Chinese 'Fireball' Malware Infects 250 Million Computers
Vishnu Pradeep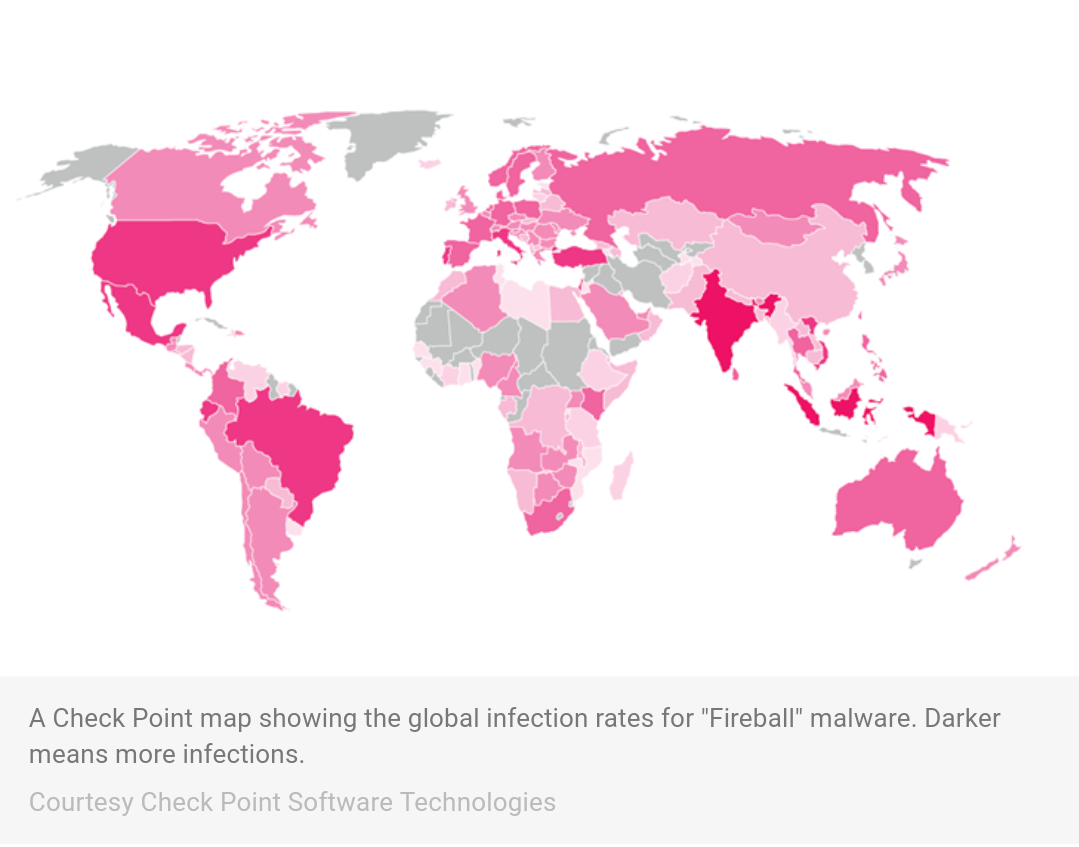
The security firm Check Point says it has found a malware infection of staggering scope and destructive potential. Originating in China, the “Fireball” malware package is believed to have infected more than 250 million computers worldwide and is present on 20% of corporate networks, with major infection centers in India, Brazil, and Mexico.
Check Point calls it “possibly the largest infection operation in history.”
The malevolent software appears to be mainly intended to generate fake clicks and traffic for its creator, a Beijing advertising firm called Rafotech. When installed, the software redirects a user’s browser to websites that mimic the look of the Google or Yahoo search homepages. The fake pages surreptitiously gather private information on the user using so-called tracking pixels.
But Fireball also has the ability to execute commands remotely—including downloading further malicious software. Fireball’s creators (or third-party hackers who find a way to take control) could theoretically transition from ad-scamming to selling harvested data, or even harness infected machines into a globe-spanning botnet of immense destructive power.
Many botnets much smaller than Fireball’s collection of 250 million compromised machines have been involved in major DDoS (for “distributed denial of service”), spam, or other campaigns. The Mirai botnet that knocked out Internet service for millions of people last December was estimated to have included as few as 120,000 devices—and those were mostly connected cameras and routers with far less power than the PCs targeted by Fireball.
According to Check Point, another scenario would simply see Rafotech mass-harvest data from infected machines and sell it—from credit card numbers to business plans and patents—to the highest bidder.
The San Carlos, Calif. security company describes Fireball as “a pesticide armed with a nuclear bomb.” Rafotech, Check Point warns, “holds the power to initiate a global catastrophe.” It adds: “The potential loss is indescribable.”
According to Check Point, the Fireball package is mostly surreptitiously inserted into free software downloads and installed without the user’s knowledge. Check Point provides a few examples of software found to contain the Fireball package, including Soso Desktop and FVP Imageviewer. The clearest sign of an infection is finding your browser has been redirected to a new homepage. Checkpoint’s post provides detailed instructions for detecting and eliminating infections.
“According to our analysis, Rafotech’s distribution methods appear to be illegitimate and don’t follow the criteria which would allow these actions to be considered naïve or legal,” Check Point writes. “The malware and the fake search engines don’t carry indicators connecting them to Rafotech, they cannot be uninstalled by an ordinary user, and they conceal their true nature.”
Rafotech’s homepage, Rafotech.com, is currently offline, but archived versions from 2016 tout the company’s ability to sell “creative ads” for website operators. The site also makes thoroughly ironic claims about a “strong anti-spamming system.”
The archived site also touts Rafotech’s role in publishing mobile apps including games like Cutie Clash and Casual Warrior. Considering recent revelations about the potential for Android apps to load malicious software onto phones, it’s worth steering clear of these and any other Rafotech products.
Rafotech’s LinkedIn page describes the company as a unit of “one of the premium publisher powering over 6 billion monthly impressions” and touts its “deep understanding of what it means to monetize more.”