubupvtpid.onion/ DanielWin
http://bocl4xqbak4xvlh4.onion/ Affenposten Secure Drop
http://dreadditevelidot.onion/ Dread
http://govanifydnjinmk2.onion/ GovanifY
http://m6su7s3ir7dxggwg.onion/ Gitea
http://mx7rwxcountermqh.onion/ Bibliomaniac
http://lxpizzamm6twgep2.onion/ linux.pizza
http://45tbhx5prlejzjgn36nqaxqb6qnm73pbohuvqkpxz2zowh57bxqawkid.onion/ Parckwart’s Website
http://7rmath4ro2of2a42.onion/ SoylentNews
http://76ssfjn22svo4vyl.onion/ /WikiLeaks
http://grrmailb3fxpjbwm.onion/ Guerrilla Mail on Tor
http://tetatl6umgbmtv27.onion/ Chat with strangers
http://sophielkpqe34cl6.onion/ Sophie says 'Hieeee!'
http://5u56fjmxu63xcmbk.onion/ Onion Search Engine
http://rvy6qmlqfstv6rlz.onion/ Chaos Computer Club Dresden
http://4qt45wbulqipigwa.onion/ Keyringer
http://5qahzzgawtqnrhux.onion/ Michael's Top Secret Page
http://paranoidlcx3y23p.onion/ Paranoid
http://gjobqjj7wyczbqie.onion/ Candle
http://psycnets7z6tvqpa.onion/ Psycho Social Network
http://n7kr26tlb545urpo.onion/ help/I2P Anonymous Webserver
http://ic6au7wa3f6naxjq.onion/ The GNU Privacy Guard
http://tigas3l7uusztiqu.onion/ Mike Tigas
http://genotypeinczgrxr.onion/ Libgen
http://wey6jcnmsy3au67k.onion/ ComputerComputer Science Libary _science/
https://kcmykvkkt3umiyx4xouu3sjo6odz3rolqphy2i2bbdan33g3zrjfjgqd.onion/ aboutMastodon
http://lain666n2yf5gnqgxk3uyqlceyt77uqcyjga5iz7owkildqlfezhypad.onion/ hidden links
http://pronoiacj777ssnk.onion/ Pronoia.onion/ site
http://sejnfjrq6szgca7v.onion/ Debian
http://hor6372x6soyyts2.onion/ Heidenwut
http://nzxj65x32vh2fkhk.onion/ stronghold
http://pyl7a4ccwgpxm6rd.onion/ Code:Green
http://torbox37t3335ws6.onion/ The Tor Mail Box
http://expressobutiolem.onion/ ExpressVPN
http://zsolxunfmbfuq7wf.onion/ rc/riseup mail
http://344c6kbnjnljjzlz.onion/ VFEmail
http://hackcanl2o4lvmnv.onion/ blackcrawl/index.htmlBlack Crawling Systems Archives
http://pyfsu7ywsnuvke3r.onion/ Deutsche Forengemeinschaft
http://protonirockerxow.onion/ Protonmail
http://servnetshsztndci.onion/ ServNet
http://qubesos4rrrrz6n4.onion/ Qubes OS
http://searchb5a7tmimez.onion/ searx
http://archivecrfip2lpi.onion/ Internet Archive
https://blockchainbdgpzk.onion/ blockchain.info's onion
http://vipq5vnfvlxb3x32.onion/ g/ternet/ Wiki
http://qj3m7wxqk4pfqwob.onion/ MadIRC
http://vb75uj2ap3hyyava.onion/ Hacking is Art
http://jdpskjmgy6kk4urv.onion/ Welcome to Dark Web Links and More!
http://raphivebfpstxbsh.onion/ Raphive
http://deepdot35wvmeyd5.onion/ Deepdotweb
http://6zc6sejeho3fwrd4.onion/ OnionMail
http://cockmailwwfvrtqj.onion/ Cock.li
http://fncuwbiisyh6ak3i.onion/ Keybase
http://www.facebookcorewwwi.onion/ Facebook
http://ou63pmih66umazou.onion/ git@vger.kernel.org mailing list mirror
http://grrmailb3fxpjbwm.onion/ GuerillaMail
http://deepdot35wvmeyd5.onion/ Deep Dot Web
https://bfnews3u2ox4m4ty.onion/ BuzzFeed
http://opalrwf4mzmlfmag.onion/ opal hart / wowaname
http://cstorm5dztz7vgmvo.onion/ cryptostorm's community forum - cryptostorm forum
http://cyruservvvklto2l.onion/ Main Page | Cyrus's Blog
https://ssd.eff.org/Self-defense Surveillance Guide
http://iamevilxxoolf3ma.onion/ The Evil Page
http://clgs64523yi2bkhz.onion/ Mailpile
http://mail2tor2zyjdctd.onion/ Mail2Tor
http://bitmailendavkbec.onion/ Bitmessage
http://eludemaillhqfkh5.onion/ Elude.in
http://tef2eqrvzibdywyc.onion/ Hi
http://hor6372x6soyyts2.onion/ Heidenwut
http://zgeajoabenj2nac6k5cei5qy62iu5yun5gm2vjnxy65r3p3amzykwxqd.onion/ Darkweb Blog
http://lfbg75wjgi4nzdio.onion/ Raddle
http://elfq2qefxx6dv3vy.onion/ fakeid.phpFake Identify Generator
http://ybti.cheettyiapsyciew.onion/ youbroketheinternet
http://dds6qkxpwdeubwucdiaord2xgbbeyds25rbsgr73tbfpqpt4a6vjwsyd.onion/ Whonix
http://zerobinqmdqd236y.onion/ ZeroBin
http://expyuzz4wqqyqhjn.onion/ The Tor Project
http://y5fmhyqdr6r7ddws.onion/ Anarplex
http://enotegggr635n4lw.onion/ Burn Notes
http://hashcrack25qkmjy.onion/ Crack MD5 Hash
http://5xgrs443ogbyfoh2.onion/ torservers.net - Tor Exit Node & Bridge hosting
http://mrlevrrir47hvei5.onion/ MrLevRocks
http://znig4bc5rlwyj4mz.onion/ Expose Facts
http://milkwxjpscr54dlm.onion/ the nimbus nursery
http://gnjtzu5c2lv4zasv.onion/ PGP Public Key Server
http://ozmh2zkwx5cjuzopui64csb5ertcooi5vya6c2gm4e3vcvf2c2qvjiyd.onion/ riseup searx
http://qkndirty6fifcrdk.onion/ Name generator
http://jld3zkuo4b5mbios.onion/ All.onion/ services
http://r6rfy5zlifbsiiym.onion/ Comic Book Libary
http://ovk26br2rfr7tqr4.onion/ Riotcat.org
http://s6cco2jylmxqcdeh.onion/ Cebolla Chan
http://ctemplar42u6fulx.onion/ CTemplar
http://osiristombjn72xn.onion/ Osiris' Tomb - Home
http://t5pv5o4t6jyjilp6.onion/ Forbes
http://infantilefb6ovh4.onion/ Infantile
http://hss3uro2hsxfogfq.onion/ not Evil
http://mqqrfjmfu2i73bjq.onion/ Tor Kittenz!
http://jtbxrtnye26o4a2a.onion/ Dossier Secrets
http://bpo4ybbs2apk4sk4.onion/ en/Security in a Box
http://writeas7pm7rcdqg.onion/ write.as
http://jusfileobjorolmq.onion/ Just upload stuff
http://torchic64idgja4l.onion/ :3
http://quantum2l7xnxwtb.onion/ Quantum
http://lldan5gahapx5k7iafb3s4ikijc4ni7gx5iywdflkba5y2ezyg6sjgyd.onion/ OnionShare
http://lqdnwwwmaouokzmg.onion/ La Quadrature du Net
http://germanyruvvy2tcw.onion/ Deutschland im Deep Web
http://cathug2kyi4ilneggumrenayhuhsvrgn6qv2y47bgeet42iivkpynqad.onion/ cathugger's site
http://sik5nlgfc5qylnnsr57qrbm64zbdx6t4lreyhpon3ychmxmiem7tioad.onion/ Qubes OS
http://dhosting4xxoydyaivckq7tsmtgi4wfs3flpeyitekkmqwu4v4r46syd.onion/ Daniels Hosting
http://chchchiasaeljqgs.onion/ Chen hosting
http://gf2juatsqdph6x2h.onion/ Torum
http://3expgpdnrrzezf7r.onion/ Associated Press
12. Movies and series related to darkWeb
movies
1.Whom Am I
2.Unfriended Dark Web
series
1.Mr Robot
2.How to sell drugs online
____________________________________________________________________________
Thanks for reading
#source : Internet