Набор уроков по Metasploit и Meterpreter для новичков (Eng)
https://t.me/w2hackInto
Друзья,всем привет!
Недавно мы начали серию уроков по Metasploit Framework для новичков. И пока я дописываю вторую часть на русском языке, наткнулся на небольшой мини курс Metasploit Tutorials написанный на английском. И не смог пройти мимо:) Так что, сегодня в материале делюсь ссылками на этот туториал.

Подборка уроков
И так, начинаем! Ниже приведено ссылки и краткое описание серий уроков по Metasploit!
Погнали!:)
Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview)
With this guide, I'm starting a sequential and cumulative series for learning and using Metasploit. This first part will cover the very basics of Metasploit for those of you who are new to Null Byte, and as a refresher for those of you who are not. With that in mind, this will be quick and dirty first lesson on using one of the most powerful hacking platforms on planet Earth.

Metasploit for the Aspiring Hacker, Part 2 (Keywords)
In this second tutorial, we will look at some of the basic commands we can use in Metasploit. Although the Metasploit framework can appear daunting to the uninitiated, it is actually a very simply framework for system exploitation. If you can learn a few keywords and techniques, you can use Metasploit to hack just about any system.

Metasploit for the Aspiring Hacker, Part 3 (Payloads)
Metasploit has many types of payloads we can leave on the target system. We are most familiar with the generic/shell/reverse_tcp and the windows/meterpreter/reverse_tcp payloads, having used those in multiple hacks already. In this guide, we will look at such things as how the payloads work, how Metasploit categorizes the payloads, and what the types of payloads are. I hope this understanding will help you to better choose the appropriate payload for your hack.
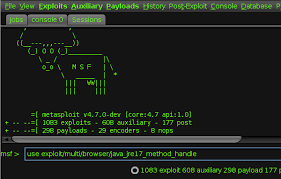
Metasploit for the Aspiring Hacker, Part 4 (Armitage)
For those who are more comfortable using a graphical user interface (GUI), Raphael Mudge has developed one that connects to and controls Metasploit much like a Windows application. He calls it Armitage, and I've covered it briefly in my Metasploit primer guide. Especially for new, aspiring hackers, Armitage can make learning hacking with Metasploit a quicker and much less painful process.

Metasploit for the Aspiring Hacker, Part 5 (Msfvenom)
Previously, to re-encode a payload in Metasploit, you had to pipe msfpayload through the msfencode command as shown in this tutorial. Recently, Rapid7, the developers of Metasploit, introduced a new command that takes the place of the clunky combination of msfpayload and msfencode to streamline the process of re-encoding a Metasploit payload. Let's take a look at it in this guide.

Metasploit for the Aspiring Hacker, Part 6 (Gaining Access to Tokens)
In this tutorial, we will use Metasploit and the Meterpreter to grab an authenticated user's token. There is a script in Metasploit named "Incognito" that is capable of grabbing tokens and impersonating them. This script was first developed by security researchers independent of Metasploit, but was then integrated into our beloved Metasploit Framework and is available to anyone using this powerful tool.

Metasploit for the Aspiring Hacker, Part 7 (Autopwn)
In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.
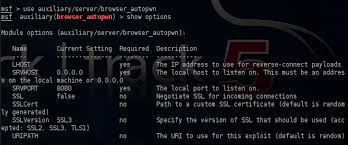
In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.
Metasploit for the Aspiring Hacker, Part 9 (How to Install New Modules)
In this tutorial, we will look at how to insert a module into Metasploit. In this case, we will be inserting an exploit module that has never been included in the Metasploit Framework, but is available from multiple sources.

Metasploit for the Aspiring Hacker, Part 10 (Finding Deleted Webpages)
In this tutorial, I want to explore and illuminate one of the auxiliary modules that can make hacking with Metasploit much more effective and efficient.

Metasploit for the Aspiring Hacker, Part 11 (Post-Exploitation with Mimikatz)
In this tutorial, we will be using the Metasploit module which is a bit limited in its capabilities, but I promise to do a tutorial soon on the more powerful standalone tool.

Metasploit for the Aspiring Hacker, Part 12 (Web Delivery for Linux or Mac)
In this tutorial, we will exploit a Linux or Mac system. Since both are UNIX-like systems, they both have built-in Python interpreters by default. If we can get the script command generated by this exploit on the target, we can have complete control of the system including keystroke logging, turning on the webcam, recording from the microphone, and reading or deleting any files on the system.

Metasploit for the Aspiring Hacker, Part 13 (Web Delivery for Windows)
In this tutorial, we will use Metasploit's web delivery exploit to take control of a Windows system through its PowerShell.

Metasploit for the Aspiring Hacker, Part 14 (Creating Resource Script Files)
Many times, when doing a pentest/hack, we need to run a number of Metasploit commands repeatedly. These commands may be exactly the same each time, and just like scripting, we may need to automatically run multiple Metasploit commands in a single step. Metasploit has the capability to save and store these "scripts," and they can then be recalled by the script name. Metasploit calls these scripts resource files.

Additional Info
А вот немного шпаргалок и чит-листов по командам (CLI) и встроенным в фреймворк скриптам для пайлода Meterpreter
The Ultimate Command Cheat Sheet for Metasploit's Meterpreter
With the meterpreter on the target system, you have nearly total command of the victim!
The Ultimate List of Hacking Scripts for Metasploit's Meterpreter
In this post, I will try to provide you the most complete list and description available anywhere on the web. You will want to bookmark this page too, as no one remembers all these scripts and it's likely you will want to return here at a later time to find a particular script for a particular hack.
На этом сегодня все! Читай, юазай, делай лабы и оттачивай навыки на стендах.
И конечно же следи на новостями на нашем канале @w2hack