QUADRANT PROTOCOL - ICO REVIEW
PENIKMATSENJA
During my younger days data collections in primitive ways are done through reading lots and bulks of books. For you to make a good research and assignments at least you have scanned and skimed in 10 books and articles, by then you will be graded “A+”.
But nowadays with the constant evolution of technology to suffice everyone thirst for information, in a single stroke of the finger- keying in topics in the most popular search engine like “Google” and voila! you have the access to the world’s enormous information consisting about zebibyte data, billions trillions of data.

The unlimited sources of data is created through billions of computer, hand held devices like tablets, and cellphones interacting together. It is rapidly growing year by year as the market also demands creation of information creator and containing gadgets.
However, the information presented in the internet especially in wikis and blogs might not all be good for you. There are lots of negative impact that might be brought by these as the internet now might not be safer as before. Viruses, identity concerns, malwares are among things we need to consider while using the internet or it will take advantage of us. Once we hit the button connecting us to the internet we are acknowledging our vulnerability to security threats that we could experience there.

Malefactors, criminals, cybercrimes have considerably grown over a period of time and they have taken advantage of the internet to do their ruthless, immoral acts. Seeing for example the incidents prevalent in many countries like using internet in broadcasting underage phornography- pedophilia.
But ofcourse behind clouds there are silver linings. So how do we lessen it? How can we filter those sites infringing our securities? How do we bar malefactors taking advantages of the internet. How do we solve underlying need to validate and verify all kinds of data?
Need for Trustworthiness

The solution is that the data needs to be filtered so that it would portrays correct, accurate as it is to be, meaning that no human and non-human intervention has purposefully altered what has been documented, for his benefits.
So, to answer such pressing problem, ITs and persons of integrity have convened on one agreed goal which is to make the internet a safe place to go for everyone whenever we need for an information exchange. Thus the QUADRANT PROTOCOL will be called into action.

Quadrant
sought to solve these problems by providing a blueprint, an internet DNA, for mapping mismatched, altered, vague, numerous data sources. It will support proof of data authenticity, veracity and provenance trough data stamping, the creation
of linkages (data smart contracts) for mismatched data sources, fair compensations and incentive sharing.
What is best about this is that the Data consumers will be ensured of the authenticity of the data that they will be purchasing. Everytime the owners’ data will be used they will be properly compensated and be given with monetary/crypto rewards; and data vendors will also be
having fair incentives to create innovative Constellations.
Furthermore this breakthrough- a new transparent ecosystem will give companies ensurance that
they are ammasing authentic data as needed.
Ideally, in the financial world, this level of authenticity is essential as data needs to be authenticated, tamper-proof and safe for use and publication.
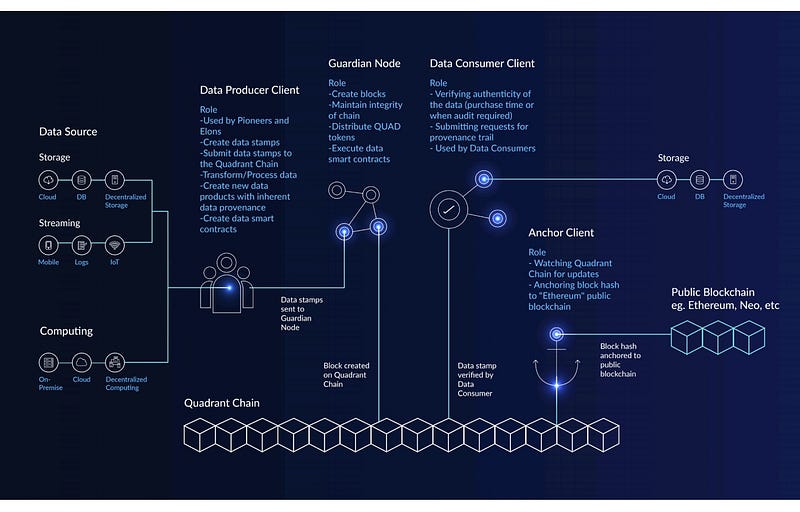
The issue of data authenticity and integrity had tremendous effects for all types of organizations that wish to adopt a cloud computing model. To solve such pressing problem Quadrant promised to adopt the following features that are aimed at helping to solve the problems ;
• Proof of Data Authenticity and Provenance

• mismatched data sources constellations

And,
• payment and Incentive Sharing given fairly

The Team Behind this Feasible Project
The following are the persons bests in their field who will work together for the project’s realization.




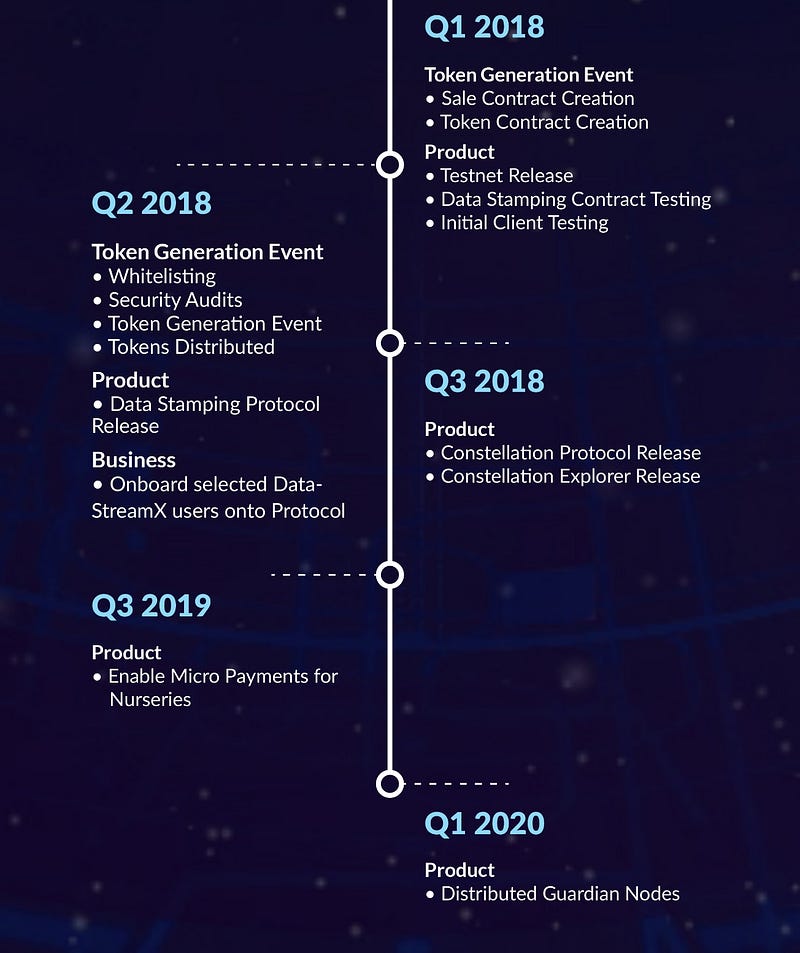
The Road Map
The diagram below shows the progress as to the where they are now towards their goals.
To know the project better. You may visit here
Website https://www.quadrantprotocol.com/
Ann thread https://bitcointalk.org/index.php?topic=3676988.0
Twitter https://twitter.com/explorequadrant
Facebookhttps://www.facebook.com/quadrantprotocol/
Telegram https://t.me/quadrantprotocol
By. penikmatsenja
Bitcointalk : https://bitcointalk.org/index.php?action=profile;u=1251309
ETH: 0x478A431b1644FdC254637d171Fa5663A739f8eF2