Master Private Key 1113

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
Система испарительного охлаждения для промышленных, коммерческих и спортивных помещений.
Для улучшения микроклимата в производственных помещениях, как правило, необходимо обеспечить высокую кратность воздухобменна с подачей в помещения свежего и чистого (очищенного) воздуха, по возможности охлаждённого. Для больших промышленных предприятий с большой кратностью воздухообмена применение классических систем охлаждения с холодильными машинами (чиллеры, компрессорно-конденсатные блоки) обуславливает экстремальные энергозатраты. Для таких объектов превосходное решение – испарительные охладители, которые на основе природного принципа охлаждают воздух с минимальными капитальными и эксплуатационными затратами; уличный воздух подаётся в помещение через специальные влажные фильтры. Часть воды испаряется, одновременно охлаждая воздух подаваемый в помещение. Фундаментальным преимуществом этой системы является то, что эффективность охлаждения растет с ростом температуры окружающей среды. Обеспечивается разница температур 4-5 оС которая является оптимальной для человека.
Испарительные охладители обеспечивают помещения свежим, охлажденным, увлажненным и очищенным воздухом, при этом через открытые окна, двери или вытяжные вентиляторы удаляются избыток тепла, дыма, неприятных запахов.
Электронная система управления контролирует все процессы, связанные с работой охладителя, что гарантирует оптимальное функционирование оборудования в разных условиях в течении суток. При значительной внешней влажности (от 70 %, утром, вечером и ночью) охладители работают только на вентиляцию помещения, высокая кратность воздухообмена обеспечивает эффект охлаждения сама по себе. Только в тропических регионах встречается влажность выше 60 % в течении рабочего дня (с 11 до 16 часов), в период наибольшей температуры воздуха в течении суток, когда охлаждение действительно необходимо.
Тип файла: document
Размер: 52.00 Kb
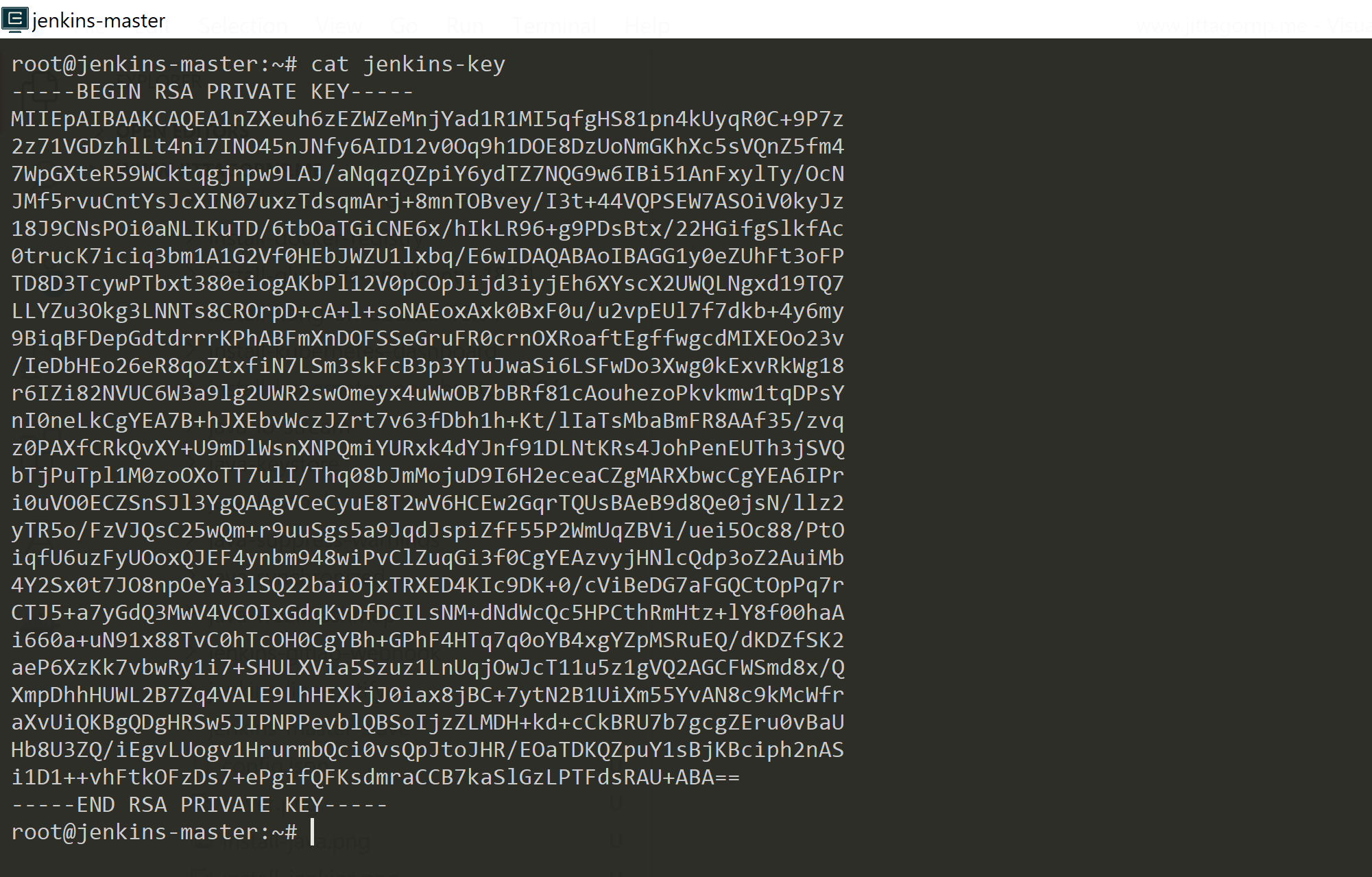
Private keys and public keys that you can derive children from.
An extended key is a private key or public key that you can use to derive new keys in a hierarchical deterministic wallet.
Therefore, you can have a single extended private key, and use it as the source for all the child private keys and public keys in your wallet. In addition, a corresponding extended public key will generate the same child public keys.
Your first extended keys (master keys) are created by putting a seed through the HMAC-SHA512 hash function.
You can think of a HMAC as a hash function that allows you to pass data along with in an additional secret key to produce a new set of random bytes.
The HMAC function returns 64 bytes of data (which is totally unpredictable). We split this in to two halves to create our master extended private key:
The chain code is required for generating child keys. If you got hold of the private key but not the chain code, you wouldn’t be able to derive the descendant keys (thereby protecting them).
So an extended private key is ultimately just a normal private key coupled with a chain code.
We can also create a corresponding extended public key. This just involves taking the private key and calculating its corresponding public key, and coupling that with the same chain code.
And there we have our initial master extended private key and master extended public key.
Tip: As you can see, extended keys are nothing special in themselves; they are just a set of normal keys that share the same chain code (an extra 32 bytes of entropy). The real magic of extended keys is how we generate their children.
All extended keys can derive child extended keys.
Each child also has an index number (up to 2**32).
For security, you can derive two types of children from an extended private key:
In other words, a hardened child gives you the option of creating a “secret” or “internal” public key, as the extended public key cannot derive them.
Both extended private keys and extended public keys can derive children, each with their own unique index number.
There are 3 methods for deriving child keys:
Tip: Derived child extended keys (and parent keys) are independent of each other. In other words, you wouldn’t know that two public keys in an extended tree are connected in any way.
The new chain code is the last 32 bytes of the result from the HMAC. This is just a unique set of bytes that we can use for the new chain code.
The new private key is the first 32 bytes of the result from the HMAC added to the original private key. This essentially just takes the original private key and increases it by a random 32-byte number. We modulus the new private key by the order of the curve to keep the new private key within the valid range of numbers for the elliptic curve.
So in summary, we use the data inside the parent extended private key (public key+index, chain code) and put it through the HMAC function to produce some new random bytes. We use these new random bytes to construct the next private key from the old one.
The new chain code is the last 32 bytes of the result from the HMAC.
The new private key is the first 32 bytes of the result from the HMAC added to the original private key. This again just takes the original private key and increases it by a random 32-byte number.
However, this hardened child key was constructed by putting the private key in to the HMAC function (which an extended public key does not have access to), which means that child extended private keys derived in this way will have a public key that cannot be derived by a corresponding extended public key.
Hardened derivation should be the default unless there is a good reason why you need to be able to generate public keys without access to the private key. – Pieter Wuille2
The new chain code is the last 32 bytes of the result from the HMAC. This will be the same chain code as the normal child extended private key above, because if you look back you will see that we put the same inputs in to the HMAC function.
The new public key is the original public key point added to the first 32 bytes of the result of the HMAC as a point on the curve (multiply by the generator to get this as a pont).
So in summary, we put the same data and key in to the HMAC function as we did when generating the child extended private key. We can then work out the child public key via elliptic curve point addition with the same first 32 bytes of the HMAC result (which means it corresponds to the private key in the child extended private key).
In other words, how is it possible that a public key derived from an extended public key corresponds to a private key derived from an extended private key?
Well, for both child extended keys, we are putting the same inputs in the HMAC function, so we’re getting the same data as a result. Using the first 32 bytes of this data (which is basically a number) we then:
And due to the way elliptic curve mathematics works, the child private key will correspond to the child public key.
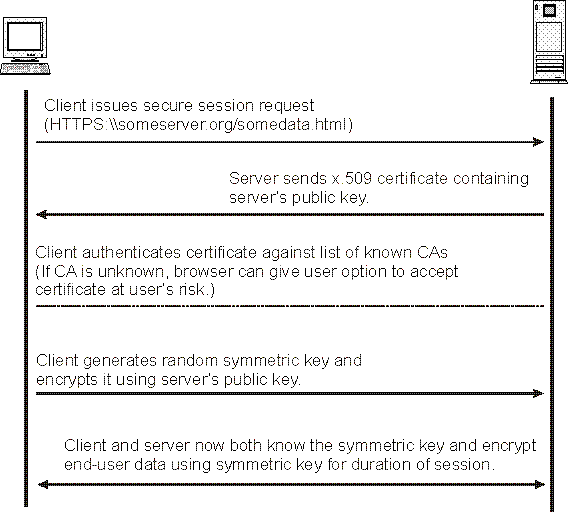
An extended key can be serialized to make it easier to pass around. This serialized data contains the private key/public key and chain code, along with some additional metadata.
A serialized key contains the following fields:
Places “xprv” 0488ade4 or “xpub” 0488b21e at the start.
How many derivations deep this extended key is from the master key.
The first 4 bytes of the hash160 of the parent’s public key. This helps to identify the parent later.
The index number of this child from the parent.
The extra 32 byte secret. This prevents others from deriving child keys without it.
The private key (prepend 0x00) or public key.
A checksum is then added to this data (to help detect errors), before finally converting everything to Base58 (to create a human-friendly extended key format).
An extended private key looks like this:
An extended public key looks like this:
As you can see they’re pretty long, but that’s because they contain extra useful information about the extended key.
Tip: The fingerprint, depth, and child number are not required for deriving child extended keys – they just help you to identify the current key’s parent and position in the tree.
Note: The 4-byte field for the child number is the reason why extended keys are limited to deriving children with indexes between 0 and 4,294,967,295 (0xffffffff).
The following are complete code snippets for creating, deriving, and serializing extended keys.
Killergram Pantyhose Sex
Cock Ninja Mom Son
Jav Model Porno
Pony Sex Comix
Reddit Wife Sharing
1. Master Extended Keys - learnmeabitcoin.com
FileCloud Security FAQ
c775e7b757ede630cd0aa1113bd…
BIP32/BIP39/BIP44 - Mnemonic Code
Data encryption - Octopus Deploy
Electrum misinterprets master extended key (depth 0) as ...
slips/slip-0023.md at master · ETeissonniere/slips · GitHub
Cryptographic Keys - XRPL.org
Can somebody please explain what a master public key is ...
Master Private Key 1113